Password spraying, unlike traditional brute force attacks, often stays under the radar. Instead of targeting a single account with multiple password guesses, password spraying uses a high-probability password against multiple accounts. By avoiding rapid account lockouts, this ‘low and slow’ approach allows the attack to remain undetected. It is a successful attack vector that is easy to pull off. All the hacker needs is a list of common passwords, which they can easily obtain from previous password leaks.
Password spraying attacks have very high success rates because, for any given large set of accounts, there are users with common passwords. From research conducted in 2017, the National Cyber Security Centre found that 75% of UK-based organizations had accounts with passwords featured in the most common 1000 passwords, and 87% with passwords featured in the top 10,000. These worrying statistics are clear reminders that common passwords are still a serious threat to data security today.
Find Accounts Using Compromised Passwords
The NCSC recommends regularly auditing user passwords against common password lists. By identifying common passwords in use, organizations can secure their environments and prevent a data breach. This free tool, Specops Password Auditor, scans and checks passwords of Active Directory user accounts against a list of vulnerable passwords obtained from multiple data breach leaks. With a quick scan, you can find out which accounts are using compromised passwords.
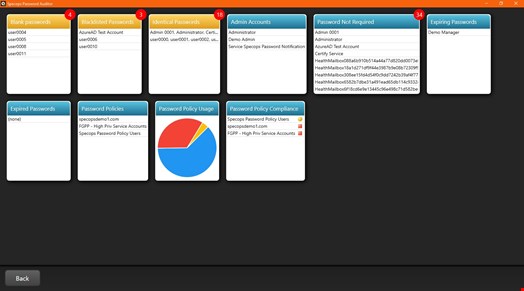
Specops Password Auditor also provides a full view of the administrator accounts in an organization’s domain. Available free reports include:
- Stale/inactive admin accounts
- Accounts with expired passwords
- Accounts with password expiration approaching
- Accounts using identical passwords
- Accounts not requiring passwords
- Accounts without a minimum password length requirement
The Most Effective Defense – Password Blacklist
Now that you’ve removed existing vulnerabilities, you will want to take steps to mitigate future attacks. The NCSC advises organizations to concentrate their efforts on technical controls that help users steer away from picking common passwords. This includes using a password blacklist. A password blacklist is a list of disallowed passwords consisting of common, and compromised passwords. To help with this effort, the NCSC also published a password blacklist of 100,000 vulnerable passwords. The list is a great start, but requires the following implementation considerations:
- What is the optimal size of your blacklist? It takes only one bad password for hackers to gain entry to corporate systems and harvest further information. Therefore, your password blacklist should be as comprehensive as possible, including all common passwords and compromised passwords, even in multiple languages. As always, you will want to consider the user experience. With a full-featured password blacklisting solution, you can relax password complexity rules knowing that you are blocking up to one billion compromised passwords
- How do you plan to update this list? The password blacklist is only effective if it is up-to-date. A third-party password blacklisting service can simplify the process of managing the list of leaked passwords. Specops Password Blacklist is influenced by major breach incidents, and updated in response to new threats
Other Defenses Against Password Spraying
The threat landscape is always evolving and ongoing efforts are required. You can protect your organization against password spraying with these additional defenses:
- Implement an effective password policy: A password policy that balances usability and security is an effective one. Specops Password Policy, offers an advanced set of password security and auditing capabilities, including finding leaked passwords and enforcing passphrases, while banning the use of predictable password patterns. The blacklisting capabilities allow organizations to relax password complexity requirements which helps improve the user experience
- User training: An educated user is a secure user. Make sure your security training program includes password training that helps users recognize common threats such as password spraying. Train your users to steer away from faulty password practices and to adopt good password habits
- Enable multi-factor authentication (MFA): MFA prevents hackers from leveraging credentials that were successfully sprayed. It is strongly recommended that organizations enable MFA for all web-based applications as well as password resets
Password spraying attacks can put your organization in serious risk, but it is preventable. Organizations must enforce technical controls such as using a password blacklist and continuously scan for compromised passwords. Implementing a password policy with blacklisting capabilities is the easiest way to achieve this without causing user frustration. It’s equally important to focus on the human factor – encourage good password hygiene with continuous training.

