Read more analysis about the NVD vulnerability backlog:
- NIST National Vulnerability Database Disruption Sees CVE Enrichment on Hold
- NIST Unveils New Consortium to Operate National Vulnerability Database
- CISA Launches Vulnrichment Program to Address NVD Challenges
A majority of currently exploited software vulnerabilities are missing from the US National Vulnerability Database (NVD), a new VulnCheck report has found.
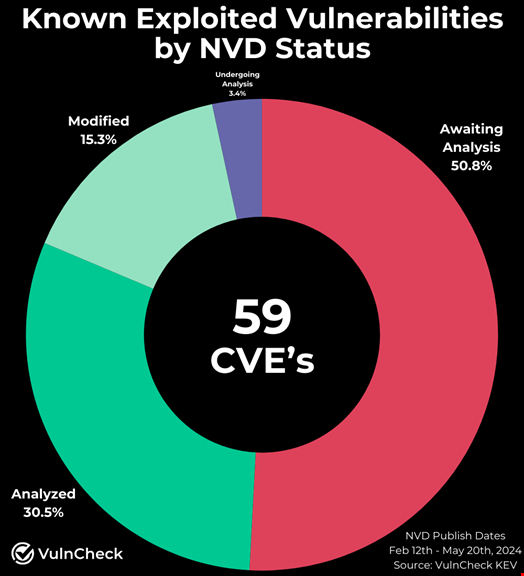
In the report published on May 23, the software security provider showed that 30 out of 59 known exploited vulnerabilities (KEVs) registered since February 12 have not yet been analyzed by the NVD team.
In total, 50.8% of KEVs are missing critical metadata.
Software vulnerabilities are added to the KEV list by the US Cybersecurity and Infrastructure Security Agency (CISA) when their analysts have confirmed they were exploited in the wild. CISA prioritizes these vulnerabilities and recommends organizations address them immediately. Inclusion in the KEV list often comes with a deadline for remediation.
VulnCheck KEVs comprise CISA KEVs and the security firm’s own account of exploited vulnerabilities.
Speaking to Infosecurity, Patrick Garrity, a vulnerability researcher at VulnCheck, said, “KEVs demonstrate the highest level of threat to an organization. The volume of missing KEVs from the NVD data highlights the trend that vulnerabilities are being weaponized and exploited faster than ever.”
Garrity led the research, utilizing data sourced from the NVD and VulnCheck’s exploit and vulnerability service.
Weaponized Vulnerabilities and Proof-of-Concept Exploits
Other findings from the VulnCheck report show that 55.9% of weaponized vulnerabilities and 82% of vulnerabilities with a proof-of-concept exploit have not been analyzed by the NVD since February 12.
Unlike KEVs, which are decided by CISA, vulnerabilities are considered ‘weaponized’ when any security researcher, threat intelligence report, or dark web monitoring report sources them as being used by cyber attackers.
According to VulnCheck, a ‘weaponized vulnerability’ is one that has either been exploited in the wild or has an available exploit capable of delivering a significant payload, that can be found on a website dedicated to vulnerability exploits (e.g. Metasploit).
Proof-of-concept (PoC) exploits are demonstrations that a specific vulnerability can be exploited. PoCs are generally published by security firms once a vulnerability has been publicly disclosed.
Almost All CVEs Missing Analysis
It has now been over 100 days since the NVD, operated by the US National Institute of Standards and Technology (NIST), started facing issues with software vulnerability enrichment.
These issues, which have not been clearly addressed by NIST or the NVD team, mean that although common vulnerabilities and exposures (CVEs) continue to be added to the NVD, many of them are missing metadata critical for patching, such as common platform enumeration (CPE) numbers, the names of software products impacted, and the vulnerability's criticality score (CVSS).
According to VulnCheck’s report, out of 12,720 new vulnerabilities added to NVD since February 12, 11,885 (93.4%) have not been analyzed or enriched.
According to its own data, NIST has analyzed only 4535 of the 16,689 CVEs received so far this year.
Read more: NIST Confusion Continues as Cyber Pros Complain CVE Uploads Stalled
“Nation-state threat actors and ransomware gangs continue to target organizations with devastating consequences, while our own house is in disarray. Although we can speculate on the underlying causes leading to the NVD's near cessation, one thing is clear: threats continue to persist and show no signs of following NIST's lead,” reads the VulnCheck report.
New Initiatives Provide Reasons For Optimism
However, VulnCheck’s Garrity shared some reasons for optimism with Infosecurity.
“Initiatives like the release of the new CVE format [version 5.1], the efforts from CVE Numbering Authorities (CNAs) to submit CPEs themselves and CISA’s new Vulnrichment program are attempting to fill the current gap NVD has left behind. This is an aspirational task.”
Although Garrity believes the CVE program, operated by MITRE and supported by CISA, could fill the NVD vulnerability analysis gaps in the longer term, some challenges would remain in the case of the closure of the NVD.
“First, NIST maintains the official CPE dictionary, so there are multiple challenges involved with this function moving away from NIST’s hands. Second, there is also the current challenge of pulling this information from multiple data sources. Consolidation across these programs would help consumers,” he concluded.
The VulnCheck research focused on new CVEs published by NVD between February 12 and May 20. A similar report on the analysis of zero-day vulnerabilities missing from the NVD is expected to be published soon.
