
You wouldn’t think that the head of product marketing at a well-known cybersecurity product vendor would fall victim to identity theft, but Fred Kost of Check Point is as susceptible as everyone else. Three months and $20,000 later, he is just beginning to recover. Ironically, the firewall products that his company makes wouldn’t have helped him, because the identity thieves didn’t go anywhere near a computer network to steal his credentials.
“I was convinced that it was an electronic breach, until I realized how much information they had”, says Kost, who shreds all of his personal documents.
He began to suspect that the data theft was not electronic at all, but may have involved the pilfering of physical data, because of the sophistication of the ID theft attack. This wasn’t just a case of stolen passwords. The thieves had opened accounts at several large electronics retailers, and were also cashing checks in his name. They were using credit cards and driver’s licenses bearing his information. But how did they get it all?
A Paper-based Problem
Overall, ID fraud figures have been volatile over the last few years. Javelin Research, which monitors US identity fraud statistics, found that the number of Americans affected by ID fraud dropped considerably throughout the last decade until spiking again between 2007 and 2009. It then plummeted once more to 2007 levels in 2010.
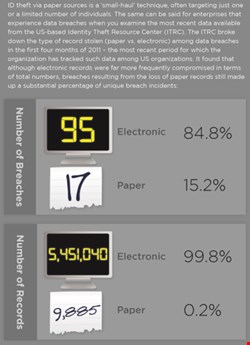
It is now on the rise again, with 4.9% of US residents affected by ID fraud in some way in 2011. Javelin argues that the users of social media sites – and mobile device users – are particularly susceptible to fraud. Others argue, however, that traditional paper-based fraud is still a big challenge, both in the enterprise and personal realms.
“It’s a big problem because a lot of organizations focus almost entirely on electronic data”, says Larry Ponemon, founder of the Ponemon Institute, which researches organizational security posture and data breaches. “All that other information in printed form doesn’t get the attention of security people anymore. It’s a sleeping giant.”
This is particularly problematic because criminals will often find it easier to dumpster dive around an office than mount an electronic attack. “We know for a fact that a lot of bad guys are not super-smart”, Ponemon relays.
Unfortunately, businesses seem unprepared to defend against traditional, paper-based theft. Physical breaches are relatively easy to engineer. Inside actors can include disgruntled employees – or third-party contractors such as cleaners – and paper-based documents can often be improperly secured. “There’s a huge amount of damage that can be done by having access to paper documents and files, and a lot of companies don’t have good hygiene”, Ponemon warns.
Ponemon routinely asks corporate security practitioners to rate their own security posture, and gets anecdotal evidence that they don’t protect physical documents. Quantitative data bears this out. “Companies are far more likely to rate their paper security at the C level or below, while their other security is rated at a far higher level”, he says.
Junkie Heaven
Fred Cates, director of the Center for Applied Cybersecurity Research and Institute for Information Policy Research at Indiana University, also suggests that traditional fraud is a significant threat to consumers, based on Javelin Research figures. Where consumers were aware of how they were defrauded, 9% of the crimes were committed by someone who the victim already knew. “These people aren’t coming down in some sophisticated technological way”, he insists. “They’re picking up stuff from your bedroom, checks from your home office, or preapproved credit offers. Not just by dumpster diving, but looking in your own trash can.”
John Sileo, an identity theft consultant who works with clients including the FDIC and the Federal Reserve Bank in the US, believes that the people behind traditional ID fraud are often markedly different than those behind internet-based ID theft. “I think it’s the local crack addict meth ring, rather than the organized crime types, that only need one identity”, he observes.
| "All that other information in printed form doesn’t get the attention of security people anymore. It’s a sleeping giant" |
| Larry Ponemon, Ponemon Institute |
Neal O’Farrell, executive director of the Identity Theft Council based in California, also identifies a link between drug-dealer culture and the theft of physical documents for ID fraud purposes. “In California, the major meth cartels were swapping meth for personal information”, he explains. “They knew that the junkies and street-level users could steal that kind of information.” He says that there was a rise in such activity when pseudoephedrine (an active ingredient in crystal methamphetamine) became more heavily regulated at both federal and state levels, because many meth users found it harder to cook their own drugs at home, instead having to bargain with dealers.
Unfortunately for the average American, criminals don’t need much to mount a basic identity theft attack. Typically, ID fraud breaks down into two main types: account takeover, and unauthorized account creation – both of which happened to Check Point’s Fred Kost. These things can be executed using information intended for the rightful owner that is intercepted by a bad actor.
“It’s the paper that is ultimately in the hands of people, that causes new account fraud or account takeover”, says Robert Siciliano, an expert in ID theft who has appeared on numerous TV outlets. He adds that this ‘paper’ could also be in the form of plastic, such as a credit card.
“You hear about major breaches of data information, but think about how often we hand over our credit card to a restaurant server”, Siciliano points out. “Those 16 digits are valuable.” This is especially true in the US, where chip and pin protection has not yet caught on.
A Name and Address Is Enough
Yet, credit cards are not necessary. A name and address is enough, argues O’Farrell. Thieves with this information can begin by making fake checks, which can be cashed for amounts up to a couple of hundred dollars at stores, without clerks becoming suspicious. Many stores won’t verify checks “because they’re cheap”, says O’Farrell.
“The victim will then begin getting calls from debt collection agencies”, he continues. “That’s impossible to stop, unless you change your name and address.” The telephone directory is, therefore, a godsend for the average identity thief.
If perpetrators can get more information, then they can execute more sophisticated attacks. “They want personal correspondence. They love a Social Security number – that’s a holy grail”, O’Farrell implores. “They want to know account numbers, your mom’s maiden name, and where your kids go to school.”
Much of this information is simply sitting in the average American’s mailbox. In many cases, the mailbox will be unprotected by the side of the street. There will even be a little flag alerting mail thieves to the presence of new bounty.
This is why being a mail carrier is a dangerous job. A year ago, O’Farrell recalls one case where an identity thief hired two thugs to mug a mail carrier and steal the master key for the mailboxes on that route. “These keys open everything”, he says, explaining that the boxes – and the locks protecting them – are decades old.
Once thieves have this kind of information, they will often sell it to a professional. There are few, if any, American cities that don’t have a data broker, which O’Farrell calls a “Fagin” for personal information, after the character in Dickens’ Oliver Twist who marshalled a group of young thieves. Task forces that he works with have intercepted people operating mobile ID factories, with laminators and hundreds of fake drivers’ licenses in the trunks of their cars.
The Social Security number is a weak point in the US system. “The fundamental flaw in the system is that we use the SSN as an identifier, yet it is far from being a private number”, says Robert Siciliano. “It’s the key to the kingdom. It’s the national identifier to be used in all of your accounts.” And yet, there is no national database for compromised SSNs, O’Farrell points out.
John Sileo argues that SSNs are sometimes traded on websites, or simply made up. He tracked one SSN theft case in which a six-year-old girl’s number had been stolen. One advantage of using a child’s SSN is that the credit reports associated with it will be clean.
The theft wasn’t discovered until the child was 16, at which point it had been used by three different people whose names didn’t match. “They probably got it from a healthcare provider who stole it from a doctor’s office”, Sileo says.
Burgled Data
Such physical thefts are not far-fetched. O’Farrell describes inside jobs in which a criminal’s girlfriend takes a job as a receptionist inside an institution, only to siphon information back to the criminal.
This brings us back to Fred Kost’s identity theft experience, which was the result of a physical breach. He eventually found that the stolen credentials came from a three-year-old transaction. He purchased a car from a luxury dealership, which then stored his physical documents using an outsourced storage provider. The provider was robbed, and multiple peoples’ personal documents were taken.
“That’s what’s clever”, says Kost. “This happened to be a luxury auto manufacturer. If you wanted to steal records of clientele with good credit, that’s a very good place to start.” Perhaps some of the people that steal physical documents aren’t simply dumb junkies, after all.