We are being increasingly asked to use our established social identities as a source of trust for communicating with a range of online services. Is this a good idea, is it safe and, if we go ahead, which ones should we choose to use? This needs consideration from both the consumer and the supplier side.
It is a good idea for consumers, if it makes our online lives both more convenient and secure. Having a smaller number of identities with stronger authentication meets those objectives. Using an established social identity can achieve this, if we trust it. To some extent this will depend on what service we want to access; for example, you may find it more acceptable to use PayPal, which you already trust with financial information, to identity yourself to an online retailer, rather than to use Twitter.
A consideration should be whether the social source of identity in question has some form of strong authentication. Google, Yahoo, Microsoft, Twitter, PayPal, LinkedIn and Facebook, for example, all do, enabling you to restrict the use of your identity relating to their service to certain pre-authorised devices. This is usually enabled using onetime keys delivered by SMS (test message), a separate independent channel of communication. The trouble is that this is usually an optional layer of security which many do not switch on, perhaps due to perceived inconvenience. If we are going to use certain social identities for more than just accessing the social network in question, we should get used to this concept.
With regard to online suppliers, Quocirca published a research report in June 2015 (Getting to know you, sponsored by Ping Identity) which included data on the perceived trust of various social networks as a source of identity. First, it should be said, that overall compared to other sources of identity, social identities are the least trusted. Just 12% considered them highly trustworthy, compared to 23% for identities provided from government databases and 16% for those from telco service providers. 53%, 22% and 32%, respectively, considered these sources untrustworthy. Clearly those proposing social identity as a source of trust have some way to go to overcome the reticence.
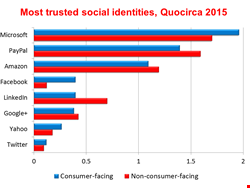
That said, there is huge variation in the level of trust placed in the different potential providers of social identity and it varies, depending on whether the organisation involved is consumer-facing or dealing mainly with business users (non-consumer-facing). For all, the top three most trusted were clear; Microsoft, PayPal and Amazon. For Microsoft this can perhaps be put down to long-standing familiarity and the fact that it is already the most highly trusted source of identities in business through Active Directory. For PayPal and Amazon it will be because they already deal with consumers’ money and have established the trust of business over time to do so.
Other social identities are less trusted by businesses. Consumer-facing organisations find Facebook more acceptable than their non-consumer-facing counterparts, but with LinkedIn it is the other way around. Google is equally trusted by both, Yahoo less so, and Twitter is trusted by few.
To make use of social identities, businesses need to do two things. First they need to ensure their customers and prospects have a degree of choice. In most cases it will not make business sense to dictate that all users must have a Facebook account or be on Twitter before they can transact with you. Good news—vendors of social identity-brokering products sort all this out for you and even offer local account creation if a consumer does not want to use social login. The three best known are probably Janrain, Gigya and LoginRadius. The consumer choses the identity they want to use, the broker authenticates it and passes credentials on to the provider of the services to be accessed. Janrain told Quocirca that its Social Login product inherits any strong authentication that users have put in place.
The provider must then decide what resources are to be made available. For example, a standard customer dealing with a travel agent may need access to separate systems for airline and hotel booking; an executive customer may also get access to a concierge service. This can all be decided by a single-sign-on system (SSO), an area where Quocirca’s research shows that many are now investing in new capabilities.
In particular they are turning to on-demand services (software-as-a-service/SaaS). Consumer-facing organisations are especially likely to be doing so. Providers include Ping Identity (the sponsor of Quocirca’s research), Intermedia, Okta, OneLogin and Symplified. IBM, CA, Symantec and Dell all now have SaaS-based SSO systems as well.
For many, the broader success of a re-vamped identity and access management (IAM) strategy will be the ability to manage these social identities alongside other sources of identity—for example, those of employees and partners. There will be some common resources and therefore policies that cover different groups and the need for common governance and compliance reporting across all; that requires federated identity management. Many of the leading identity vendors now support federate identity management; some such as Radiant Login specialise in it.
Furthermore both on-premise and cloud-based IAM requirements may need linking. Many vendors offer on-premise and cloud based product pairs; for example Ping Identity’s Ping Federated and Ping One, IBM’s Security Access Manager (ISM) and its Cloud Identity Service, CA Identity Manager and CA Identity Manager-SaaS and SailPoint’s IdentityIQ and IdentityNow.
As the range of end-users that organisations need to deal with continues to expand, so do the options for sourcing and authenticating their identities and the products available to enable and manage them.
Quocirca’s report, Getting to know you, is free to download here: