Netskope has just released its February 2021 Netskope Cloud and Threat Report, a study that analyses the main trends on enterprise cloud service and app use, web and cloud-enabled threats and cloud data migrations and transfers.
Besides confirming that the majority of all malware (61%) is now delivered via cloud applications, the report also sheds light on how cloud apps are reshaping the phishing threat landscape - cloud apps are now the target of more than one in three (36%) phishing campaigns.
A Common Denominator in Multiple Phishing Reports
Cloud services are very compelling for threat actors, a fact confirmed by multiple security vendors and organizations. A report released recently by Check Point found that in Q4 2020, Microsoft was the most impersonated brand, appearing in 43% of brand phishing attempts. Unfortunately, Microsoft is not the only cloud service in the top 10; LinkedIn (another Microsoft brand) comes in at number three (6%) and Google is seventh (2%). Interestingly, this report places technology on top of the most impersonated sectors.
Results are similar in other reports. Vade Secure researched 2020 in its entirety and, for the third year in a row, places Microsoft at the top of the list of the most impersonated brands. Unsurprisingly, it also found that cloud services are the most impersonated verticals.
And it’s not just security vendors highlighting the risk of cloud apps. The Q4 Phishing Trends Report 2020 issued by the Anti-Phishing Working Group (APWG), illustrates similar findings, placing “SaaS / webmail” at number two amongst the most targeted industries in Q4 2020. Having held the top spot for several quarters, it was overtaken by “financial institutions.”
Despite minor differences across the studies, they all agree and confirm that cloud credentials are top-of-mind for phishers. The pandemic has accelerated the adoption of the cloud as it has been found to be a conveniently rapid and outsourced method of responding to the immediate challenges of mobility and the multichannel provision of resources and business tools. The bad guys have quickly moved to monetise this trend.
Phishing from the Cloud, for the Cloud…
As well as being the most impersonated brands, SaaS / IaaS applications also offer an ideal infrastructure to deliver phishing pages. As we know, they provide simplified hosting for the attackers; they present the user with a legitimate domain, a legitimate certificate, and are implicitly trusted. All too often, they are whitelisted by legacy technologies that either can’t perform TLS decryption at-scale or simply lack the context of the connection and can’t recognise if the traffic is going to a corporate instance or a rogue instance of a cloud application.
Again, the numbers don’t lie. According to phishstats.info, in its Top 50 exploited ISPs for phishing so far in 2021, Google ranks number three, Amazon number six, and Microsoft number 11. Of note, three out of 10 domains appearing in the “Top 10 Hosts” are Google domains such as “docs.google.com” or “drive.google.com.”
Serving a fake login page for a cloud service from the same platform (or a cloud platform of the same brand) is easy pickings for cyber criminals providing more legitimacy to the attack and increases its chance of success. This is especially true for Microsoft and Google.
In the following example, Microsoft Forms is abused to host a Fake Microsoft Team (sic) login page:
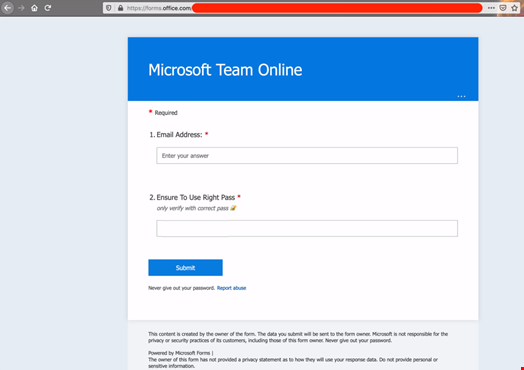
I know what you are thinking… and I know the answer: “no, the simple layout and the disclaimer about the submitted data do not make this attack harmless,” and neither do the efforts of the cloud service providers to take down these pages in a timely fashion. Shutting down similar pages takes much longer than setting them up despite them being replicable in different instances.
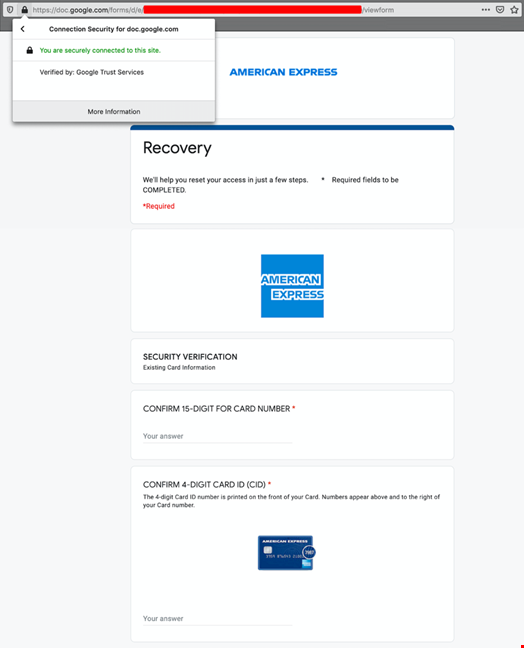
When it’s time to perpetrate a malicious activity, the bad guys can leverage the full potential of a cloud service, even when the latter offers a limited flexibility. As identified by the AWPG report mentioned earlier, “Financial Institutions” is the most targeted vertical for phishing. There are many examples of financial institutions mimicked on Google Forms. The one below shows the creativity threat actors apply to Google Forms serving quite a sophisticated American Express login page, which is clever given the limitation of Google Forms.
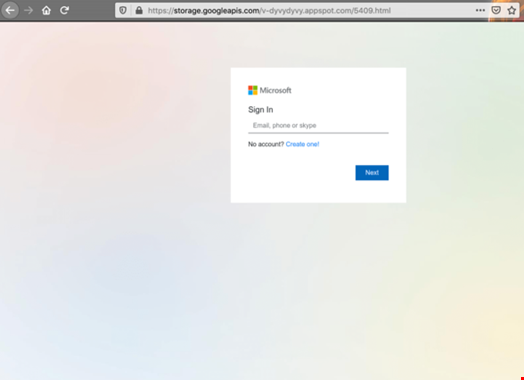
These are two extreme examples, but there are enough cloud platforms out there to build very convincing pages to mimic virtually any service belonging to any vertical. The screen shot below shows a fake Microsoft 365 page hosted on Google Firebase.
Cloud Services Are Reshaping the Phishing Landscape
It is evident that cloud services offer multiple attack surfaces to phishers. They are now the main entrance to corporate assets, and this explains why they are ranked at the top of the targeted sectors. At the same time, they are the ideal place to serve phishing pages:
- They can evade security gateways as the phishing URL and the corresponding traffic belong to a legitimate service
- They are trusted by users who recognize a domain belonging to a well-known organization
- They let the attackers build phishing pages very quickly and replicate them across different instances without all the additional tasks involved with traditional hosting. Additionally, some cloud services are powerful enough to build elaborate pages
- They make the attack even more convincing when the served phishing page belongs to a service of the same cloud service provider delivering the phishing page. For example, a fake Microsoft login form served from a Microsoft service
