Fujitsu CTI has been monitoring Dridex across our customers for a period of time. There have been evolving variants of the same campaigns attempting to deliver the Dridex banking trojan via malicious email attachments. Dridex recently targeted victims using a football lure in an attempt to deliver the malicious trojan.
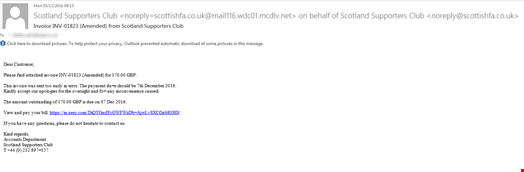
The recent change affects the delivery mechanism which has moved from a prompt to ‘Enable Macros’ to a script file inside a zip attachment hosted on a compromised personal Microsoft SharePoint site, which if executed would download Dridex. Further additions in this campaign include the use of wscript and network communications with compromised residential routers.
Fujitsu Cyber Threat Intelligence have been tracking Dridex for a period of time and observed significant changes in both delivery and execution from using the full range of Office documents, to today delivering a zip file with a malicious attachment. The version of the recent Dridex malware was a newer botnet ID of 2302 and a version of 196880.
Making Millionaires Out of Criminals
In 2015 the National Crime Agency indicated, conservatively, that criminals had stolen £20 million from UK victims alone. This resulted in a coordinated takedown of part of the infrastruture associated with Dridex.
How to Defend?
Educating our colleagues is key to protecting critical systems. Understanding the risks of opening and executing emails such as the one that used a football lure will ensure we’re better protected against risks such as Dridex. Although not used in this campaign, good practices in relation to Macros are available here from the NCSC.
In today’s threat landscape, organizations can no longer afford to be complacent when it comes to security. It needs to be top of the boardroom agenda. By implementing an effective security education program alongside a strong threat intelligence system and incident response plan, an organization can combat today’s cyber-criminal networks and protect their data assets.
Read more about Fujitsu’s ‘Secure Thinking’ offerings here
