As the world recovers and learns to live with COVID-19, the use of the pandemic as a phishing theme has started to wane. However, public wariness and anxiety surrounding an emerging medical concern will remain exploitable. Enter the current Monkeypox outbreak.
Over the past month, the Cofense Phishing Defence Center (PDC) has seen a series of Monkeypox themed phishing emails emerge as the outbreak has built momentum. Capitalizing on the growing concern and media attention, the emails have attempted to deceive enterprise staff, and attackers look likely to continue tweaking their tactics as the infection spreads around the globe.
In the past month, at least two PDC customers in the US have reported emails, such as the one displayed in Figure 1, in their Microsoft and Trend Micro environments. The emails use both the employee’s and company’s real names in the subject line and email body which changes depending on who is targeted. As a result, this creates an element of trust and personalization with the receiver, making the email look legitimate.
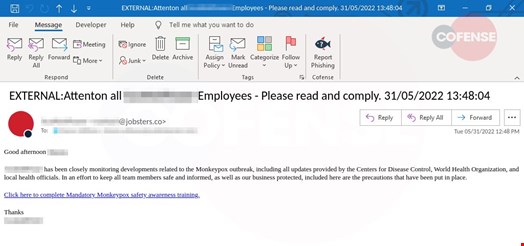
The intention is similar to what we have observed with COVID-19 themed phishing emails: using current topical content to motivate a reaction. The email body has stayed the same throughout the instances we have seen in the campaign and opens by mentioning updates from reputable health organizations to give the impression of veracity and seriousness. It stresses the importance of keeping staff and the company safe, a legitimate concern from businesses following COVID-19, in an attempt to make the employee feel like they share part of the collective responsibility.
Finally, the call to action in the email asks employees to click through to complete and comply with new mandatory safety precautions and awareness training. Again, this is something employees will have seen and gotten used to throughout the COVID-19 pandemic, so are less likely to question the safety of the link.
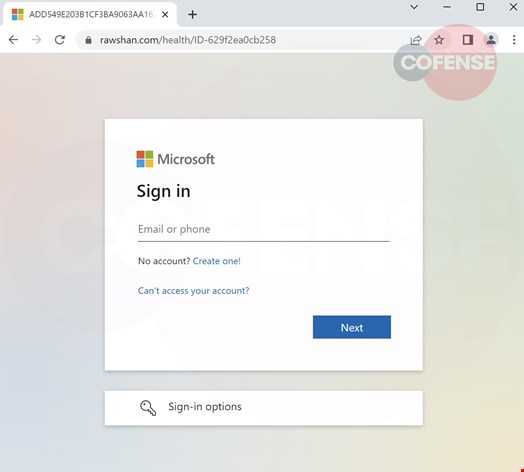
When they click through, users are directed to either a spoofed domain or an already compromised website. Looking at the URL, it is clear the threat actor wanted to add validity to the page by naming the directory as “health.” It is the standard Microsoft credential phishing otherwise.
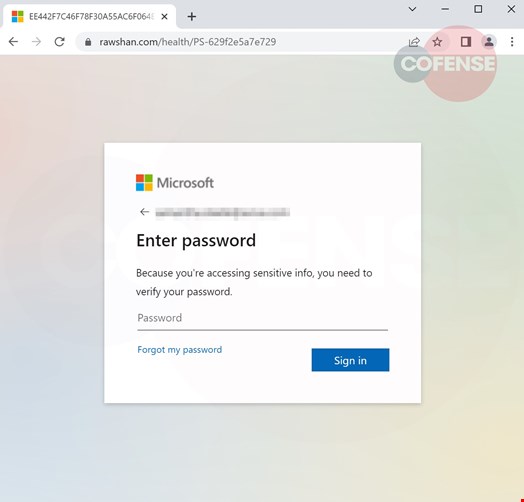
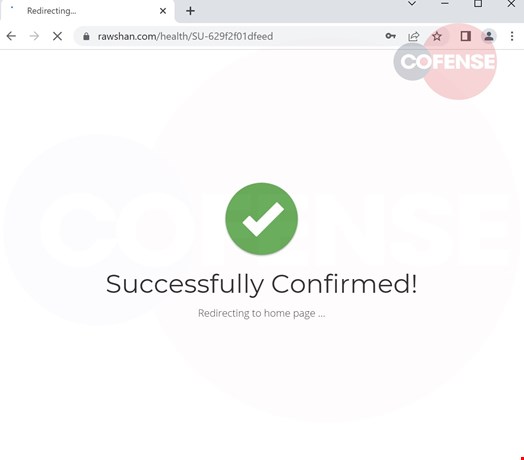
The website shows a legitimate looking login page that asks for the recipient's email address (Figure 2) and password (Figure 3), adding confidence from the recipient that this is necessary due to the sensitive nature of the information being accessed. Once the user has provided all credentials a confirmation page appears for a few seconds (Figure 4) before being redirected to the real Office 365 website.
This example shows the importance of educating your employees about what to look out for and what communications to expect from their employer. Creating a culture where employees know how and when to interrogate sender email addresses, URL links, files and other elements within emails helps to secure not only your people but also the future of your business.
Having this knowledge within your organization will help to reinforce your line of defense, and supplying an easy and automated way of reporting when it happens allows you to react quickly. In addition, having a consistent and central format for training and new policies will make it easier to spot if and when an attack is made that is out of the norm.
Overall, this threat campaign gives us an indication of things to come in Europe as Monkeypox cases increase in numbers globally. Threat actors will always be drawn to exploiting topical and emotive tactics, especially following the scale of COVID-19 and continued nervousness of a serious medical outbreak having already experienced consequences.
