As a society, we [that is the Royal we], businesses of all sizes, and their clients, in some manifestation may be a subject of inclusion into a data set which, is by association placed within a cloud-cloaked environment which may be tagged Big Data.
And this implies, or even dictates that our data and our lives are exposed to the potential of compromise by hackers, hacktivists, cyber criminals, state sponsored activities, and even the prying eyes of authorized agencies. In fact to place these observations in context, according to a recent report published by PwC, titled ‘2015 Information Security Breaches Survey’, consider the following interesting, and disturbing discoveries:
• The number of security breaches has increased, and the scale and cost has nearly doubled
• Nearly 9 out of 10 large organizations surveyed now suffer some form of security breach
In the Big Data space, with its obvious associated surface of attacks, and the extant state of data retention, many security professionals feel that the potentials for adverse compensations exist to a very attractive level for cyber criminality. In fact to look deeper into this world of extensive data storages, and what may be termed a Data Warehouse, makes the recent Experian security breach of 15m T-Mobile accounts so very pertinent.
Potential of Associated Exposure
Any Data Warehouse in the image of Experian, and of course other such agencies in the credit referencing industry, will host high volumes of potential and attractive targets upon which cyber-criminality will attempt to feed. And given the multiple third party relationships, and the necessity to provision access to compartmented data-sets to the authorized [paying] user clients, there would seem to be a high potential of associated exposure.
However, notwithstanding the recent encountered Experian breach, we should also consider the other forms of misuse of data, which by its very nature provisioned indirect support for criminal leverage against an in-scope set of targets. For example, in 2012 it was reported in the media that Experian had suffered breaches against its databases no less than 80 times, with one media report claiming that almost 15,000 credit reports were pilfered [their words not mine].
The company also hit the press when it was alleged that were under investigation for a previous breach in which around 200 million identity records were sold to criminals. In fact to summarize the current position of potential abuse and the related exposure, security expert Brian Honan said about Experian:
“I would argue that given the nature and sensitivity of the information being held by the credit reporting agencies, and the potential harm it could have on the affected individuals, these credit bureaus should not rely solely on their customers’ security to protect that data."
There have also been many other observations, and insights made by other notable security professionals such as Brian Krebs, in the past years relating to known incident’s. Here Brian commented:
"Experian also sells its own line of services for preventing identity theft. That means the company was in a position to profit not only from the data it reportedly sold to underground, but also from the demand the underground site created for Experian's credit-monitoring and other identity theft protection services."
This is an observation that brings out the element of a double-edged win-win where it would seem that the provider of diverse services is in a position to profit from the age of cyber adversity no matter what.
In fact, and as an unsavory reflection on the recent Experian breach, it would seem to be very contradictory that this very same breached company offer breach mitigation services - very amusing when one reflects on this month’s exposure. Maybe here there also is room for some self-education.
Open Source Intelligence Exposure
So where companies are allowed to house such large repositories of data in the form of a logical mass-storage Warehousing, they must go that extra mile to both prove, and to demonstrate they are appropriate custodians of such sensitive data-sets - and by inference must be in a position to evidence that they deliver the security mission beyond all reasonable doubt – here the definition of adequate is simply not fit for purpose.
However, given the size of Experian one would hope that such companies deliver their security to such a level that, the aforementioned breaches and exposures should never have happened in such high numbers. However, clearly flaws allowed a leverage point for a successful hack, and it is in this area where I feel this company, like many others, has missed one fundamental point of potential exposure – Open Source Intelligence (OSINT).
When we come down to the question as to how such successful attacks may be accomplished, I am afraid there is still a gap in the world of cyber security understanding of the wider ramifications of what OSINT is, and what it can really mean to a cyber-criminal or hacker who may discover, acquire, and exploit snippets of subliminal data leakage to accommodate an indirect exercise of Footprinting the environment to underpin a complete, or partial support for a subsequent direct attack.
Now I know this may look a tad pie-in-the-sky, but just think about this. If I [you] can map your company for all its visible, subliminal elements of data leakage, and interrogate the publicized documents, and maybe run the odd zone transfer or two, and then map some internal assets, we may be off to a good start. And then after this, if we sit down in a Cuckoo-Egg style of attack and take our time to then extract all of the metadata embedded within documents which have been published to the web in an uncleansed condition, we may well be in business.
The question is, would you care? As to the answer, I will give you a clue – it should be in the affirmative.
In the case of the Experian breach it may that there are some misconceptions of security as to what found its way into the public arena without due consideration of data leakage. For example there are over 600 documents publicized which may be copied down, many of which have not applied any form of data cleansing, or applied any security to the content, which means they are carrying all sorts of interesting snippets for an external onlooker.
For instance email addresses, user IDs, PC names, IP addresses, local folders and so on (See Fig 1 below). There are potentially hosts of open source, publically available snippets of intelligence that may also be used to socially engineer the target.
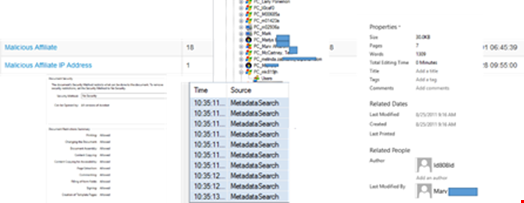
Inverting Cyber-Criminal Skills Into Organizational Security
There is no doubt whatsoever in my mind that those at the executive level of companies which have suffered breaches are asking the question as to why there investment and faith in the compliance/governance efforts, and the teams who are delivering security would seem to be underachieving.
The answer may be staring them in the face, which requires them to look to the field of the poacher, learn their dark-trade, and invert the skills of the cyber-criminals into the organizational security mission. It may be also time post so many security breaches which have hit the press to take stock, look, and start to consider removal of the snippet-led data leakage into public gaze.
However my ultimate conclusion is, if agencies such as Experian are going to hold my data relating to my mobile provider, credit card company, and any other such body who uses their exposed services in connection with me, may I conclude by demanding that I expect more from them when it comes to security, and hope they can up their game, and soon.
