Securing apps has never been easy, and in today’s world of remote work, it has become increasingly difficult. Employees can work from anywhere, and they do, often connecting to corporate resources through unsecured networks using any number of devices, including personal ones that IT does not manage. It’s opened a whole new set of challenges that must be managed and overcome.
To help do it, the Open Web Application Security Project (OWASP) has updated its highly recognized Top 10 List of most critical web application security categories. The 2021 list represents a major revamp that sees:
- Significant methodology changes that make it more data-driven than before
- Major ranking changes
- The introduction of three new categories
- Scope and name changes for four categories
- A degree of consolidation to more accurately reflect the changing threat landscape
What do these changes mean for your business’s application security, and how can you leverage the list to keep your applications and data safe? What are these changes, and why are they relevant?
We’re launching a four-part series to help you understand, and we’ll start with an introduction to OWASP.
OWASP is a non-profit foundation that aims to raise awareness about application security. Over the years, it has become the de facto gold standard for app security. Many businesses and vendors turn to them when they need guidance on the most pointed application vulnerabilities, and their listserv as checkpoints are among the first things application security teams consult when protecting their app and API assets.
New Data-Driven Research Methodology: Community Driven
In the past, OWASP research was primarily based on comments and feedback from security teams on prescriptive lists of vulnerabilities that OWASP supplied in surveys. While there was always scope for open feedback, there tended to be a disproportionate focus on listed items. OWASP thought this skewed the results and, in 2021, asked organizations to provide data on the prevalence of all the vulnerabilities they saw in their tests and used this to create a new, more data-driven list.
Yet, OWASP believes that an entirely data-driven list is like a window to the past, as it only captures known vulnerabilities and could be tested. Therefore, they augmented the results with a community survey that asked experts what they see as weaknesses that the data does not show yet.
The result is a list that renames and rescopes four existing categories to better reflect the root causes of security issues rather than a description of symptoms:
- A02:2021 - Cryptographic Failures
- A06:2021 - Vulnerable and Outdated Components
- A07:2021 - Identification and Authentication Failures
- A09:2021 - Security logging and monitoring failures
In addition, OWASP added three new categories
- A04:2021 - Insecure Design
- A08:2021 - Software and Data Integrity Failures
- A10:2021 - Server-Side Requests Forgery
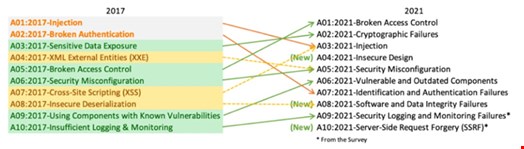
This new OWASP top 10 list represents a major revamp over 2017 and possibly the most dramatic since its inception in 2003. The new list will definitely help security teams target the most critical risks to their business and identify the right application delivery and security solutions to mitigate them, including web application firewalls that provide holistic visibility and enable a consistent security posture – even in the most distributed environments.
In the next article, we will look at the three new categories, why OWASP sees a need to expand application security to the left to keep up with new software development processes and what it all means for you.

