2021 saw a major revamp of the OWASP top 10 most critical and severe application security risks.
The first article in this series examined the new methodology that OWASP used to derive its ranking. The Second looked at the three new categories they added.
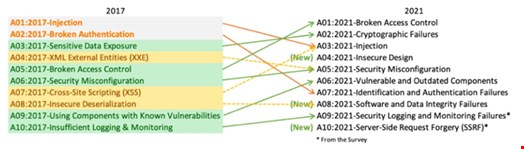
This article highlights the changes in the relative ranking of each application security risk and what they mean to you.
Broken Access Control: Rises to Number One App Security Risk
Previously number five on the OWASP list, broken access control has risen to the top spot. Security teams seem to be getting better at making sure they know who is accessing apps, but there is plenty of room for improvement in controlling what they can do with them. Yet, both are equally important!
OWASP reported that 94% of apps were tested for broken access control, with 3.8% having one or more flaws. Indeed, there were a staggering 318,000 occurrences of broken access control vulnerabilities in the data set.
Access control is critical. Yet, authentication is often put in place with no controls over the action a user, process or device can carry out. This has to change, as failure to ensure users, processes and devices cannot act outside their permissions leads to data security issues, data loss, modification and breaches.
Some actions to consider:
- Least privilege access should be your first principle. Least privilege access is the principle of restricting access rights for every user, APIs and processes to the absolute bare minimum of resources required to perform their routine and legitimate activities.
- Don’t forget to do a thorough audit of the current access policies of your existing applications. Maintain the least privilege principle – give no more rights to anyone than necessary – deny by default and enforce it!
- When access control failures occur, log them. Persistent failures could indicate an attack, and you should alert admins immediately – and block failing accounts.
- When you grant access, use a short lifespan on any session tokens used. This may minimize the window of opportunity an attacker has to compromise your applications. When a session is over, do not allow any tokens to be reused. Invalidate them immediately.
- Also, to mitigate the effect of automated threats, you should rate limit API access.
Identification and Authentication Failures: Still a Major Challenge
Under its old name of Broken Authentication, this category held the number 2 slot in 2017, but In its 2021 update, OWASP ranked it 7th. Finally, a welcome piece of good news!
However, make no mistake – these types of attacks remain extremely dangerous for a business. If someone can bypass or fool the authentication system, they have carte blanche to do pretty much anything they want and wreak a lot of havoc. To mitigate their impact, ensure that passwords are long, strong and frequently changed, and implement multi-factor authentication.
While ranked lower than they were, broken authentication attacks remain a significant challenge. Yet, the increased availability of standardized authentication frameworks and their adoption by businesses make them easier to manage.
Injection: Still a Top Three Threat After Losing Top Spot
In 2021, injection attacks fell from the top spot it long occupied on the OWASP Top 10 List, ranking third among most critical threats.
However, let’s not get overly excited. Injection attacks have not gone away and remain a genuine threat to businesses that need to be mitigated. In its report, OWASP stated that 94% of apps were tested for some, or all, of the 33 CWEs associated with injection vulnerabilities and that there were 274,000 flaws found, which equated to an average incidence rate of 3% - Not good!
To mitigate the impact of such vulnerabilities, make sure you have a positive security model that restricts which users, APIs and processes devices can run commands against sensitive data. At a minimum, you should employ server-side validation of commands and tightly control the use of SQL commands (e.g., LIMIT) within queries to prevent mass disclosure of records in case of SQL injection.
These changes at the top of the OWASP list are significant. Authorization and authentication work in tandem and must be considered together to tighten application security. Similarly, while progress has been made with injection attacks, they are still out there, and it is not time to take our collective foot off the gas of mitigation.
In the next and final installment of this series, we’ll look at poor security practices highlighted on the OWASP Top 10 list and what you can do to avoid them.

