The COVID-19 global pandemic has been a tough situation for everyone. Businesses have been affected by the economic downturn, and unfortunately, this has led to many losing their jobs. Despite the obvious human side, companies must also continue to think about cybersecurity regarding furloughed employees and their associated user accounts.
There are many cybersecurity risks associated with furloughed employees. What cybersecurity risks threaten furloughed employee accounts? How can businesses adequately protect themselves from the consequences of a breach involving a furloughed employee account?
What Cybersecurity Risks Are Posed by Furloughed Employees?
Furloughed employees often have access to different levels of business-critical data. If an employee who is now furloughed continues to have access to sensitive data, it can easily become a data leak risk for your organization. It is not to say that furloughed employees are, or have been, bad employees. Often, those who are furloughed include incredibly talented and valuable employees. However, leaving unfettered access to a furloughed employee can be dangerous for the business.
Let’s briefly consider the following:
- Distraction: A temporarily furloughed employee will no doubt be subject to many distractions such as taking care of their family, rightfully so. Protecting business-critical data is often not a priority during their leave. Even though the intention is to have the employee return, they may not view themselves as employees during the time away for all practical purposes, and possibly never return
- Phishing: Building on the fact that furloughed employees are distracted, they are much more likely to fall victim to phishing attacks. If a furloughed employee is still allowed access to digital resources such as email, this access can be a recipe for falling victim to the often very sophisticated phishing attack that targets various types of employees. Phishing attempts may even specifically target furloughed employees. Attackers may play the ruse of offering coupons, discounts or other financial assistance during the COVID-19 pandemic. However, in reality, this is simply an attempt to phish important information, such as user credentials
- Malicious intent: The third risk, hopefully, is one that is not too common. However, it can happen when a furloughed employee becomes extremely disgruntled and may want to inflict harm on a business. A furloughed employee with malicious intent may wish to harm the company any way they can. It may be by damaging data assets, compromising security controls, or even selling or willfully handing over their credentials to attackers
Securing Furloughed Employee Accounts and Access
Organizations have to decide how they will handle furloughed employees’ user accounts and access to company resources such as email, instant messaging, cloud storage, etc. In general, most cybersecurity experts advise that furloughed employees have all access to IT infrastructure disabled when they are away from the business.
It can be hard to determine if a furloughed employee will want to return to employment. Some may find other jobs, and others could be disgruntled due to the leave in the first place. Taking the approach of proactively disabling IT assets, including accounts, helps to ensure no matter what future actions the employee might take, the business is protected.
Disabling user accounts leaves these intact for the future return of the employee. However, it allows restricting the user account from use during the duration of the leave. In addition to account disablement, what other restrictions or actions need to be taken?
- Disabling all access to accounts – Active Directory, email, cloud storage, VPN, remote access, VDI desktops, etc.
- Reclaiming company hardware – cell phones, laptops, tablets, and other hardware
- Monitoring email accounts and other communications of the furloughed employee
- Are there shared accounts the user may have the ability to access? Be sure these passwords are changed as well
- Notifying third parties of any furloughed employees so these can ensure proper security of any third-party systems
Automating Active Directory Account-Related Tasks
Focusing on user accounts, Microsoft Active Directory is the most common identity access provider found in the enterprise data center. Many organizations use Active Directory as their on-premises identity and access management solution. Active Directory generally enables email access as well as the assigning of permissions on various digital resources on-premises.
When disabling access to various systems, IT administrators will want to start with disabling the furloughed employee’s Active Directory account. It will effectively remove access to all systems that make use of the Active Directory account for access. How can organizations automate the disabling and other Active Directory housekeeping that needs to take place for furloughed user accounts?
Using automated scripting to perform account-related tasks can maintain consistency and uniformity for handling furloughed user accounts. Below is an example of a simple PowerShell script to reset the password for an AD user account and add the user to a select Active Directory group while removing them from all other AD groups.
#Prompt to enter users AD ID
$readADUser = Read-Host Please enter a username to terminate
#Display current AD user groups
Get-ADUser $readADUser -Properties memberof | select -expand memberof | sort
#Prompt for new password for furloughed user
$newPassword = (Read-Host -Prompt Provide New Password -AsSecureString) Set-ADAccountPassword -Identity $readADUser -NewPassword $newPassword -Reset
#Add user to a special user group in AD and set as primary
$ADGroup = get-adgroup TERMEDUSERSADGROUPNAME -properties @(primaryGroupToken) Add-ADGroupMember -Identity $ADGroup -Members $readADUser get-aduser $readADUser | set-aduser -replace @{primaryGroupID=$ADGroup.primaryGroupToken}
#Find all group memberships and remove them except TermedUsersGroup and move to #TerminatedUsers OU in AD
Get-ADPrincipalGroupMembership -Identity $readADUser | where {$.Name -notlike TermedUsersGroup} | % {Remove-ADPrincipalGroupMembership -Identity $readADUser -MemberOf $ -Confirm:$false} Get-ADUser $readADUser | Move-ADObject -TargetPath 'OU=TERMEDUSERSOU,DC=YOURDOMAINNAMEHERE,DC=local' -Confirm:$false Remove-ADPrincipalGroupMembership -Identity $readADUser -MemberOf Domain Users -Confirm:$false
Securing Active Directory Accounts
In addition to securing furloughed employee accounts, organizations must ensure they give due attention to Active Directory account security across the board. Checking Active Directory accounts for password-related threats can help ensure proper security of your Active Directory environment and, by extension, any other system integrated with Active Directory.
Specops Password Auditor provides the tools needed to proactively scan and discover risky account passwords and settings in the environment. This includes breached or pwned passwords, default passwords and passwords set to never expire. You can also use Specops Password Auditor to scan password policies for compliance with password best practices from NIST.
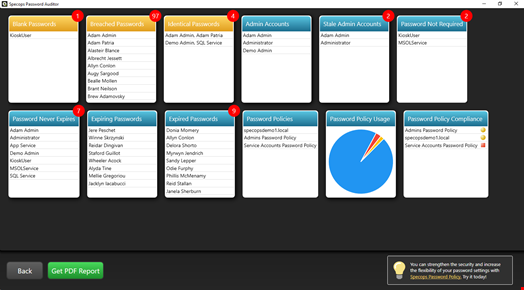
Giving light to dangerous passwords and other Active Directory settings can help prevent the compromise of any Active Directory user account, including disabled or ‘password-changed’ furloughed employee accounts.
You can learn more about Specops Password Auditor, its features and functionality, as well as how it can help further secure your Active Directory environment.

