There are many misconceptions when it comes to how most file sync and sharing services handle business-critical information
In their effort to maximize efficiency, organizations tend to incorporate externally provided and managed services into their infrastructure. One of the most frequently applied services is file sync and sharing. This service allows centralized, convenient and efficient daily work for employees constantly working with files such as word and text files, spreadsheets, presentations and so on. The information contained in these files is often business-critical; its unauthorized disclosure or loss would result in severe monetary and reputational losses.
So, if you are using file sync and sharing as a service, you have to ask yourself the following questions: How much do you trust your provider? Is trust enough for you? How certain are you that they do everything in their power to secure your business-critical information?
I’m raising these concerns as there are many misconceptions when it comes to how most file sync and sharing services handle business-critical information. Let’s explore some of them.
Convenience Is Key! (Should It Be Though?)
There is a constant debate about how much control and privacy one is willing to sacrifice for a little more convenience which rose to prominence when social media platforms appeared on the horizon. To begin with, everyone was freely providing huge amounts of personal information in order to have their feeds more custom-tailored to their desires. But as more and more data breaches came to light and awareness of cyber-crime spread, people started to become wary of sharing private information online. Taking into consideration that cybercriminals can sell your data, use it to breach other accounts, impersonate you and steal your identity – people are understandably concerned about how their information is managed and stored online.
Nowadays, we have reached the stage when the same concerns apply for organizations. As data confidentiality and user privacy is becoming ever more important, a convenient solution on its own is no longer enough.
Until now, most file sync and sharing solutions focused on making everything more convenient and security was relegated to the back seat in the process. So much so that if you look into the applied security measures, you realize that during the whole process of getting a file from point ‘A’ to point ‘B,’ the only time it is actually encrypted is when it is sitting still on a storage server. Which in most cases, does not even necessarily need to happen.
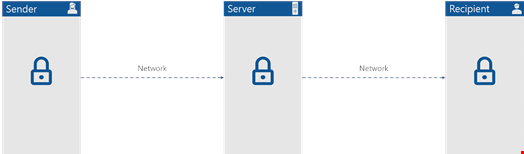
Most cloud services state that your information is encrypted while in transit and at rest. Sure, you might want to ask, what else is there? Either information is moving or sitting on a server, but in reality, things are a bit more complex.
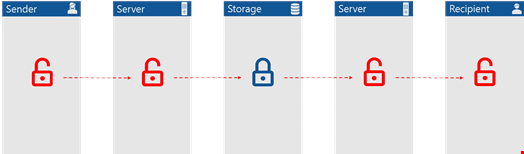
Firstly, in transit encryption applies to the communication channel and not the information passing through, meaning that information is readable if the channel security is broken.
The other issue is that at rest encryption is only applicable for a dedicated storage server which is used if information is retained for a longer period of time. If you are just quickly sharing data, it simply passes through still unencrypted.
Then there are the processing servers, i.e. the reason why security is so limited. Processing servers are responsible for providing all the features which make file sharing and sync convenient. In file search and parallel collaboration are only possible if there is a dedicated server which indexes every bit of information in a file, but to do so, it must be readable and unencrypted.
The bottom line? Working this way, your business-critical information may never get encrypted.
This brings me back to the questions I raised earlier. With this information at your disposal, do you still think that relying on trusting service providers is enough, and are you still certain that they do everything in their power to secure your business-critical information?
The Silver Lining
There are actually ways to strike a balance between convenience and security, using solutions that were designed by thinking outside of the box. Solutions with which your organization’s business-critical information is not only encrypted at all times, but also inaccessible even for your own provider. You only need to look for the right features – namely End-to-End Encryption (E2EE) and zero knowledge.
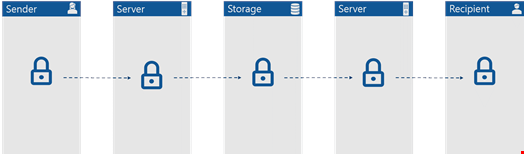
What E2EE does is prevent any file from leaving an end user’s device in unencrypted format and only makes it readable again once it reaches the designated recipient. Files travel encrypted through the whole journey.
Zero knowledge is in place to ensure no one apart from authorized users can view and manage files. By moving all the responsibilities of the file processing servers to the client-side, a secure environment is created, maintaining a convenient collaboration platform where server-side decryption is unnecessary.
In Conclusion
E2EE combined with zero knowledge creates a healthy balance between convenience and security, where you don’t have to rely on trust but have full control over your file sync and sharing environment.
If you wish to learn more about how to strike a balance between security and convenience, as well as develop a secure file sync and sharing environment, check out this detailed guide here.

