There are all sorts of potential for IoT-related applications to streamline business processes and provide new ways of interacting with customers.
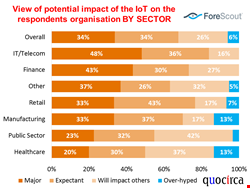
This was recognised by a cross section of industry sectors surveyed in a new Quocirca report that covered the UK and German speaking region (European Perceptions, Preparedness and Strategies for IoT Security, Oct 2016). In that, 68% said IoT was already having an impact or would do soon.
The respondents were conservative about the number of devices likely to be involved over the next six months compared to industry estimates from sources such as Gartner, McKinsey, Juniper and previous Quocirca research (The Many Guises of the IoT, Dec 2015). Overall, the average number of connected devices was estimated to be around 7,000 per organization (the survey ranged from small businesses to large enterprises). However, all agreed on the direction of travel; there would be more and more devices in the future.
In some cases, IoT deployments will involve isolated networks and many will involve sub-nets, where the only way to interact with a given set of things is via a hub (so for example, in a well set up home network, all smart devices are behind a secure router). In businesses however, most things will attach directly or indirectly to corporate networks. For network security teams this is a headache, as it means a rapidly expanding attack surface.
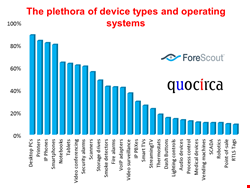
There is a reasonable level of confidence that devices connecting to networks can be identified and controlled. However, in many cases this is because network security teams are still mainly dealing with traditional devices such as PCs, printers and IP phones. As more IoT applications are rolled out, more unusual things will appear.
Many are designed to operate off batteries with low energy use and have limited processing power. This also means they are likely to run new operating systems designed specifically for the IoT such as TinyOS, Nano-RK or Mantis.
This poses another network security problem: the need to manage devices without endpoint agents installed. In the days when many network attached devices ran just a few familiar operating systems, mainly Windows and Linux, this was less of a problem. However, the increasing need to manage employees using their own devices and provide guest access to networks meant that relying on agents has not been practical for some time.
The situation is exacerbated by the IoT; fewer than 4% of respondents felt such agentless support was unimportant. However, 12% said their main means of controlling devices was still by using specialist agents installed on devices. At least that is better than the 72% that said they relied mainly on rudimentary control such as network passwords or Wi-Fi access keys!
This unsatisfactory situation explains why 45% of the respondents were planning to roll out new network security technology over the next 18 months. This rises to 54% for those who expect the IoT to play an increasing role in their business processes soon. They will need to look for technology that can provide continuous real time visibility of any device on a network, be it previously known or not.
The technology will also need to be able to apply policy based controls and updates to things and the software installed on them (currently only 37% say they have well established IoT policy controls in place). All this needs to be achieved without the use of agents.
Network access control (NAC) technology is capable of doing this and has been tried and tested over a number of years for identifying and controlling the way traditional IT devices join corporate networks. NAC products are now being adapted to provide advanced IoT security. ForeScout Technologies, which sponsored Quocirca’s latest research, believes it has taken a lead in adapting NAC for challenge of IoT security, through agentless discovery and classification, automated policy-based controls and ability to integrate with other security products. Other NAC vendors include Cisco, Aruba (now part HP), Pulse Secure, Bradford Networks, Trustwave and Portnox.
Most businesses are agreed on the potential of the IoT, however, many also have some way to go in ensuring the can roll out IoT applications with the plethora of unusual devices involved safely and securely. The time to adapt network security for the future is now.