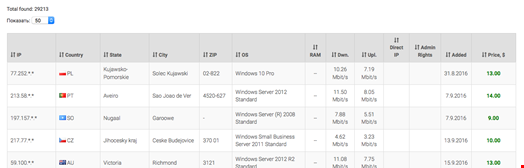
There is a criminal underworld of compromised services in existence on dark web forums. Examples of this include the recently disclosed ‘xdedic.biz’ site; this offered access to a device via way of its own malware. Selling access to these devices via the forum to anonymous customers at varying prices is dependant on capabilties such as RAM, download and upload speeds and geographical locations. Ultimate Anonymous Services (UAS) is a forum which exists both on the ‘dark web’ and ‘clear web’ offering compromised servers for sale using their own custom malware to leverage access.
A recent analysis by Fujitsu CTI identified a tool which uses a brute force technique to gain access to poorly configured servers directly facing the internet. This allows an attacker to perform automated attacks. Various operating systems including Windows Server 2012 and Windows 10 are offered for sale for as little as $14. The UAS RDP team offer access to almost 30,000 compromised RDS clients.
A Global Scale Compromise
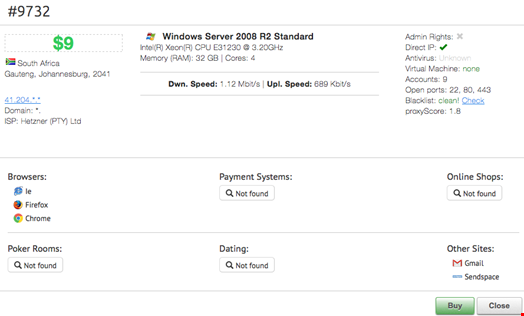
The global scale of the compromised devices is listed with options such as location, and whether the device has admin rights. Gaining admin rights on a compromised device would facilate lateral movement inside a network by an attacker as recently highlighted in the OPM hack which resulted in a US Government led investigation.
Is this enough? Xdedic Clone?
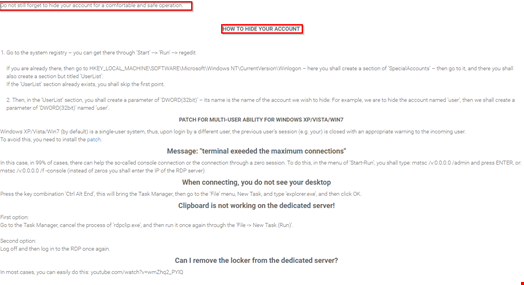
The similarities between UAS and xdedic are striking; logical similarities and the manner in which the forum operates are reminiscent of each other. The inclusion of stealthy instructions for hiding administrative accounts on compromised servers serve as proof of an intimate understanding of Windows OS, and whilst not indicative of a criminal mastermind it does seek to offer a way to undermine system administrators.
Being able to offer instructions on technical aspects is key to generating interest and repeat business, not just offering a service. This highlights some of the competition that a defensive team faces nowadays. Knowledgeable IT professionals are choosing to work for criminal groups in return for potential rewards.
How to Defend?
The ease in which criminals appear to have cloned, or reset, the xdedic forum is testament to the market place desire for access to compromised servers. These servers have been observed by Fujitsu CTI in conjunction with LinkedIn ‘sock puppets’ which attempt to perform fraudulent business transactions by leveraging ‘jump’ servers such as those for sale on the UAS RDP Shop.
System Administrators should apply security protocols to exposed servers and ensure the correct level of securely applied policies are applied to remote desktops, particularly those with direct internet access. The threat of brute forcing and compromise are clear by the sheer number of compromised devices for sale on UAS.
In today’s threat landscape, organizations can no longer afford to be complacent when it comes to security. It needs to be top of the boardroom agenda. By implementing an effective security education program alongside a strong threat intelligence system and incident response plan, an organization can combat today’s cyber-criminal networks and protect their data assets.
Read more about Fujitsu’s ‘Secure Thinking’ offerings here.
