US companies that operate in the European Union (EU) need to understand what drives European organizations when it comes to data protection. This applies to both commercial organizations that want to trade in Europe and IT suppliers that need to ensure the messaging around their products and services resound with local concerns.
A recent Quocirca report, The trouble at your door; Targeted cyber-attacks in the UK and Europe (sponsored by Trend Micro), shows the scale of cybercrime in Europe.
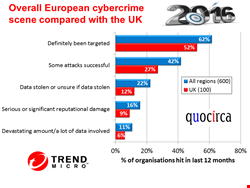
Of 600 organizations surveyed, 369 said they had definitely been the target of a cyber-attack during the previous 12 months. For 251 these attacks had been successful, 133 had data stolen (or were unsure if it had been stolen), 54 said it was a significant amount of data and 94 reported serious reputational damage.
The reality is almost certainly worse; many of the remainder were uncertain if they had been a victim or not. Cyber-criminals are the top concern for European businesses, above hacktivists, industrial espionage and nation state attackers.
This shows that European businesses have plenty to worry about with regard to data security – even before the added complications of the seemingly ever-changing EU data protection laws.
The new EU General Data Protection Regulation (GDPR) is looming and seems likely to come into force in early 2018. The good news for any business trading in Europe, is that the GDPR provides a standard way of dealing with personal data in all EU states (the current Data Protection Directive only provides guidance, from which many EU states deviate).
The bad news is the new stringencies that come with the regulation; fines up to €20M (Euro) or 4% of a non-compliant organization’s revenue, requirements to report breaches ‘without undue delay’ and the ‘right to erasure’ (often referred to as the ‘right to be forgotten’).
Given the scale of crime and the pressure to protect customer privacy, it is not surprising that protecting customers’ personal data is the highest priority in Europe, more so than payment card data (the processing of which can be outsourced) and intellectual property (which is less regulated).
US businesses trading in Europe need to adapt their processes to take into account the new regulation and the changing Safe Harbor arrangements that are in-place between the EU and US following a successful 2015 court challenge to the status quo.
The attack vectors of greatest concern for European organizations are exploited software vulnerabilities and compromised user identities. Protection against these threats is reflected in the measures put in place to help prevent targeted cyber-attacks in the first place and to stop them once in progress.
User identities can be protected by improved awareness around safe email and web use whilst infrastructure can be protected through software scanning and update regimes, all of which top the list of deployed security measures.
Addressing concerns about secure infrastructure should play well for US cloud service providers that get across the message that their platforms are more likely to be kept up to date, have vulnerabilities fixed at an early stage and generally will be better managed than is the case with much in-house infrastructure. The higher up the stack the cloud service goes, the better, so these benefits apply more to application level software-as-a-service (SaaS) than more basic infrastructure-as-a-service (IaaS). The caveat is that with new doubts about Safe Harbor, US providers really need to put in place European infrastructure to satisfy data protection concerns, a move many are now making.
All this said, European businesses know that sooner or later they will have to deal with a first, or for many another, successful breach of their systems and a potential data loss. So assistance with after measures will also go down well.
Malware clean up technology tops the list of deployed measures, but the ability to identify compromised systems, data and users is also understood.
Of course, all of these should be in place to assist with the execution of breach response plans, which should also include processes for informing compromised data subjects and data regulators, as well as having plans for good media relations. Less than half of European businesses have such a plan in place, but there is a willingness to implement them, perhaps with some help and advice from those with the skills and services to offer.
The volume of trade between the US and EU is huge, especially when it comes to technology. Talks to establish the Transatlantic Trade Investment Partnership (TTIP) should make it even easier for US companies to trade with those countries that remain in the EU (the UK may leave following an in/out vote later in 2016). TTIP will provide common trading rules on both sides of the North Atlantic, but it will not change the need for US-companies to be savvy about local EU data protection concerns.