In the ever-evolving battle against cybercrime, knowledge is the ultimate weapon. Cyber defenders need to rely on trustworthy threat intelligence to provide the best response.
Enter Ransomware.live, a website that has become a beacon of real-time intelligence for law enforcement, cybersecurity professionals and beyond. Founded by Julien Mousqueton, Ransomware.live is shedding light on the shadowy world of ransomware attacks, one data point at a time.

Mousqueton, CTO for Cybersecurity at Computacenter, started Ransomware.live in 2021 as a tool for himself and a few colleagues before realizing he could build the ‘Wikipedia for ransomware.’
His website is now used by millions of people across the world, including government and law enforcement agencies. It also serves as a tool to show that cybersecurity is for everyone and bust some cyber-myths.
Infosecurity asked Mousqueton to reveal his secret sauce which involves a €10pcm server, some homemade scripts and OpenAI’s ChatGPT.
Infosecurity Magazine: When and why did you start Ransomware.live?
Julien Mousqueton: In 2021, many of Computacenter's customers started to get hit by ransomware attacks.
Additionally, I was tired of hearing from security vendors claiming to experience a new cyber-attack every 11 seconds, which means nothing to me. Are they referring to intrusion attempts or actual cyber-attacks? I wanted to investigate the ransomware threat using accurate, tangible data.
I quickly realized that most ransomware groups used websites on the clear and dark web to make their victims public. I started creating a simple script to collect this information and send it to colleagues and peers through a Slack channel and then through Microsoft Teams.
In 2022, I discovered Ransomwatch, a website developed by New Zealand-based Josh Highet, collecting information similar to what I had done. I used his work to build my own website, but I quickly decided I wanted to add more information, such as screenshots of ransomware claims or victim descriptions. Similar websites like Ransomfeed or RansomLook were also built from Highet's work.
"The website's primary goal is to raise awareness about ransomware threats for people within and outside the cybersecurity industry."
In the summer of 2024, I rewrote the data-collecting script, gave my website's front end a complete makeover and added additional information. This new version was a way for me to distinguish myself from the competition, but it was also in response to suggestions and requests from government and law enforcement agencies. Now, approximately 80% of the website's code is my doing.
IM: Who is your website for and what can be found there?
JM: Today, on Ransomware.live, you will find the following information:
- Real-time data on the ransomware claim: every new ransomware claim, the name of the ransomware group, a screenshot of the claim when available, the name of the claimed victim, the discovery date, an estimated attack date when available
- Contextual data on the claimed victim: a short description of the organization, its sector, the country it is located in, a link to its main website, infostealer data
- Contextual data on ransomware groups: techniques, tactics and procedures (TTPs) and YARA rules
- Links to press articles reporting ransomware attacks
- Screenshots of ransom notes and negotiation chats when available
- Statistics on ransomware groups and ransomware victims
My idea was to build the "Wikipedia for ransomware," but purely based on my own needs.
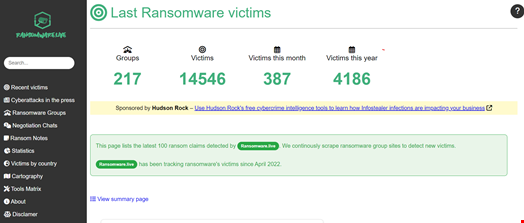
The website's primary goal is to raise awareness about ransomware threats for people within and outside the cybersecurity industry.
What makes me proud is when people use my website to show that cybersecurity is for everyone and bust some myths about cyber-attacks.
For instance, I was pleased to see that a security vendor recently used screenshots from Ransomware.live to show its clients that small companies were also hit by ransomware attacks.
Additionally, I have received feedback from the Dutch National Police, Quebec's Ministry of Cybersecurity and the Digital Economy. I have also heard from people in the industry that people at the French Ministry of the Interior, at some cyber departments within the French Army or France's Healthcare Computer Emergency and Response Team (CERT Santé) use Ransomware.live.
"I believe that providing raw information should be free."
From January 1 to July 31, 2024, my website's application programmable interface (API) received four million requests. Recently, a maintainer of OpenCTI, an open-source cyber threat intelligence engine, developed a plug-in linked to my API, which led to an explosion in visits.
The whole website runs on a €10pcm server from OVH Cloud and is entirely free to use - and will always be.
Of course, not everyone in the cybersecurity industry is happy with my website. Some vendors sell similar information. However, I believe that providing raw information should be free. If you want to monetize such data, you should provide additional intelligence.
IM: How do you collect information?
JM: Today, my scripts automatically scan ransomware groups' data leak sites and additional sources, like X (formerly Twitter) every hour, pull the data, which is formalized and pushed automatically to the website. The only part I do manually is adding a new ransomware group to my database.
I also use ChatGPT's APIs to provide additional information on the victims, such as a short description of the organizations, their sectors and the countries where they operate. For this, like for anything I've added over the years, what motivates me is my own need. This is why you may see more information on French and European victims, for instance.
Sometimes, users of my website also inform me of new ransomware attacks or ask me to make changes when the incorrect data is showing.
Additionally, several people are helping me, such as Will Thomas, a UK-based cyber threat intelligence analyst at Equinix, Allan Liska, a US-based CSIRT analyst at Recorded Future, Valéry Rieß-Marchive, a French cybersecurity journalist and cybersecurity firm Hudson Rock on infostealer data.
IM: How do you deal with false claims from ransomware groups?
JM: First, I keep a close watch on the website, which I also need to use in my daytime job and remove any mistakes I notice.
Also, Rieß-Marchive helps me track press articles covering attacks, usually from the victim's side, which are generally published before the ransomware claims. This adds a degree of reliability. Sometimes, I also receive insider intelligence on an attack.
However, I want to insist that the information Ransomware.live provides is what has been published by ransomware groups, but it is not necessarily the whole truth. That's why intelligence analysts should conduct additional research and cross-examine the claims with real-world evidence.
I cannot claim I did not publish any false claim, but I try my best to remove or modify anything that I realize is incorrect or misleading. This was the case with LockBit 3.0, when the ransomware group repurposed old intrusion data to make brand-new claims.
Recently, France's Ministry of Justice was inaccurately named as a ransomware victim. The real victim was a law firm. One of the reasons for this mistake was that many of this firm's emails were using addresses ending with .justice.fr.
Read more: From Protests to Profit: Why Hacktivists Are Joining the Ransomware Ranks
IM: What's next for Ransomware.live?
JM: I'm also teaching at École 2600, a cybersecurity school in the suburbs of Paris, and I would like to ask my students to help me develop the site. For instance, I would like them to work on a module following the cryptocurrency flows associated with ransom payments.
I also have a personal roadmap for the site. My priority is to find a way of collecting victims' domain names so that I can provide more information on infostealers affecting employees of victim organizations.
Another aim is to expand the list of sources my scripts scan for ransomware claims. For instance, I currently do not scan Telegram channels. I want to develop a bot that would scan Telegram channels and other sources.
