
In early 2012, one of the top banks in Israel was armed with state-of-the-art cyber protection: some seven layers of security, including a system that analyzed every email sent through the bank’s servers. The seemingly impenetrable set-up still wasn’t enough to prevent a clever hacker from finding a way in.
“This was an old-school attack on a sophisticated system”, says David Maman, founder and CTO of GreenSQL, an Israeli-based database security company.
When the bank’s cybersecurity system had examined a file that included a presentation, it found nothing wrong with it. But when a person opened the presentation file, a three-part quiz appeared. “It was only when he pushed one of the options that the exploits started working and infected the computer”, Maman recalls.
Data Breaches on the Rise
Although no sensitive information leaked in this particular case, it’s a reminder that even the toughest barricade isn’t foolproof. Oftentimes the stakes can be high as intrusions become more costly. The Ponemon Institute found that, in 2012, the average annualized cost of cybercrime for the 56 organizations it studied was
$8.9 million per year. That’s a 6% jump from 2011, when the average annualized cost was $8.4 million.
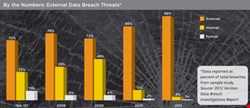
And data breaches from outside threats are on the rise. In 2011, there were 141 reported data hacking incidents defined as electronic entries by an outside party, malware and spyware. Last year, that number increased to 225, according to the Privacy Rights Clearing House, a non-profit consumer rights advocacy group based in California. Security industry insiders expect these figures to grow as vulnerabilities increase, coinciding with the rise of mobile use and the evolution of cloud storage.
This all comes as security professionals within both the private and public sectors continue to shift philosophy, shore up entry points, add cyber intelligence departments and install better detection programs.
A Different Landscape
“Companies are looking at security differently than they were 10 years ago”, observes Laura Mather, co-founder of security software provider Silver Tail Systems, which was recently acquired by storage giant EMC². “Back then, companies tried to ensure their infrastructure was completely locked down. Today the assumption is you can’t lock everything down. You’re never going to have a bullet-proof system. You constantly monitor for changes in your system because criminals have to do something different to get access. It looks different from what normal people do.”
Still, outsiders dominate corporate data theft, according to the 2012 Verizon Data Breach Investigations Report, which found cybercriminals were behind the majority of breaches – roughly 98%. Incidents involving hacking and malware were both up considerably, with hacking tied to about 81% of compromised records.
Recent years have given witness to changes in the data breach landscape. No longer are hackers mainly targeting companies’ servers; they are going after individual employees as well. As Maman points out, an intruder just needs to access a web browser and identify the person holding coveted information to instigate a breach.
Inside the Mind of a Cybercriminal
“All I would have to do is make sure this person gets to a specific link”, continues Maman, who got inside the mindset of an intruder for the purpose of this article. “So, I will learn which exact browser he uses. The second time, I will take control of his entire computer.”
Once he gains control of a PC, Maman insists: “I don’t care which firewall you have, which intrusion prevention programs you’ve got. I made it. And I [will take] control of his operating system.”
The database security expert says his next step would be to get the target’s user name and password, “to see which database he’s connecting to and managing, which information he’s exposed to, and then all I have to do is run an execution command to retrieve sensitive information when he’s not working – maybe overnight, or when he’s on his lunch break.”
Pharmaceutical Company at Risk
An attack like this can have serious effects on an organization’s financials, image and overall infrastructure. Take the following example, provided by Jeff Spivey, vice president of RiskIQ and international vice president of ISACA, in which a pharmaceutical company learned that information about the development of a new drug had leaked to a competitor in another country.
“They ended up being able to detect on their system that information, probably for eight to 12 months or so, had been leaving the company and going to another country’s IP address”, Spivey recounts. A lot of information trickled out, ranging from the company’s policies and procedures and drug formula details, to architectural plans for the plant, and even data on the people needed to run it.
“That nation-state would end up developing the drug in their country”, he says, adding that the intruders “would be taking all of that intellectual property”.
So how did someone from the outside manage to navigate inside? There were two possible ways: malware may have entered a key player’s mobile device either directly because someone loaded an app that had malware in it, or loaded an app that navigated to a website where the malware was then injected into the mobile device.
| "Today the assumption is you can't lock everything down. You're never going to have a bullet-proof system" |
| Laura Mather, SilverTail Systems |
“From there, the mobile devices and the malware could allow for complete surveillance – complete knowledge of what’s on the mobile device”, contends Spivey, who noted that attackers had access to email, file storage and telephone numbers.
“Microphones can be opened up and they can listen in on meetings that are occurring”, he continues. “They can take pictures of papers that are on your desk. Through that, as well as other connections to email addresses, an exploit was enabled that allowed them to get into the network of the company.”
Lessons Learned
So what can be done to prevent attacks like this in the future? A survey of security professionals suggests that a combination of better programs, improved skills and the deployment of new technologies can help.
“We must do a better job with detective controls”, insists SANS Institute senior instructor Paul A. Henry, a forensic analyst who teaches a course for the CISSP certification exam. “We have to eliminate only focusing at the gate and looking at inbound traffic. And we really need to start paying attention to what’s leaving our networks. If we could address that, we can cut these numbers dramatically.”
The right security professionals – with the appropriate skills set – have to be in place, many analysts say. “We need to skill up some of the people we have monitoring our networks and servers to make sure they can identify anomalies or make sure they have an escalation plan in place”, says Ian Glover, president of the Council of Registered Ethical Security Testers (CREST).
Glover expects to see an increase in attacks on the web application side due to the “number of insecurely coded systems”. “Pre-incident planning is very important”, he added. “You need to identify the right people to help you.”
Mather emphasizes the need to look more closely at web browsers; if data is available through a browser, or even through an organization’s intranet, then important data could be compromised.
“We’re seeing data breach attacks shifting from breaking into a database or stealing info, to now moving to a perpetrator finding the information they need displayed through a web browser...The more companies that recognize this going forward, the fewer attacks we will see.”
“We keep repeating the same mistakes that we’ve been making for a decade. We need to break out of the box and start looking at next-generation technologies that will help off-set this next-generation malware”, Henry adds. “On malware, for too long now, the bad guys recognize that we do a lousy job of patching.”
Also of importance, Henry maintains, is a better understanding of data leakage prevention methods. “Many organizations use it, but many of them have gone about it completely wrong. They’re not taking the time to properly classify the data within the environment, yet they’re spending $100,000 on a gold-plated box in an attempt to secure the environment,” he laments. “They don’t know where the data is located and they’re attempting to solve the problem with a Holy Grail solution at the gateway – and that’s not workable.”
If a data breach does occur, however, it’s important for companies and organizations to know how to handle it, as timing and execution decisions should be made very early on.
“They need to decide their objectives”, Glover says. “If they are attacked, they want to mimic that attack and close down any avenues that might be in place to continue that facilitation. If you want to catch someone, though, then they may not want to do that quite as quickly.”
Looking Ahead
As we delve further into 2013, analysts agree that although many go unreported, we will continue to see an increased number of attacks on our systems and networks.
“If you are criminally minded you would look at the penalties associated with it, the likelihood of protection and where you can do it from – and the fact that you can extract money, you would still view this as an area of potential,” Glover concludes.