
The market for vulnerability data takes on three shades, depending on motive. As security researchers increasingly attempt to commoditize their findings, Davey Winder seeks to put a value on vulnerability information
Responsible disclosure is one of those buzzwords bandied about the IT security community, but what does it actually mean? The common definition is simply: the process of informing a software vendor, in a timely and direct fashion, of a vulnerability or bug that impacts upon data security. If responsible disclosure can be summed up as ‘doing the right thing’ with undeniable benefit to all parties (the vendor plugs a security hole before it is exploited, the researcher gets kudos for finding the hole, the end-user gets data protection), then why are we even talking about a vulnerability data market?
The truth is that some security researchers are happy to sell vulnerability data to the highest bidder, often arguing that they deserve financial recompense for their work, and some vendors have entered the market by offering payment-driven bounty programs for bug hunters. Infosecurity has been investigating the price of vulnerability data, and the markets through which it is traded.
Black, White, and Shades of Gray
Let’s start by looking at the differences between ‘entrepreneurs’ who conduct vulnerability research for a profit, and those who seek this information from researchers and sell to the highest bidders with no questions asked. Dwayne Melancon, chief technology officer at security firm Tripwire, divides security researchers into four distinct categories:
- Those who are solely in it for the money, will sell to anyone, and don’t care about the motives or usage by the customer. “These black hat hackers are the kind who will put up an e-commerce storefront and accept payments from anyone who has the means”, Melancon explains.
- Those who are in it for the money, but tend to have ethical or moral standards that govern who they are willing to sell their research to. “Gray hat hackers are more likely to sell their research only to reputable organizations, such as law enforcement or governmental agencies”, Melancon observes, “however, it is up to the researcher to draw their own lines between good and bad”.
- Those who keep the information for themselves to create a business in other areas, such as mercenary surveillance and information interception as part of a business model. These researchers may identify with either black or gray hat classifications but keep their knowledge close to their vest and provide their findings via a professional services model, what Melancon describes as the “we know how to get things you can’t, so hire us and we’ll deliver the goods” model.
- Those who are in it for the challenge, or to make the world a better place. That said, they will make money from their research if they can but only via legal, moral, and ethical means. Your typical white hat hackers tend to stick to the responsible disclosure brief. “These researchers also participate in bounty programs”, Melancon points out, “because the information still goes directly to the impacted vendor.”
These bounty programs have been developed to encourage responsible disclosure, while at the same time acknowledging that time and effort demands some financial compensation. The alternative is simply to drive legitimate and ethical security researchers toward the dark side.
“There was a shift a few years back where security researchers realized it was often easier to sell a vulnerability to a broker rather than dealing with the companies directly”, explains Robert Hansen, technical evangelist at WhiteHat Security. “Companies often react badly, and want to go after researchers, who for the most part have no ill will toward the companies in question. So rather than dealing with that, the researchers turn to middle men who help broker those deals, lowering their risk.”
Infosecurity spoke to Jacob West, CTO for HP Enterprise Security and the man who heads up HP Security Research (HPSR), which puts together threat briefings and actionable security intelligence based on information the division gathers. West has hands-on knowledge about operating a bug bounty program, the HP Zero Day Initiative (ZDI), which works with the top-tier of global vulnerability researchers and provides all of the vulnerabilities procured to the affected vendor, free of charge.
“HP’s ZDI acts like a middleman, allowing researchers to focus on vulnerability research while HP manages the process associated with responsible disclosure”, West explains. “Researchers trust that HP’s ZDI will work diligently to get the issues resolved and will not hold back disclosure of critical vulnerabilities if software vendors become unresponsive or unwilling to work on a patch.”
To give you an idea of the kind of money involved, at the last Pwn2Own hacking contest, the HP ZDI program offered $100,000 for a working exploit against the latest versions of Internet Explorer 10 on Windows 8 and Google Chrome on Windows 7. “Overall, the competition was so successful that HP’s ZDI gave away more than $500,000 in cash and prizes for exploits taking advantage of critical vulnerabilities in Internet Explorer, Google Chrome, Mozilla Firefox, Adobe Flash, Adobe Reader, and Oracle Java”, West admits.
Along these same lines, Microsoft has just announced its entry into the cash-payout fray, unveiling three new ‘Heart of Blue Gold’ bounty programs that will pay up to $100,000 to enterprising researchers and hackers.
Moral Choices
What about the ethical implications of commoditizing vulnerability information? When, for example, does selling such data back to a vendor move out of the realm of responsible disclosure and step into extortion territory? EJ Hilbert is managing director for Cyber, Investigations & Disputes at global risk consultancy Kroll Advisory Solutions, and is quite clear that extortion comes with a threat, whereas responsible disclosure is all about sharing what you found in such a way that it can be addressed but people still know about the threat.
However, not everyone agrees that things are so clear cut. “The danger of the ‘vulnerability research’ culture is that it’s adding further eyes into the mix whose motivation is simply to discover vulnerabilities without worrying about resolving them”, argues Steven Furnell, IEEE Senior Member and head of the Centre for Information Security & Network Research at the University of Plymouth in the UK. “This in turn serves to increase the pace of discovery, and the consequent risk of exploitation.”
Prof. Furnell continues: “from this perspective, it’s also arguable that companies like Google publicly laying down the gauntlet (and offering financial reward) with their Pwnium challenge are not helping the situation for the wider developer community.” The argument is that while Google actively invited the discovery of bugs to gain intelligence, it clearly did so with the confidence it had the resources to respond. Meanwhile, other companies may not be as willing to welcome such attention, but could end up being considered equally fair game on the basis of Google’s stance.
Katie Moussouris is a member of FIRST (Forum for Incident Response and Security Teams) who thinks that most researchers who approach vendors and want money won’t try to extort because there are usually mutually beneficial business arrangements if they are savvy, and many are. “If a researcher approaches the vendor with some vulnerabilities that the vendor didn’t ask for, the vendor can simply say no thanks if they don’t usually pay bug bounties”, she says. “Another possibility is that a vendor can ask to see a vulnerability or two to see if hiring this researcher as a regular employee or contract pen tester makes sense.”
As for the legal implications of selling vulnerability data back to vendors, Moussouris is quite clear: “we as an industry can figure out mutually beneficial ways to work with these researchers who want money in exchange for their work and ideas, so there’s no need for legislation against exploit sales in my opinion”.
Price Tag
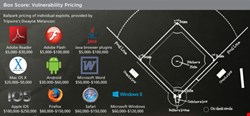
Given that vulnerabilities will always exist within software and services, and some researchers will want to profit from discovering this data, just how much is vulnerability information worth on the open market? Dwayne Melancon has seen a big difference between the cost of toolkits (used to exploit vulnerabilities) and specific exploit data. “For general-purpose toolkits, such as those used to steal user credentials or create botnets, the market is global and the price ranges wildly from several hundred dollars for a one-time use, to $5000 per month on a subscription basis”, he reveals. “For individual exploits, the price is generally much higher, with a zero-day vulnerability starting at about $50,000.”
The actual price varies according to a number of factors, such as:
- Exclusivity (if the vulnerability is sold to multiple buyers, it costs less)
- Publicity (if the vulnerability is known it is worth less – secret or undisclosed vulnerabilities are worth more)
- Reputation (in the underground market, the best researchers develop brand equity and can charge more than other researchers)
- Applicability (the more widely used an application or operating system is, the more valuable the vulnerability)
Vulnerability and exploit sales represent a relatively new marketplace, and as with any new marketplace, prices and what is in demand are still in flux. “Globally, there are no geographic variations in value, but prices increase from the white market, to the gray market and onto the black market”, Moussouris explains, adding “most vendor bug bounties and other white market programs offer $500 to $3000 per vulnerability, and fully functioning exploits can fetch $100,000 to $150,000 in the white market.”
| "Globally, there are no geographic variations in value, but prices incresae from the white market, to the gray market and onto the black market" |
| Katie Moussouris, FIRST |
The black market is more difficult to estimate, not least because the ‘dark market’ where exploits are traded consist of member-only underground, Tor-driven discussion boards and IRC servers that have proved difficult to infiltrate. Black market transactions are also a lot more complex than simply handing over cash for data.
White Hat’s Hansen told Infosecurity about vulnerabilities traded in Rubles (using trading accounts in Russia) and converted to dollars at a later date, with Bitcoin and the like being popular for smaller transactions. Then there’s the bartering system, with black hats happy to trade botnet rentals for exploits, or swapping vulnerability data in exchange for hacking into a specific service or account.
One thing is for sure though, the black market is where the big money currently sits. Alex Kirk, a researcher from Sourcefire’s Vulnerability Research Team, told us that ‘Paunch’ (the curator of the Blackhole Exploit Kit, which is made up of a group of vulnerabilities targeting unpatched systems) is currently offering a bounty of $100,000 for each new zero-day exploit created in popular products like Java, Flash, Internet Explorer, and so on. “The economics of this market are fascinating”, Kirk concludes. “On the one hand it’s a fairly public market with hackers and corporations publicly offering bounties, but there is also a really dark market, where the financial stakes are even higher – and it’s here that you’ll find hackers who don’t want public notoriety or for their existence to be known.”