Infosecurity Magazine Features

Selling biometrics to the masses
The biometrics industry may not always get good press, but at least it’s still getting press. In the aftermath of the Biometrics 2010 conference, Kevin Townsend takes a look at what’s right and wrong with the technology, and how its future is taking shape

Blurring the Lines: Information Security in the Public and Private Sectors
There are similarities and differences in the approach to information security in both the private and public sectors, including the relevant laws and regulations. The (ISC)² U.S. Government Advisory Board lends its observations regarding information security strategy and implementation within these two realms, along with factors seen as key drivers in both the public and private sectors.

Understanding the Drivers for Secure Data Storage
Storing and securing data can be a headache for most IT managers but, as Steve Gold explains, the problem can be solved with the correct approach
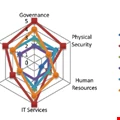
Securing third parties? Yes we CAMM!
It was at the RSA show in San Francisco in March that Adrian Davis, senior research consultant, ISF, first mentioned two initiatives: CAMM – the common assurance maturity model – and the ISF third-party standard. Several months later, Eleanor Dallaway sat down with Davis and Raj Samani, CTO, McAfee EMEA, to discuss the initiatives that have the power to change the industry, for the better

Digging Up the Hacking Underground
The hacking underground is driven by three things: money, information, and reputation. Danny Bradbury takes a walk through its dark tunnels

Charitable misgivings
Trust makes the world of non-profit charity go round, and a breach of this trust can lead to irreparable damage of a charity’s reputation. Wendy M. Grossman investigates the unique pitfalls facing those who are in the business of giving.

Social networking: The ‘what not to do’ guide for organisations
Sales and marketing executives are getting excited about social media, and savvy IT professionals are backing them up. There has been a sea change in the last three months, as Twitter, in particular, takes the corporate world by storm. Infosec professionals are left wondering whether social networking is leading the way, or in the way. Brian McKenna reports

When Trust Is Not Enough: Examining Insider Threats
Whether perpetrated by means of sleek corporate spying or dim-witted neglect, odds are that your insider threats will go undetected for an uncomfortable amount of time unless you play your hand correctly. Drew Amorosi investigates some of the common causes of internal data leaks and reveals its many faces

Navigating the black hole of small business security
Although size may indeed matter when it comes to larger organisations’ ability to dedicate security resources, evidence shows that smaller firms are well aware of the information security threats they face – but the question remains about where to focus these smaller budgets. Stephen Pritchard examines the options currently available for SMEs

The art of social engineering
Social engineering is not new and it’s here to stay. Kevin Townsend looks at how social networking is a social engineer’s best friend and asks what we can do to protect ourselves from this very real – and very personal – threat

How Not To Spend Your Infosec Budget
Spending money on information security is essential for most companies – be it in the form of technology, awareness, or education – but it’s where you spend it that makes all the difference. Wendy M. Grossman investigates which technologies and activities are worthy of your budget, and which are a complete waste of money

Credit Card Transactions: Held to a Higher Standard
There are numerous access points for thieves to make off with credit data, with just as many fraud techniques available. Drew Amorosi surveyed experts in the field to get their opinions on fraud trends, the effectiveness of standards, and what can be done to protect merchants and customers alike, and not just the ‘five families’ of the credit card Cosa Nostra.

Shopping for security: Securing the e-tail market
As the online retail sector continues to expand, encouraging a wider audience to shop online, it’s important that online retailers protect their brand by securing their customers’ credit card details. Cath Everett reports

Does Web 2.0 Need Security 2.0?
With the proliferation of Web 2.0 services, security concerns have escalated. Davey Winder investigates how infosec vendors are addressing these challenges and wonders whether security 2.0 actually exists

Do Punishments Fit the Cybercrime?
Although some collaborative strides have been made, the international law enforcement community still lacks sufficient resources and skills to have substantial impact on the cybercrime juggernaut. The (ISC)² U.S. Government Advisory Board examines deterrent effects of recent high-profile prosecutions, legislative gaps, challenges in US cybercrime laws, and obstacles facing international law enforcement strategies.

A Clear Future for a Cloudy Concept
Cloud computing – it’s an industry buzz word that is all the rage. The concept is hardly new, and many companies and organizations embraced cloud computing services long ago. However, as budgets remain strained, the push toward more economical cloud services remains ever-present. Stephen Pritchard asks the questions every enterprise needs to know about security when transitioning to the cloud

Securing the Friendly Skies
Aviation security and information security are inextricably linked. So much of what makes up aviation security depends on sound information security; encompassing the protection of intelligence, procedural, systems, and network data. For all-too-obvious reasons, much of what goes on behind the scenes at airports with respect to information security is a closely guarded secret, whether it is the alphabet soup of governmental agencies in play or the airlines themselves. Drew Amorosi reports

Information security in 2020
Information security has come a long way since the days of the Y2K IT problems and the infamous MafiaBoy staging a DDoS attack on major sites such as Amazon, CNN and Yahoo! in February 2000. Looking ahead, where will the industry be in 2020? Steve Gold asks some of the industry’s finest minds to share their predictions
Running the Right Risks
Standards cover much of the field of information risk management, but there is an art to the rational understanding and mitigation of risk that is more about skill than knowledge. Brian McKenna uncovers how the discipline can be practiced with a cool head and a calm stomach

What makes a CISO employable?
The position of chief information security officer (CISO), or an equivalent role, is increasingly commonplace within business, government and the non-profit sectors. In 2009, approximately 85% of large organisations globally had a security executive, up from 56% in 2008 and 43% in 2006. Avtar Sehmbi examines the desirable skill-set for the role of CISO and asks industry peers what hiring executives are looking for when recruiting for this position



