


Social engineering is written about widely, although definitions and mitigation strategies vary. The following definition highlights the key elements of social engineering: ‘Deliberate application of deceitful techniques designed to manipulate someone into divulging information or performing actions that may result in the release of that information’.
Social engineering is unique in that the victim is not consciously aware that their actions are wrong when being targetted. The social engineer exploits natural instincts and subconscious behaviour. Social engineers targetting information often use conscious techniques including bribery or threat of violence.
Social engineering attacks can be either targetted, or opportunistic. Targetted attacks typically focus on a specific individual, whereas opportunistic attacks aim to glean information from anyone in a specific position (e.g. helpdesk).
Legal issues
Unlawfully obtaining personal information is also covered by section 55(1) of the Data Protection Act 1998 which states that “A person must not knowingly or recklessly, without the consent of the data controller, obtain or disclose personal data or the information contained in personal data; or procure the disclosure to another person of the information contained in personal data.”
Depending on the attack, it may also be against Article 8 of the European Convention on Human Rights which states that everyone has the right to respect for his private and family life.
For companies operating or owned in the United States, the Gramm-Leach-Bliley Act of 1999 bans the act of assuming a false identity in order to gain access to financial data (sect 6821). Also the US Telephone Records & Privacy Protection Act of 2006 carries up to 10 years imprisonment for anyone making false or fraudulent statements or representations to an employee of a covered entity.
Hunting and farming
Social engineering attacks can be divided into two categories; hunting and farming.
While hunting aims to extract information with minimal interaction with the target, typically involving a single encounter, farming aims to establish a relationship with the target over a longer duration.
The fundamental differences between hunting and farming are the number of interactions between the social engineer and target.
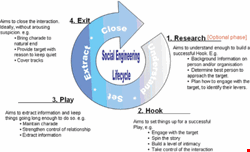
The four phases
A social engineering attack typically comprises four phases (see figure). Of these four phases, the research phase is optional. There is no typical duration for each phase, it may consist of one short telephone call (hunting), or span years (farming).
Throughout the research phase, the social engineer can use a variety of sources to research their target, including online information, public documents and physical interaction. Research is only necessary, however, when the social engineer is targetting a specific individual.
The social engineer will then endeavour to ‘hook’ his/her victim by engaging with the target and providing a pretext to entice an interaction. At this stage, influencing skills come into play. Psychologist Robert Cialdini cites six levers that are relevant to social engineering:
Reciprocation: Manipulating somebody to feel grateful and thus obligated to the social engineer. This often results in the victim feeling that they owe the social engineer a favour.
Scarcity: Manipulating a victim into compliance by threatening the short supply of something they need/want.
Consistency: Human nature means that people generally try to stick to promises, so as not to appear untrustworthy.
Liking: People are more likely to comply with someone they like.
Authority: People comply when a request comes from a figure of authority.
Social Validation: People comply if and when others are doing the same thing.
The purpose of phase 3 – ‘Play’ – is to keep a dialogue going long enough to extract information. This state of play was summarised well by the Met Police in Fraud Alert, who declared: “By the time the victim has overcome all the hurdles [set by the fraudster], he is in such a state of involvement that he is practically throwing his money at the fraudsters just to finish the course”.
Typically, the information targetted by the social engineer can be divided into two categories: Primary information (which is the main target), and enabling information (which may assist in the acquisition of primary information).
Finally, in stage 4 – the exit – the social engineer aims to close the interaction with the target without arousing suspicion.
Occasionally, there are circumstances when the social engineer may be unconcerned about arousing suspicion. This may be due to lack of traceability, or if the fraudster is beyond the reach of UK law enforcement.
Attack channels
Social engineers can use several avenues for attack. The telephone is a popular channel for information brokers, and more recently text messaging. Face to face, social engineers can manipulate or coerce victims into providing information. Most common however, social engineers will use websites and emails (phishing) to encourage users to enter credit card details or other sensitive information.
| "Social engineers targetting information often use conscious techniques including bribery or threat of violence" |
According to US-CERT, the United States Computer Emergency Readiness Team, phishing is on the increase. There has been exponential growth in the number of new phishing sites reported – a growth of over 500%. While phishing attacks are an example of opportunistic hunting, spear-phishing is more targetted.
The final two attack channels – postal service and fax – are less prevalent, but apparent and sinister nevertheless.
Who wants your data?
The answer is a lot of people. While you might first think of cyber-criminals – organised crime that focuses on identity theft and fraud – your information might also being hunted by private investigators, journalists, foreign intelligence services, commercial organisations and individuals both inside and outside of your organisation.
According to Bill Goodwin in his article ‘Foreign intelligence agents hacking UK businesses governments warn’ – published by Computer Weekly – “Overseas intelligence agencies engaged in economic espionage are targeting UK firms. Attacks have increased over the past 12 months… They use social engineering techniques to trick staff into opening e-mails or plugging in USB memory sticks to infect computers with hacking tools”.
Insurance companies, lenders and creditors, and debt collectors all have an apparent incentive to acquire confidential, personal data, particularly with respect to suspect claims, or to recover a debt from borrowers who have defaulted on their loans.
Debt collectors may also be advised to use social engineering strategies to find missing overdue account holders.
Building awareness
Organisations undertaking risk analyses of exposure to social engineering typically start by developing an awareness programme. The effectiveness of such social engineering awareness programmes varies.
| "Only 20% are conducting security awareness programmes... even fewer are actually measuring the awareness" |
Aaron J Ferguson reveals a case study whereby the West Point Carronade awareness programme was ineffective. He explains, “Cadets at West Point receive security awareness training. The freshmen spend four hours (four lessons) learning about information assurance and network security”, he writes. “There is a culture at West Point that any email with a “COL” (abbreviation for Colonel) salutation has an action to be executed...The email message informed cadets of a problem with their current grade report and instructed them to click on the embedded hyperlink to make sure their grade report information was correct….. Even with four hours of computer security instruction, 90% of the freshmen clicked on the embedded link.”
Awareness programmes combined with measures to evaluate their effectiveness is the best approach. Although effective, it is rarely used. According to the 2007 CSI Computer Crime and Security Survey, “only a small portion (20%) [of respondents] are conducting security awareness programmes, even fewer (10%) are actually measuring the effectiveness of the programmes”.
There are three categories that are considered to mitigate the risk of social engineering; people, process and technology. This list is not exhaustive, however, and may not be applicable to all organisations.
People
- Provide staff with clear boundaries: All staff should be keenly aware of the policies regarding the release of information, with clear escalation paths should a request fall outside of their boundaries.
- Permission to verify: Provide staff with the confidence to challenge even innocuous requests.
- Engender a sense of importance of information: Even seemingly innocuous information, such as telephone numbers (enabling information), can be used to stage an attack.
- A no-blame culture: The targets of social engineers are victims. By punishing staff who have been deceived, they are less likely to admit releasing information.
Process
- Bogus call reporting sheets: Where a suspicious activity has occurred, staff should complete a form detailing the interaction.
- Notifying customers: Where a caller is denied information, the organisation contacts them at a later date to notify them. This can be used to verify whether the caller was entitled to the information.
- Escalation route: Clear reporting lines for front-line staff to escalate doubts they may have about the person they are interacting with.
- Tiger testing: Routinely test staff susceptibility to social engineering attacks.
Technology
- Call recording: Routinely record incoming telephone calls to assist investigations.
- Voice stress analysers: Determine if the caller is likely to be lying.
- Bogus lines: Route calls believed to be suspicious to a monitored number.
A real threat
The threat of social engineering is very real. An industry that unlawfully extracts information for their customers exists and is very profitable. To counter the problem, it is important to understand its nature. This means defining the likely threat actors and their level of resources.
Social engineering is regarded as a low-tech attack due to the low level of technical resources required. Technology can be used as a control, but not in isolation. Therefore, resources should be channelled into education and cultural change.