
It’s no secret that one of the biggest threats to securing corporate information infrastructures isn’t, ultimately, the latest variation of the Flame virus or new malware that exploits vulnerability in an operating system or application. One of the biggest threats is employees themselves – either through a malicious action or, much more likely, inadvertent error.
That’s why information risk management is one of the most important new skills that security professionals need to master in order to add value. As the use of cloud computing and mobile devices increases substantially – from small start-ups to the Fortune 500 – corporate information assets have left the building, and keeping them secure has become much harder. As a result, security professionals must evolve into advisors. Information risk management, furthermore, is not the only new tool they must add to their arsenal; security professionals also need to master governance and compliance, privacy, metrics and data analytics, and business consulting skills.
Changing Gears
Protecting information no matter where it is located requires a fundamental shift in focus. Information security professionals who are accustomed to concentrating on technology need to switch gears and focus on business processes and data. Both cloud computing and mobile devices are driving this transition, demanding that security professionals spend more of their time on governance and providing advice to their organization than on direct operational responsibilities for cloud and mobile environments.
“Organizations are eager to leverage cloud solutions – not only as a means of reducing cost, but also to provide product/service scalability and redundancy not easily supported through traditional IT solutions”, says Erik Friebolin, managing principal at Verizon Enterprise Solutions – Global Risk Services. “As a result”, he adds, “security professionals must be prepared to address the new and emerging risks to these evolving business strategies”.
Shifting from managing information security to managing the provider of that security can be a leap. Security professionals must now learn how to obtain answers from third-party providers, not just provide answers themselves. Some of the most important information they need to obtain is the level of visibility they will have into the design, implementation, and operation of their cloud provider’s infrastructure.
As illustrated by the Amazon EC2 outage in June that took down high-profile services like Netflix, Instagram and Pinterest (and the more recent outage in October), it’s important to determine a cloud provider’s business resiliency capabilities (i.e., command and control, business continuity, disaster recovery, and incident response). It is also important to discover how they handle a deliberate denial-of-service attack, what service guarantees are offered, and how fully integrated risk management is into their core business processes and governance.
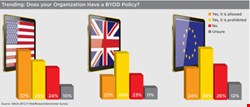
BYOD Accelerates the Evolution
On the mobile side, the rise of Bring Your Own Device (BYOD) is not the only driver of change, but it may be the most irksome. Half (50.5%) of information technology leaders in the US believe that the risks of BYOD outweigh the benefits, according to the 2012 IT Risk/Reward Barometer survey conducted by ISACA. Close to one in three (29%) enterprises prohibit BYOD. When asked to rank a range of employee activities as high, medium or low risk, a large number of respondents chose losing a work-supplied smartphone or downloading content on to it as high risk.
Like cloud computing, mobile device use is driving a bigger emphasis on process and people and a shrinking focus on technology. One illustration of this shift is the evolution away from mobile device management (MDM) to mobile enterprise management (MEM), which encompasses both MDM and mobile application management software. The importance of the device, or technology, is retreating compared with the overarching issue of managing mobility in relation to the enterprise.
Time to Rebrand
In today’s threat landscape, information security must go hand in hand with information risk. Yesterday’s ‘information security’ job title needs to change to ‘information risk and security’. Those who don’t fully embrace information risk are missing out on a major piece of alignment with enterprise goals.
Technology skills will still be important, but more to support execution of security processes once enterprise risk tolerance and risk profiles have been established. This aspect of the evolving role requires that these new information risk and security professionals venture into parts of the organization that may seem like foreign territory: enterprise risk management and the legal department. Like the rise of cloud and mobile computing, this shift requires the ability to think and act like a business consultant, not a technologist.
| "Security professionals must be prepared to address the new and emerging risks to these evolving business strategies" |
| Erik Friebolin, Verizon |
“Security risk management’s evolving role of enabling the business requires intimate knowledge of, and support for, business goals,” says Jeff Spivey, international vice president of ISACA and director of Security Risk Management Inc.
“Security professionals have so much to offer in providing value and increasing profit through a more mature risk management process”, he asserts. “Change management, culture, monitoring of risk, mobility and BYOD all demonstrate the accelerated pace of risk due to new and better technologies. The secret is in establishing the correct framework to understand and manage new and evolving risk to the enterprise.”
Culture and Communication
End users can be a highly effective force multiplier when it comes to managing information risk and security. They are also an unstoppable force. So, as today’s risk and security professionals embrace cloud computing and mobility, they should also focus on educating employees instead of fearing them.
Understanding corporate culture, human behavior and effective communications will help enormously. Risk and security professionals should assist users in understanding enterprise expectations and concerns. Appeal to their personal motivations to drive adoption of secure behaviors around cloud, mobility and related technologies. And, if you don’t think you need to educate employees on safe cloud use, ask yourself how many of them have signed up for a Dropbox account or are using Google Docs without IT guidance or permission.
When communicating with management, risk and security professionals should avoid the FUD (fear, uncertainty and doubt) approach and opt instead for case studies and scenarios that help demonstrate realistic and material concerns about business impacts. These professionals should also stop using the word ‘risk’ if what they really mean is the narrower topic of ‘threat’ or ‘vulnerability’. To talk credibly about enterprise risk requires insights into business strategy, financials, operating conditions and direction. What security professionals can contribute to that conversation is valuable threat and vulnerability input values that aid in calculating overall business risk.
From Prohibition to Policy-setting
With the consumerization of information technology, it makes little sense to prohibit mobile device use or severely restrict cloud use. But employees do need guidance and parameters. That is why policies and standards continue to be the backbone of a robust information risk management and security program.
However, policies need to be updated to account for unique cloud and enterprise device management requirements. They also need to be pragmatic, reasonable to the intended audience, and sustainable. This relates back to the need for communication skills and an understanding of corporate culture. Policies that are meant to influence employee behavior, but are designed by security professionals who lack this understanding, simply will not succeed.
“A challenging but critical task for security professionals is to correlate policy, culture, organizational matters, technology, information and processes under a common holistic framework such as COBIT 5 for Information Security”, says Christos Dimitriadis, head of information security for INTRALOT GROUP. “It provides practical guidance and helps security professionals communicate in the appropriate business language.”
Establish Control Objectives and Requirements
The information risk management and security professional should identify and govern control objectives, whereas the identification and operation of controls should be left to the data, process, and/or control owners. This allows for a more efficient and effective operating model, avoiding issues associated with operating outside of a group’s expertise or responsibility (e.g., the information security group owning operations for technical controls instead of IT operations).
The evolving role of the risk and security professional requires a shift in their activities associated with controls to establishing expectations among business stakeholders that these controls exist and operate properly, defining concepts and requirements (instead of detailing technologies and operational activities), providing insights into expected outcomes, and allowing operational personnel to define how to meet these outcomes. In short, it’s not that risk and security professionals should stop working with controls – but they should up-level what the focus of that work is.
Checklist of New Skills
The evolution from security professional to information risk and security professional requires the development of several related competencies, especially because this broader role requires greater partnership with the business side of any organization. These skills include:
- Business knowledge
- Information risk management
- Information governance
- Consulting and advisory
- Compliance
- Privacy
- Metrics and data analytics
- Change management
- Communications
- Organizational behavior and psychology
Prepare for the Evolution
No security professional can transform his or her skills, or career path, overnight. Nevertheless, there are plenty of resources available – many at no cost – to help guide the gradual evolution from technologist to advisor. A few recommended components include: professional certification (such as CRISC, CISM or CISSP), which assures stakeholders of subject matter expertise and a level of hands-on experience; attendance at industry events and association meetings, both to acquire knowledge and to network with peers; and mentorship – identifying and learning from a security professional who has already evolved to take on an advisory role and integrates security with risk management.
As the rate of change continues to accelerate, access to professional resources is crucial to understanding and adapting risk management options and risk models. This mix balances factual information that can be learned from reading an article or PowerPoint slide with ways that someone can acquire those softer skills, such as consulting and communication, which can’t be learned from a book.
In this era of cloud computing and mobile device use, the role of the security professional has to change. The traditional and obtuse ‘magic happens here’ approach to information security needs to be discarded in favor of embracing change and collaborating across the organizational chain. Technology is no longer enough. Only people can prevent data breaches.
John Pironti, CGEIT, CISA, CISM, CISSP, CRISC, ISSAP, ISSMP, is an advisor with ISACA and president of IP Architects LLC.