
The current vectors of threat posed by cybercrime, industrial espionage, and hacktivism have driven many organizations to invest in and deploy data loss prevention (DLP) solutions to protect corporate assets and intellectual property. Research and experience, however, has shown that the approach adopted today by some organizations – including banks, large corporates, charities, telecommunications providers, industrials and governments – can suffer from serious security gaps. Often, expectations and investment in DLP actually realizes a very low return on investment, manifesting in dangerous opportunities that support the potential illicit egress of sensitive assets.
Of more concern in these situations, given the deployment of a solution, is that there is a natural perception that security is fully accommodated – the worse possible place to be, in suspension with unknown exposure.
There is a selection of culpable shortfalls, responsible for what can be lackluster delivery of a critical solution, the first of which is shared between those who consult and supply and, of course, those who procure and deploy. Number two is the segregated silos of operations that can exist within both the business and technology alike, which – at times – suffer from a lack of communication. The third is what may be described as system administrators, who suffer from technological tunnel-visioning, only seeing what sits within their individual comfort zone. The last – the misconception that the business is there to support security – is, of course, actually the reverse.
Didn’t I Say that I Love MS Office?
Let’s commence with Microsoft’s Office 2010, and understand what levels of insecurity this set of tools can bring to the table. Now I personally love Office 2010, because it enables productivity and collaboration. But the snag is – in pure security terms – unless deployment has been planned with security in mind, it can come with baggage, punching holes through your secure perimeter.
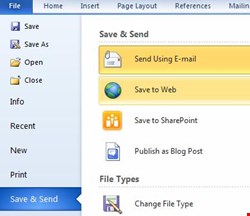
In fact, it is the very objective of Office 2010 to be collaborative, which introduces opportunities for data leakage. One feature of concern includes ‘Save & Send’ (see Fig. 1), allowing the user to place content directly into their personal cloud space from Word, Excel, or any MS Office application. Then there’s a feature that supports blogging direct from Word, to Blog, and all from the office computer. Not to mention the functionality to write directly to a cloud-based SharePoint implementation. These are all common finds in today’s protected DLP environments, supporting unauthorized movement of data right under the sniffing corporate nose.
Then we come to the sweetest tool of all for illicit sharing of data; that is, the derivative of what was MS Groove, now manifesting as SharePoint Workspace. It is just a simple matter of setting up and running a remote Workspace, made even easier with the use of the MS Public Directory of users. Now just Drag-and-Drop the content you desire to share (export), and as if by magic, it replicates to all subscribed external systems. It can work in a bidirectional fashion and is a great out-of-band feature that may be leveraged (see Fig. 2).
To continue the theme of using supplied desktop tools, while the next application has been around for many years, for some reason, it seems to be a well-kept secret. Have you heard of ‘Iexpress’? If not, as an introduction, here it is shown in Fig 3. Failing that of course, just open up ‘Run’ and enter ‘Iexpress’ and there you have it.
A tool that may have been supplied to every user build as part of the operating system – a packaging tool that enables the building of self-extracting applications – can run scripts, and for free. It can also provide some useful functionality to the developer. For the rest, this can introduce the prospect of insecurity, and can be a great tool for introducing malware.
Conversations
Now the humble printer’s turn. Do you remember when printers sat in the corner and just printed? Well things have changed, and these big ink-beds now arrive in the form of the multi-functional device (MFD), a full-fledged computerized, intelligent printing press.
They come equipped with on-board memory, print server, and a local, accessible hard drive of around 360 GB, potentially retaining all that sensitive and PCI DSS-related data. In fact, in the worst case I am aware of, after a contamination of a MFD with high-grade protectively marked government information (in fact, secret), the compromise was considered too difficult to deal with and expectations were that overwriting it would eradicate the unauthorized exfiltration of data. It was a dangerous approach, given the device in question was leased.
In the area of security skills – and having a robust and workable grasp on understanding technology and infrastructure – I would also like to consider exposures underpinned by insecure SAMBA implementations. Now, as most informed readers will know, these are big fat shares, and when resident as a recipient hub for corporate data, PCI-DSS, and other such sensitive information assets, can serve up a great opportunity for compromise and data leakage.
However, on at least two occasions – notwithstanding the logical environments had been subject to audits and penetration testing – at the center of the operational world, such insecurities languished. I find this truly amazing. In fact I will close this particular observation with a real-time, real-world discovery on the site of a global brand, where such accommodation of insecure infrastructure provided unfettered external access to content of a most disturbing profile, storing very unsavory images of a criminal nature.
One area we can’t avoid is that of low-cost cloud, and here focus will be on two technologies I actually love – but which, when it comes to security, can be a nightmare. The two examples are ‘PogoPlug’, and ‘Tonido’, two imaginative toys that if subject to miscreant use, they make data sharing, export, and theft very easy to accomplish.
| "If you are embarking on a DLP project…ask the question: Where could my information assets leak from?" |
Basically, both these sexy little technologies are placed in the area of low-cost cloud, offering around 5 GB for free, and the opportunity to increase storage capacity. However, they really come into their own with the sort of NAS-like capabilities, which may be accommodated from a home-based plug. By simply registering some personal cloud space, installing a PogoPlug in your home, connected to a broadband router, to which say, a 2-TB drive is attached, there you have it – data from the corporate setting to home at the click of the mouse, again facilitating bidirectional capabilities. In fact, having now set up such a device, and successfully testing it from a number of corporate sites, I can confirm that when it comes to DLP solutions, some do not see the office-to-home conversations.
And it’s not just about the technology. One worrying case I am aware of is where Protectively Marked information was released into the public domain under the Freedom of Information Act (FOI). Notwithstanding that the subject matter was declassified, there was no consideration given over its potential to implicate, or provision intelligence to its new readership for target selection – but it did, and by virtue of its content, provided a link between a security services operation to an obscure facility that would not normally be privileged with such an association. Nevertheless, it was serving up a much increased level of risk to every civil servant and employee, not to mention their collocated, unaware neighbors. But even more worrying, when this was reported to the head of security, no action was taken.
I Could Write a Book about this, But…
I have limited space to fully justify this topic, and will never even get to introduce the security relationships of mobile computing, home servers, virtualization, DNS, WiFi, and micro-imaging, let alone metadata, but I think you get the point. Thus the conclusion is simple, and while the aforementioned areas may not all be present in your operations, I can personally qualify they are common finds from across many sectors that you would not normally associate with such levels of insecurity.
So let us eradicate the approach that can be taken for DLP, which on occasion can be a ‘silver-bullet’ solution based on a point-and-click installation of a purchased application, and deal with DLP as a corporate-wide technology and business strategy.
If you are embarking on a DLP project, don’t just focus on the capabilities and expectations set against the tool of choice, but look to the spectrum of the enterprise, and ask the question: Where could my information assets leak from? Also apply an open mind and seek out the real opportunities for insecurity, including the user desktop, infrastructure, and the interface to the interconnected world of the internet. Then with a broad brush of savvy, you may just find that you can get a little closer to securing the enterprise – but even then, don’t take it for granted. Continue to employ a watchful eye over what functionality and access users are provisioned with in the future.
| John Walker is the CEO of Secure-Bastion and a visiting professor at Nottingham Trent University. Walker is a fellow of the BCS and holds numerous certifications, including: CITP (BCS), CISM CRISC (ISACA), and UK Government ITPC. He is chair of the London ISACA Chapter Security Advisory Group (SAG), an ENISA CEI-Listed Expert, and editorial board member of Cyber Security Research Institute (CSRI). |