Cyber attribution is a sensitive subject, not least because of the potential political fallout. Even when cybersecurity experts observed an explosion of wiper malware attacks targeting Ukraine during the current conflict, many did not venture to point the finger directly at the Russian state.
Even the HermeticWiper malware which was launched on February 23, 2022, one day before the Russian invasion of Ukraine, has still not been formally attributed.
For many threat intelligence analysts, however, attributing cyber-attacks is fundamental to defending against them.
Strategize and Predict Future Attacks
First, many argue that attribution is valuable for the victim’s immediate incident response.
“Attribution really matters because it allows you to think about how you can best strategize and predict future attacks,” Alex Leslie, a cyber threat intelligence researcher at Recorded Future, summarized on Infosecurity’s February 2023 podcast.
Cybersecurity firm Trend Micro explains in a blog that attribution can help identify if victims are a target or collateral damage, better understand the tactics, techniques and procedures (TTPs) used during an attack to enhance detection and response, and help the board see the investment value in new security tools. say in literature posted
According to Feike Hacquebord, a senior threat researcher at Trend Micro, some of his peers’ reluctance to discuss attribution comes from the confusion between technical attribution, which consists in identifying sets of threat activity and analyzing patterns, and legal or political attribution, which links these sets to nation-states – and can sometimes lead to the prosecution of individuals.
“When we talk about attribution at Trend Micro, we’re only referring to technical attribution, devoid of legal or political purposes. The primary role of cyber threat intelligence (CTI) teams is analyzing intrusion sets, not groups or people.”
On the other hand, Mandiant, now part of Google Cloud, does not refrain from including state affiliation in its attribution process. However, Shanyn Ronis, a senior manager in Mandiant's threat intelligence team, told Infosecurity that understanding how an adversary operates and being able to anticipate what they do and how they might shift their TTPs over time is more important than understanding who is on the other side.
“Let’s say you’ve blocked an attack and remediated it or contained it – how do you guarantee that you’ll be able to block them again if they come after you in a different way? The best way to do that is to get some degree of knowledge,” Ronis added.
Cross-Checking Data
To acquire this knowledge, Jamie Collier, an EMEA senior threat intelligence advisor at Mandiant, explained: CTI analysts need first to work hand in hand with incident response teams to identify two types of data: evidence on the ‘crime scene’ (who has been targeted by an attack, what devices have been accessed by third parties, which part of the system has been infected, what the indicators of compromise (IOCs) are, etc.), and intelligence about the perpetrators (what their TTPs are, what tools they are using, what infrastructure they are using, what level of sophistication is the attack on, what their motivations can be, etc.).
"The biggest shift in cyber attribution was the emergence of the ransomware groups. Now, it's a much more fluid criminal ecosystem, with groups merging and disbanding and threats coming and going."
Second, they start joining the dots with the threat intelligence data they have.
According to Feixiang He, an adversary intelligence research lead at Group-IB, this data includes:
- First-hand attack indicators collected by digital forensics and incident response experts or managed extended and response (XDR) solutions
- Proprietary telemetry
- Attack technical data reported and shared by the cyber security community, including threat reports
- Threat actors’ activities uncovered by CTI teams, such as discussions on the underground forums, illicit trades, recruitment, and information about personal preferences (political, linguistic, time zones…)
- Open-source information
- Closed source financial information available to law enforcement.
“CTI teams cross-check data from various attacks and operations to unveil similarities and patterns. When enough knowledge is acquired for a set of cases, CTI teams will organize such discoveries under a given profile, that will be given a code name,” He said.
This code name is made of combined identification elements referring to the TTPs the threat actors use, their motivations, their targets, or their alleged origins, depending on the vendors’ policies and naming conventions.
Temporary Attributions
While each vendor has its own attribution process, one thing is common to all: it can take months, if not years, to identify a specific threat group behind an attack or a series of cyber incidents.
This tampers with the victim’s benefit of attribution, making it difficult to action CTI insights in the short-term incident response.
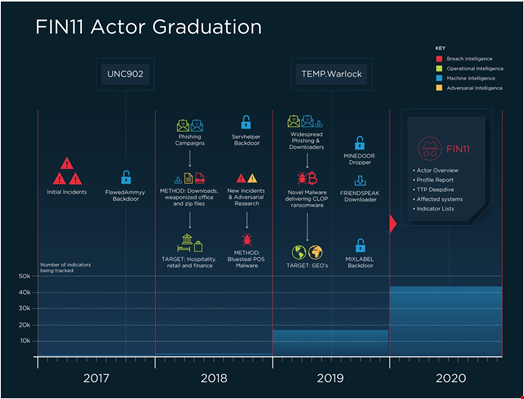
One of the workaround techniques to overcome this challenge is to use temporary naming codes. Mandiant, for instance, first attributed an ‘Uncategorized’ – or UNC – codename to a cluster of threat activity. Then, when they gain more knowledge about who is behind the activity, they can move to a ‘Temporary’ codename –TEMP – and then on to giving it a definite identity, Advanced Persistent Threat (APT) number for a nation-state actor and a Financial number (FIN) if they are financially motivated.
For instance, the threat activity named UNC902 was then attributed to TEMP.Warlock, who finally became tracked by Mandiant under the FIN11 codename.
Microsoft uses a similar process, attributing a temporary DEV number, which stands for 'Development group,' for clusters of threat activity they haven't fully identified yet.
A Game of Cat and Mouse
Another challenge for CTI analysts is choosing the right time to publish their findings, and how much to share.
“The downside of public threat reports is that the threat actors learn the tracking techniques and conduct counterintelligence activities by changing their tactics, toolset, and infrastructure. Some of them can be very quick in adjusting and fixing bugs,” Group-IB’s He said.
For Mandiant’s Collier, threat actors are increasingly doing that anyway, threat reports or not.
Chris Morgan, a senior cyber threat intelligence analyst at ReliaQuest, told Infosecurity, “Because cyber criminals are much brasher about what they did and what they want, and the nation-state groups much more covert, it’s been more difficult to attribute nation-sponsored cyber-attacks than financially motivated ones,”
However, this threat landscape has now changed a lot, Collier argued: “The biggest shift in cyber attribution was the emergence of the ransomware groups. Now, it’s a much more fluid criminal ecosystem, with groups merging and disbanding and threats coming and going.”
He agreed and added that the cybercrime-as-a-service business model that ransomware groups have introduced and perfected over the years means that “digital crime is very interconnected these days.”
Additionally, the confusion ransomware groups have managed to cause seems to influence nation-state threats actors, who now “tend to imitate each other’s behavior to throw CTI researchers off track,” He said.
“For instance, Lazarus, which is believed to originate from North Korea, added specific debugging symbols and strings containing Russian words to a module designed to proxy network traffic.”
As a result, attribution has become more time-consuming but also “expires more quickly. It means that threat intelligence users need to be served up much more quickly, as well. That’s why we now tend to skip the ‘temporary’ step and jump straight from UNC to a final identification,” Collier noted.
The increased overlap between threat actors with different motivations, accelerated by the war in Ukraine, could potentially have an impact on change how cyber incidents are attributed.
This article is the first part of a three-part cyber-attribution series that has been published on Infosecurity’s website.
Part 2 - Threat Intelligence: Do We Need A 'Rosetta Stone' of Cyber Attribution?
Part 3 - Threat Intelligence: The Role of Nation-States in Attributing Cyber-Attacks
