As we stated in our Top Ten facts about the Atlanta ransomware incident, the variant which hit the city was the SamSam ransomware.
While this ransomware has been persistent for around two and a half years, few malware analysts have been able to get a handle on a sample due to several factors:
- It is very targeted and typically only one effort to infect is made every day
- It has the ability to delete itself and all traces of the encryption process is interrupted
- It has an encrypted payload which only decrypts when delivering the payload into memory
This week, Infosecurity was given the opportunity to learn more about this ransomware when researchers from Sophos got their hands on a sample of it. What was particularly interesting was its findings on how manually operated this ransomware is, and it not being a “fire and forget” style of attack.
Speaking to Infosecurity, Peter McKenzie, global malware escalations manager working in Sophos technical support, said that in comparison to other campaigns this is manually controlled and access begins with the attacker using stolen credentials, likely bought from Dark Web stores, to access remote desktop protocols and using tools to elevate privileges and gain domain access rights. This then allows the attacker to not only drop the payload on the network and begin encrypting files, but also then clean up traces of the infection when they are done.
“They can kill the process and delete files so it is hard to analyze, and version three that they moved to in October uses an encrypted payload and decrypts into memory,” he said. “This decrypted version then just runs in memory, so getting hold of files is very hard as when you do get hold of one, you need the password.”
McKenzie also said that Sophos had seen the payload extension name move from .berkshire to .satoshi and finally to .sophos. He suspected that the first name was deliberate, as it is the next county to the Sophos headquarters in Oxfordshire, while the latter would suggest that the attackers were aware of the analysis.
So how did they manage to get hold of a sample? McKenzie said: “By working with other vendors and a lot of searching and getting the password to decrypt it, it was very difficult.”
The Sophos research found that SamSam is so targeted that each payload has a unique password, and encrypted fields have a unique key for each machine, and a public key for each machine for the attacker to enable multiple pricing options.
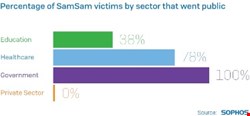
It was clear that the attackers were specifically targeting certain people or organizations, and McKenzie said that the purchasing of credentials on the dark web showed this was the case, and also in only making one targeted attack a day. Research showed so far that healthcare, government and education had been hit, but it was not clear how many in the private sector had been impacted. The most payments received was in December 2016 when 19 payments were received, while the average was six payments a month over the course of the past year.
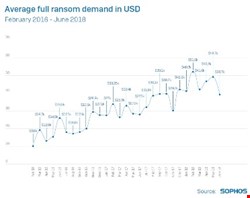
Another key factor of the SamSam ransomware is the money it has been able to generate. The Sophos research determined that it had collected around $5.9m in the two and a half years of operation, where a maximum payment was $64,000.
“For most ransomware, GandCrab’s most common charge is $1200 while for SamSam a normal ransom payment is $40-50,000, so this is much higher than normal” McKenzie said.
“We believe the people behind this are a small group and this is not an insignificant amount of money and the amount changing hands is going up, and will keep making money in the immediate future.”
Once the attacker is inside, Sophos found that they are able to use PsExec to move around and mimikatz to spread to other servers. In terms of detection, McKenzie said as this has not been part of a mass campaign it has been off the radar of most file detection, but he believed that limiting remote desktop protocols to local privilege and not blocking PsExec could help potential victims from being infected.
Without the capability to do detection because of its sophistication, the fact that Sophos was able to capture and analyze to this level is commendable. SamSam has been proven to be a particularly tricky piece of malware in its capability to spread and encrypt, and in particular encrypt data files that are not essential to the operation of a Windows PC, which are not commonly backed up.
“The attacker is very good at covering their tracks and appears to be growing increasingly paranoid (or experienced) as time passes, gradually adding more security features into his tools and websites,” the Sophos research claimed.
It seems that we are faced with an adversary very determined to hit a target that they can extort a lot of money from. The emphasis to end this may be on the user’s security hygiene rather than on the security vendors being able to detect and block this for now.
