The year 2022 was unprecedented in terms of wiper activity, with the emergence of at least twelve new families of info-destroying malware, many of them linked to the Russian invasion of Ukraine.
Some wipers had a significant impact, such as AcidRain, which shut down thousands of KA-SAT modems from satellite communications provider Viasat in Ukraine on February 24, 2022. However, most of them were observed to be using the same basic techniques or overwriting files or critical components of the operating system (OS), such as the Master File Table (MFT) and the Master Boot Record (MBR) – and sometimes a combination of them.
When Or Yair, a security researcher at SafeBreach, started investigating wiper development in the middle of 2022, he wanted to surprise people by “creating a next-generation wiper.” His approach was counter-intuitive: using security controls, and particularly endpoint detection and response (EDR) solutions as the wipers. His research led him to create Aikido, a wiper that exploits 0-day vulnerabilities in EDRs, which he showcased during Black Hat Europe in London in December, 2022.
In case you missed my talk in Black Hat Europe today, you can now read about the research in our latest blogpost https://t.co/d1UtrUI9jt @safebreach
— Or Yair (@oryair1999) December 7, 2022
“Because of their anti-malware purpose, EDRs are necessarily granted high privileges on a machine, and they have the capacity to delete files. Also, even as unprivileged users, we still have a certain amount of control over them,” Yair explained to Infosecurity.
Junction Points and TOCTOU Vulnerabilities
Before building a wiper malware, Yair needed to develop a technique to confuse EDR solutions to delete legitimate files. He came up with the idea of using junction points, one of the three linking mechanisms, with hard links and symbolic links (symlinks), to associate files, directories and volumes in Microsoft Windows.
“Junctions are specifically designed to create shortcuts to access directories. They are particularly interesting here because, unlike hard links and symlinks, they don’t require administrator’s privileges,” Yair added. This unwanted feature has been coined ‘Improper Link Resolution Before File Access’ and several corresponding vulnerabilities can be found under the Common Weakness Enumeration number 59 (CWE-59).
To confuse the EDR, Yair would create a ploy malicious file using the Mimikatz open source malware program and install it on the target device, mimicking a legitimate file’s name, thus triggering the EDR to detect it. He would then delete the folder containing the malicious file and replace it with a junction leading to the target file.
In this scenario, Yair would need to operate within a short window of opportunity between the detection and the deletion of the file, exploiting what is commonly referred to as a time-of-check to time-of-use (TOCTOU) vulnerability.
Yair tried his method with seven different EDR solutions. “They all failed, either because the EDR saw that the malicious file was already deleted or because they deleted it before I could replace it with a junction,” Yair recalled.
Handle Catching and Forcing Reboot
Yair was not deterred. Instead, he persevered with an idea to extend the window of opportunity and allow himself to replace the ploy file with a junction link: using a technique called ‘handle catching’ in order to force a reboot.
“Whenever a file is created or opened on Windows, a program creates a handle for that file. What I did is I didn’t close the handle of the malicious files, thus triggering file-sharing mode that will prevent the EDR from deleting the file automatically,” Yair explained.
The goal is to force the EDR’s deletion process to fail and the EDR software to ask for a reboot, which would give the researcher enough time to replace the ploy file with the junction point linking to the target file. Once this is done, Yair could reboot the device, and the EDR should try deleting the ploy file, but instead follow the junction’s path and delete the target file.
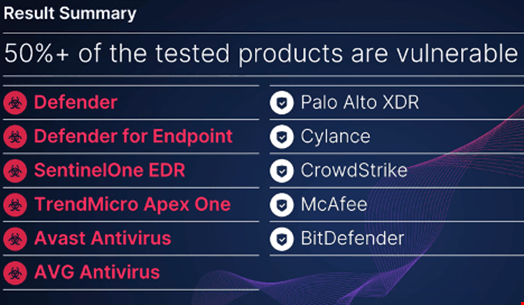
This method was successful with six out of the seven EDR solutions Yair tested: Microsoft Defender and Defender for Endpoint, TrendMicro Apex One, Avast Antivirus and AVG Antivirus and SentinelOne EDR. Of note, the two Microsoft products were only able to delete the directory, not the file itself.
“It means that around 50% of products in the EDR market are vulnerable, and three of these five vendors are very high on the Gartner’s Magic Quadrant for Endpoint Protection Platforms, which makes it even more worrisome,” Yair said.
Recovery Tools Unsuccessful
All that was left was to develop the Aikido wiper, equipped with malicious files and that’s able to install them, keep the handles open so as to make the EDR ask for a reboot, replace them with junction points and let the device reboot to allow the EDR delete the target files.
Yair tested it on SentinelOne EDR and Microsoft Defender and Defender for Endpoints – and it worked. “The Aikido wiper was undetected, running with unprivileged permissions and able to wipe important data,” Yair concluded.
The researcher also enabled his wiper to fill free disk space to avoid triggering the users’ attention.
“Finally, I used two popular recovery file tools, Cleverfiles Disk Drill and CCleaner Recuva to see if someone could get their files back this way, and they didn’t work.”
With this proof of concept, Yair reached out to all five EDR providers, who “were very cooperative,” he added.
Microsoft wrote to Yair and said: “The fix in development for your report has completed testing and is tentatively scheduled to be released in the upcoming Defender Release later this month. We propose to disclose that fix on the October 11[, 2022] ‘Patch Tuesday’ with the other security releases under CVE-2022-37971.”
Gen Digital, owner of both Avast and AVG antiviruses, told him: “On October 20, 2022, Avast released an update (to version 22.10) to address an issue that was discovered in the malware removal functionality of Avast and AVG Antivirus versions 20.5 up to 22.9 [CVE-2022-4173]. Users of the affected versions have received an automatic update.”
Trend Micro also investigated the issue and fixed the vulnerability in their Apex One EDR (CVE-2022-45797).
“SentinelOne sent me a fixed version to test, but I have not been able to get a CVE number from them,” Yair explained.
With this proof of concept, Yair also wanted to warn all EDR providers, especially those he hadn’t tested, such as Palo Alto Networks, BlackBerry’s Cylance, CrowdStrike, McAfee and Bitdefender, among others, to check and patch the same vulnerability.
“There is a good chance other EDRs and antiviruses are vulnerable too. This experiment is proof that security controls can be diverted from their original purpose and used as a point of entry for executing malicious software,” he said.
SentinelOne was contacted by Infosecurity but did not respond to requests for comment on this issue.
