Throughout 2024, police forces and law enforcement agencies worldwide have been exceptionally active, tackling a range of high-profile operations and cybercrime takedowns.
The year started with Operation Cronos, which some cybersecurity experts called the largest anti-cybercrime operation in history, with the FBI, the UK’s National Crime Agency (NCA) and partners taking down the infrastructure of LockBit, one of the most active ransomware groups.
The year concluded with Operation Destabilise, a groundbreaking effort also led by the NCA. This operation successfully disrupted a multi-billion-dollar Russian money laundering network with ties to drugs, ransomware, and espionage.
In between, law enforcement took down botnets, infostealers and one of cybercriminals’ favorite encrypted communications platforms.
Here are Infosecurity’s top 10 operations for 2024 – in chronological order.
NCA and FBI Lead LockBit Takedown with Operation Cronos
The UK's NCA teamed up with the FBI, Europol, and others to take down the infrastructure used by LockBit, which was then the most prolific ransomware-as-a-service (RaaS) group worldwide.
On February 20, leaders of Operation Cronos announced they had seized many elements used by the RaaS group, including Stealbit, its bespoke data exfiltration tool, its affiliate administration panel, some source code, details on victims and extortion payments, over 1000 decryption keys and internal data, including chat messages.
The NCA added that 28 LockBit affiliate servers were taken down and two suspected affiliates were arrested in Poland and Ukraine, with over 200 cryptocurrency accounts frozen.
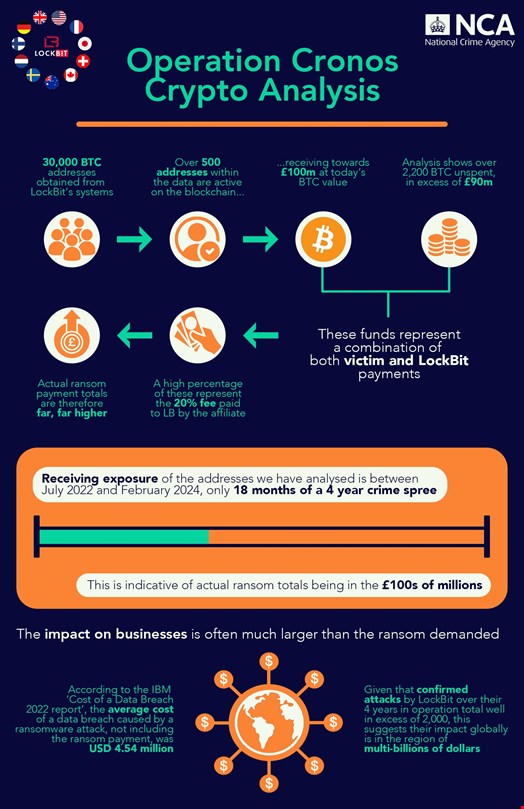
Three international arrest warrants and five indictments have also been issued by the French and US judicial authorities.
Read more about Operation Cronos and the LockBit administrators.
Two Operations Take Down Botnets and Ransomware Operations on the Same Day
Read the 911 S5 takedown story here and Operation Endgame story here
The end of May 2024 was hectic for law enforcement worldwide. In the US, the Department of Justice (DoJ) announced on May 29 the takedown of 911 S5 Botnet, a global network of millions of compromised residential Windows computers used to facilitate cyber-attacks, large-scale fraud, child exploitation and other serious criminal activity.
911 S5 was believed to be the world’s largest-ever botnet and was associated with more than 19 million unique IP addresses, including 613,841 IP addresses located in the US. Cybercriminals were allowed to purchase access to these infected IP addresses to conduct various criminal activities. The DoJ also announced the arrest of a Chinese national, YunHe Wang, 35, on charges relating to the creation and operation of 911 S5.
Across the Atlantic, Europol announced on May 30 that its Operation Endgame had taken down several significant malware droppers, including IcedID, SystemBC, Pikabot, Smokeloader, Bumblebee and Trickbot.
The global operation, reportedly the largest ever against botnets, was initiated and led by France, Germany and the Netherlands, with support from Eurojust and involvement from countries including Denmark, the UK and the US.
Additional support came from Armenia, Bulgaria, Lithuania, Portugal, Romania, Switzerland and Ukraine.
The effort involved arrests, suspect interviews, searches and server and domain takedowns. Key private partners such as Bitdefender, Cryptolaemus and Shadowserver, among others, also contributed to the efforts.
Police Swoop on Black Axe Cybercrime Syndicate in Operation Jackall III
On July 17, Interpol said it had struck a significant blow against several West African cybercrime groups, including the notorious Black Axe syndicate.
The police agency said Operation Jackal III ran from April 10 to July 3 across 21 countries on five continents, resulting in 300 arrests and the seizure of assets worth $3m.
In addition, police identified 400 suspects and blocked more than 720 bank accounts.
Black Axe is believed to have been in operation for decades. Although it is involved in various criminal enterprises, it has made significant sums in romance fraud, business email compromise (BEC) and other financial crimes.
Read more about phase I and phase II of Operation Jackal
Prolific DDoS Marketplace Shut Down by Operation Power-Off
The NCA announced on July 23 that it had infiltrated and taken down DigitallStress in collaboration with the Police Service of Northern Ireland (PSNI).
DigitalStress was one of the most prolific underground marketplaces offering distributed denial of service (DDoS) services.
This activity formed part of Operation Power Off, a coordinated international response that started in 2018 and targets criminal DDoS-for-hire infrastructures worldwide.
Read more about previous phases of Operation Power-Off
Europol Taskforce Disrupts Global Criminal Network Through Supply Chain Attack
The Australian Federal Police (AFP) led a successful international law enforcement operation to take down Ghost, a dedicated encrypted communication platform allegedly used for drug trafficking, money laundering, organized killings and other illegal activities.
The AFP said in a September 18 press release it managed to infiltrate the crimeware app thanks to a supply chain attack against the suspect’s infrastructure.
The creator and administrator of Ghost, a 32-year-old man living in New South Wales, was arrested.
The raid, dubbed Operation Kraken by the AFP, involved eight other law enforcement agencies worldwide and was coordinated by OTF NEXT, a Europol international taskforce.

OTF NEXT was led by the FBI and French Gendarmerie and included the AFP, the Royal Canadian Mounted Police (RCMP), the Swedish Police Authority, the Dutch National Police, the Irish Garda Síochána and the Italian Central Directorate for Anti-Drug Service.
Operation Magnus Takes Down Redline and Meta Infostealers
On October 28, a global law enforcement operation, Operation Magnus, successfully disrupted the infrastructure for the Redline and Meta infostealers, malware tools used by cybercriminals to steal sensitive personal data.
Authorities shut down three servers in the Netherlands and seized two domains, rendering the malware non-functional and unable to steal new data from infected victims.
Additionally, a database containing thousands of Redline and Meta clients was retrieved. Investigations into these criminal actors are ongoing.
One alleged administrator, Maxim Rudometov, has been indicted in the US and accused of managing the Redline infostealer infrastructure and laundering payments through cryptocurrency accounts. Two suspected customers were also taken into custody in Belgium, though one has since been released.
Several Telegram accounts used to distribute the infostealers have been taken down as part of the operation.
The operation was prompted by a tip sent to law enforcement by cybersecurity company ESET in 2023 about servers in the Netherlands relating to the malware.
Operation Serengeti Disrupts $193m African Cybercrime Networks
On November 26, Interpol revealed details of its latest pan-African operation, which it said led to the arresting of 1006 cybercrime suspects and the dismantling of 134,089 pieces of malicious infrastructure.
Running from September 2 to October 31, Operation Serengeti involved authorities across 19 African nations. It targeted cybercrime networks responsible for an estimated $193m in financial losses and 35,000 global victims.
Private sector partners assisted Interpol with on-site support through intelligence sharing and help with patching vulnerabilities and other cyber-resilience efforts for critical infrastructure. The operation focused on ransomware, business email compromise (BEC), digital extortion and online scams.
Global Police Arrest 5500 in $400m Cyber-Fraud Crackdown
Between July and November 2024, Interpol coordinated Operation Haechi V, which involved law enforcers from over 40 countries and territories.
It resulted in the arrest of over 5500 individuals and the seizure of more than $400m in virtual assets and government-backed currencies, most likely obtained via voice phishing, romance scams, online sextortion, investment fraud, illegal online gambling, BEC and e-commerce fraud, Interpol said in a November 27 press release.
Police Shut Down Matrix Encrypted Criminal Hub
A large-scale investigation into Matrix, an encrypted messaging service used by criminals, was coordinated by Eurojust and Europol. The operation, named Operation Passionflower, led to the platform’s takedown on December 3.
The operation was executed by Dutch and French authorities on December 3, and follow-up actions were undertaken by their Italian, Lithuanian and Spanish counterparts. The main servers used by Matrix in France and Germany have been taken down as a result.
The operation also resulted in the arrest of individuals suspected of being involved in serious crimes. In France, one suspect was arrested and his house searched. In Spain, two suspects were arrested following a European Arrest Warrant from the Netherlands and six houses were searched. Six houses were also searched in Lithuania.
Operation Destabilise Disrupts Multibillion-Dollar Russian Money Launderers
On December 4, the NCA revealed the outcome of Operation Destabilise, a significant effort to unmask two previously unknown money laundering networks: Smart and TGR.
The two Russian-speaking networks are said to have laundered funds for transnational crime groups like the infamous Kinahan Cartel and helped Russian clients like the sanctioned Russia Today media company to bypass UK financial restrictions to invest money in the UK.
They also helped Russian cybercriminals, including the Ryuk group, to launder millions of dollars’ worth of ransoms paid by victims, according to the NCA.
The core of the operation focused on unmasking a complex scheme whereby TGR and Smart collected funds in one country, often via physical cash transfers on the street, and then made the equivalent value available in another – usually in cryptocurrency.

Conclusion
The year 2024 has been a landmark year for global law enforcement and cybersecurity efforts. From dismantling the infrastructure of notorious ransomware groups to disrupting sophisticated financial crime networks which support cybercriminals, these operations have showcased the power of international collaboration and advanced investigative techniques.
As cybercriminals continue to evolve, the relentless pursuit of justice by agencies worldwide serves as a beacon of hope, demonstrating that even the most elusive threats can be countered with determination and innovation.
