The past year was expected to be a watershed moment for the ransomware ecosystem, with the takedown of ALPHV/BlackCat in late 2023 and the disruption of the LockBit syndicate in early 2024.
While these law enforcement takedowns had a negative impact on ransomware activity for a while, the ransomware-as-a-service (RaaS) landscape showed its resilience.
Soon after some of the biggest law enforcement busts, activity from other established ransomware brands like Play and Akira seemed to pick up, perhaps due to affiliates moving from exposed groups, while new groups emerged.
Ransomware activity peaked in November, with Corvus Insurance analysts claiming the month saw the highest number of claimed ransomware victims in history. Other sources, like the ransomware tracking website Ransomware.live, believe no monthly ransomware claims in 2024 topped the 907 claimed in July 2023.
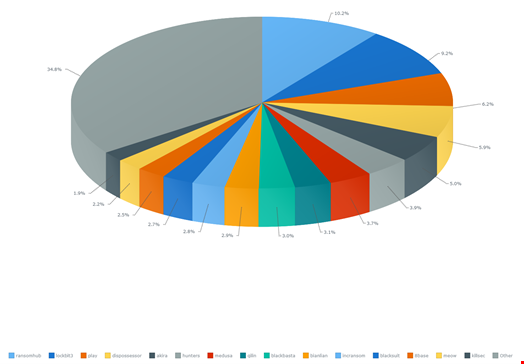
Top Ransomware Gangs of 2024
Infosecurity selected the 10 most active ransomware groups of the past year, collecting data from several sources, including Ransomware.live, RansomLook, Corvus Insurance and Recorded Future, among others.
RansomHub: Move Fast and Break Things
- Other names: N/A
- Appeared in: February 2024
- Claimed victims in 2024: 593
- Claimed victims overall: 593
On February 2, 2024, a user called 'koley' announced a new ransomware affiliate program under the name RansomHub on the Russian-language hacking forum RAMP. The split of each heist would be 90% of the value for the affiliate and 10% for the developer.
According to ‘koley,’ the RansomHub ransomware is designed to be versatile in order to compromise a wide array of platforms, including Windows, Linux and ESXi, as well as architectures such as ARM and MIPS.
In June, it was reported that operators of the Scattered Spider group, responsible for a number of high-profile ransomware incidents affecting large organizations in the past year, including MGM International, Caesars Entertainment and Okta, left the disrupted ALPHV/BlackCat to join RansomHub.
Affiliates of RansomHub overtook LockBit as the most prolific RaaS brand in October and largely contributed to a ransomware claim surge in November, with 98 claims that month alone, according to Corvus Insurance.
Play: Going Hard on Exploits
- Other names: PlayCrypt
- Appeared in: June 2022
- Claimed victims in 2024: 362
- Claimed victims overall: 716
Play Ransomware emerged in 2022 with attacks targeting Latin American entities, but the group has targeted organizations in a wide range of countries since then.
The group’s preferred mechanism for initially compromising its targets is via vulnerability exploitation, focusing on exploiting supply chain vulnerabilities in common or security software used by many organizations, such as Fortinet, Citrix and VMWare’s ESXi.
A July 2024 report by Trend Micro revealed a connection between Play and Prolific Puma, a group known for generating domains using random algorithms and offering link-shortening services to cybercriminals to evade detection.
Akira: The True Conti Heirs
- Other names: N/A
- Appeared in: March 2023
- Claimed victims in 2024: 291
- Claimed victims overall: 454
In February 2023, the Conti ransomware group dissolved following internal conflicts between pro-Russian and Ukrainian members. Quickly, several affiliates migrated to other groups, such as Royal, BlackBasta and others.
Akira is one of these groups and likely one that has more ties with Conti’s infrastructure than any other group. According to cybersecurity provider Qualys, Akira has code overlap with Conti and operators that mingled funds with Conti-affiliated wallet addresses. After the downfall of LockBit, threat intelligence firm RedSense identified Zeon as a former Conti affiliate group that has been outsourcing its skills to LockBit and Akira.
Akira affiliates also work with other ransomware operations, such as Snatch and BlackByte. In November 2024, Akira seemingly ramped up its operations, with 73 claimed victims that month alone, according to data from Corvus Insurance.
Hunters International: Building on the Hive Demise
- Other names: Hunters
- Appeared in: Late 2023
- Claimed victims in 2024: 227
- Claimed victims overall: 252
In mid-October 2023, a few days before the takedown of the Hive ransomware group, the group’s infrastructure source code was sold, along with its website and older versions of the source code.
Hunters International claimed to have bought the package and fixed the vulnerabilities that were responsible for preventing file decryption in some cases. The group also stated it would prioritize data theft over file encryption.
Medusa: All PR is good PR
- Other names: N/A
- Appeared in: Late 2022
- Claimed victims in 2024: 212
- Claimed victims overall: 357
While Medusa can be seen as just another RaaS group using traditional data extortion tactics, its online presence stands out.
Medusa’s online presence is an unusual mix of dark and clear web activities. Notably, Medusa operators run a clear web identity, ‘OSINT without borders,’ along with profiles linked to 'Robert' under various surnames, on a dedicated website and across social media platforms like X and Facebook.
Although Medusa tries to present these entities as separate, numerous connections suggest otherwise.
Cybersecurity firm Bitdefender explained, “Medusa’s official data leak site links to a Telegram channel that shares the same logo as 'OSINT without borders,' and the site’s owner frequently refers to Medusa in ways that imply a close affiliation.”
Qilin: Password Hungry
- Other names: Agenda
- Appeared in: July 2022
- Claimed victims in 2024: 179
- Claimed victims overall: 230
Qilin has been active since at least July 2022 and is also known as Agenda.
In August 2024, the group was observed by the Sophos X-Ops team to conduct en masse theft of credentials stored in Google Chrome browsers on a subset of the network’s endpoints – a credential-harvesting technique with potential implications far beyond the original victim’s organization.
This is an unusual tactic and one that could be a bonus multiplier for the chaos already inherent in ransomware situations, said Sophos.
BlackBasta: Another Conti Descendant
- Other names: N/A
- Appeared in: April 2022
- Claimed victims in 2024: 176
- Claimed victims overall: 507
BlackBasta’s core members are believed to have originated from the now-defunct Conti threat actor group, given the similarities in their malware development techniques, leak sites, and methods for negotiation, payment and data recovery.
Additionally, BlackBasta has been associated with the FIN7 threat group due to the resemblance in their custom endpoint detection and response (EDR) evasion modules and the shared use of IP addresses for command and control (C2) operations.
BlackBasta was the second most active ransomware group after LockBit in the first quarter of 2024, according to ReliaQuest data.
BianLian: Extortion Without Encryption
- Other names: N/A
- Appeared in: December 2021
- Claimed victims in 2024: 166
- Claimed victims overall: 518
Active since late 2021, BianLian primarily targets entities in healthcare and manufacturing in Europe and North America.
In a notable shift, BianLian recently moved from a double extortion scheme to one of extortion without encryption.
Rather than encrypting their victims’ assets before stealing data and threatening to publish it if they do not pay the ransom, the group is now moving straight to stealing data to motivate victims to pay.
INC Ransom: No Limits
- Other names: INC, Inc. Ransom, Lynx
- Appeared in: July 2023
- Claimed victims in 2024: 162
- Claimed victims overall: 208
INC Ransom positions itself as offering a service to its victims, claiming it makes the victim’s environment ‘more secure’ as a result of its attacks.
However, the group seems to have no limits in the entities it targets, with some of its most recently claimed victims including a children’s hospital near Liverpool, in the UK.
Notably, INC’s data leak site user interface looks similar to LockBit’s.
Palo Alto Networks researchers believe that Lynx, a new ransomware group that appeared in October 2024, is a rebrand of INC Ransom.
BlackSuit: A Royal Rebrand
- Other names: Royal
- Appeared in: April/May 2023
- Claimed victims in 2024: 156
- Claimed victims overall: 175
First detected in early 2023, BlackSuit is believed to be a rebrand of Royal Ransomware, one of the most active ransomware groups in 2022.
The US Cybersecurity and Infrastructure Security Agency (CISA) reported that one of Royal/BlackSuit’s signature tactics was to use legitimate software and open-source tools during ransomware operations.
Bonus - LockBit 3.0: The One That Got Away
- Other names: LockBit Black (for this version)
- Appeared in: March 2022 (for this version)
- Claimed victims in 2024: 534
- Claimed victims overall: 1973
Despite being heavily disrupted in February 2024 following Operation Cronos, a global law enforcement operation led by the UK’s National Crime Agency (NCA) and the FBI, LockBit remained the most active ransomware group in May 2024, according to NCC Group.
The reason for this may come from a quick response from the LockBit administrators. However, it is most likely because LockBit 3.0 was leaked in the fall of 2022 by the group's disgruntled developer. This has led many cybercriminals with no formal relationships with LockBit to use LockBit 3.0 to compromise their victims.

Conclusion
As we close the chapter on 2024, it’s clear that the ransomware landscape remains as dynamic and unpredictable as ever. The decline of once-dominant groups like ALPHV/BlackCat and LockBit has not diminished the overall threat, as new and existing players continue to adapt and evolve. The resilience of the ransomware-as-a-service model ensures that even significant law enforcement actions only provide temporary relief.
Looking ahead to 2025, the cybersecurity community must remain vigilant. The emergence of new groups like RansomHub and the shifting alliances within the ransomware ecosystem suggest that the battle against these cyber threats is far from over. Continuous innovation in defense strategies and international cooperation will be crucial in mitigating the impact of ransomware in the coming year.
