The threat landscape has been bustling in the second half of 2023, according to cybersecurity provider ESET.
In its Threat Report: H2 2023, the firm recorded many significant cybersecurity incidents between June and November 2023, a period dominated by AI-related malicious activity and the emergence of new Android spyware.
According to the report, a new economy has arisen around OpenAI API keys and the ChatGPT name during that period, luring legitimate participants and cybercriminals alike.
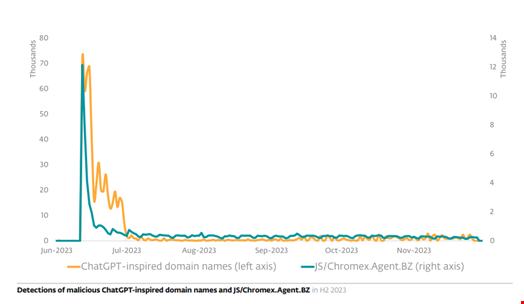
ESET telemetry in H2 2023 blocked over 650,000 attempts to access malicious domains whose names include the string ‘chapgpt’ or similar text in an apparent reference to the ChatGPT chatbot.
“While most blocks happened in June, the succeeding months saw website visitors encountering a steady stream of malicious domains superficially offering OpenAI services,” the report reads.
Read more: Cybercriminals Hesitant About Using Generative AI
Spyware Surge Amid SpinOk SDK Release
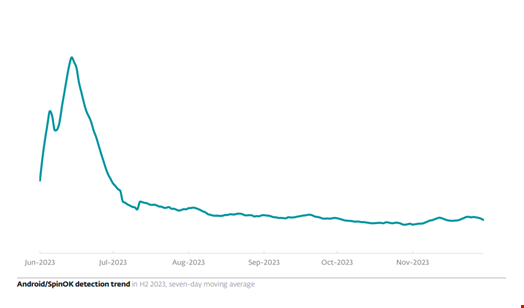
ESET telemetry reported a significant surge in Android spyware detections, rising by 89% during the second half of 2023 compared with the previous reported period.
This is due to a significant number of legitimate Android apps starting to behave as
Spyware in H2. The reason, ESET researchers noted, is a third-party software development kit (SDK) identified by the firm as SpinOk Spyware.
“Surprisingly, this SDK was incorporated into numerous legitimate Android applications, including many available on official app marketplaces. As a result, SpinOk Spyware climbed to seventh place in the Top 10 Android detections for H2 2023, becoming the most prevalent type of Spyware for the period – almost a third of all Spyware detections seen by ESET telemetry consisted of SpinOk,” the researchers wrote.
Lukáš Štefanko, a senior malware researcher at ESET, commented: “The SpinOk case serves as a reminder for app developers about the need for caution when deciding to incorporate third-party technology into their apps. It’s common for developers to be approached by third-party tech providers, but it’s crucial to evaluate these technologies thoroughly to ensure that they are secure and suitable for their apps.”
“Ensuring the security of an SDK involves a series of steps, starting with a comprehensive investigation of the provider’s reliability. This involves understanding the SDK’s functionality, examining its documentation, and, if feasible, scrutinizing the source code for any anomalies,” he added.
Štefanko also provided specific recommendations to prevent this type of threat. These include:
- Conducting a test in a safe environment before integrating an SDK into apps to assess its behavior and performance
- Using static analysis tools to unearth unwanted behaviors and potential vulnerabilities
- Keeping an eye on network traffic to spot any unexpected data transfers
- Scanning your own apps after a test integration with the third-party SDK under consideration
- Verifying whether the SDK or its provider has any security certifications or audits
- Getting feedback from developer forums or groups about the said SDK
MOVEit Ripple Effect Still Felt
The MOVEit supply chain attack had a significant ripple effect throughout H2. According to cybersecurity provider Emsisoft, the hack has impacted almost 2700 organizations at the time of writing.
It was among the most impactful events of the year's second half, ESET observed.
Jakub Souček, another ESET senior malware researcher, commented that the MOVEit hack was one of the stories that stood out the most during 2023.
“It wasn’t just the size of the campaign that made it so prominent,” he commented, “But also the technical proficiency of the Clop gang that was behind the attack. These threat actors demonstrated they can find a new zero-day vulnerability, weaponize it, and wait for the opportune moment to deploy it.”
“In 2024, we expect most of the outlined trends to continue, with current major players focusing on expansion of their affiliate programs. By employing other cybercriminals within their schemes, notable families will limit the space for the emergence of new competitors,” he added.
No Cryptocurrency Threat Trend
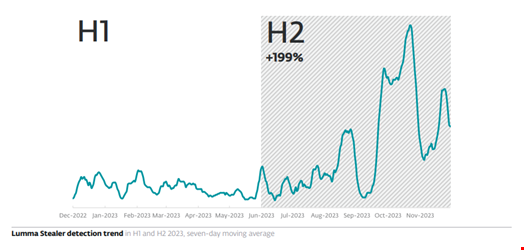
Other significant highlights observed by ESET included Magecart e-commerce cyber-attacks, botnets such as the internet-of-things-specific (IoT) Mozi and the Android TV boxes savvy Pandora, and a rapidly emerging cryptostealer called Lumma Stealer.
Finally, ESET noted that the increasing value of Bitcoin has not been accompanied by a corresponding increase in cryptocurrency threats, diverging from past trends.

