Security researchers have warned against Rafel, an open-source remote administration tool (RAT) targeting Android devices.
The investigation by Check Point Research (CPR) identified multiple threat actors exploiting Rafel RAT, including an espionage group, demonstrating the tool’s versatility in achieving different malicious objectives.
An earlier publication by CPR had already linked Rafel to the APT-C-35/DoNot Team, underlining its capabilities for remote access, surveillance, data exfiltration and maintaining persistence on targeted devices.
Through the collection of malware samples and analysis of around 120 command-and-control (C2) servers, CPR pinpointed the United States, China and Indonesia as the most affected countries. The majority of infected devices were Samsung phones, followed by Xiaomi, Vivo and Huawei.
Read more on mobile security threats: Mobile Banking Malware Surges 32%
The study also revealed that Android 11 was the most commonly compromised version, followed by versions 8 and 5. While newer Android versions present more challenges for malware execution, older versions remain highly susceptible.
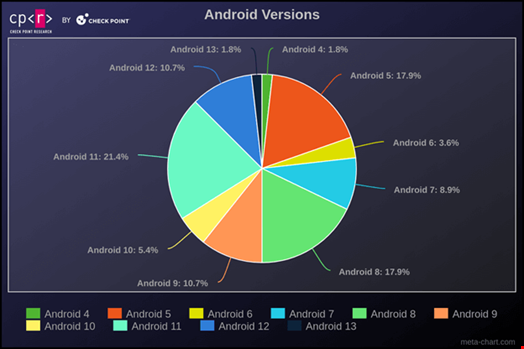
Over 87% of infected devices were running unsupported Android versions, leaving them vulnerable to attacks due to the lack of security updates.
“Neglecting software updates, especially in regions where newer devices are less accessible, exacerbates vulnerability,” warned Krishna Vishnubhotla, vice president of product strategy at Zimperium.
“Effective countermeasures must, therefore, include robust user education on recognizing threats and adopting safe mobile practices, alongside technical defenses.”
CPR’s in-depth analysis of specific cases included an Android ransomware operation, a scenario involving leaked two-factor authentication (2FA) messages and a situation where a government website in Pakistan was compromised to host Rafel RAT command-and-control infrastructure.
“The involvement of an espionage group using Rafel suggests potential national security implications,” said Callie Guenther, senior manager of cyber threat research at Critical Start.
“If critical infrastructure or governmental operations are targeted, the impact could extend beyond financial losses to include compromised national security and intelligence.”
To mitigate these risks, Android users are advised to download apps only from trusted sources, keep their software updated and use reliable mobile security apps.
“Google has gotten pretty good about making sure none of these apps get on the Play Store, or at least stay there very long,” explained John Bambenek, president at Bambenek Consulting.
“Users should never install applications based on a text message. That said, this also highlights the importance of persistently applying updates to your mobile phone to ensure that you’re running the latest versions.”
Image credit: rafapress / Shutterstock.com
