Windows Defender Security Intel has reported two major phishing attacks targeting American Express and NetFlix.
The Office 365 research teams discovered the attacks, which reportedly emerged over the weekend, hitting unsuspecting customers with well-crafted phishing campaigns that attempt to steal credit card information. According to a tweet from Windows Defender Security, “Machine learning and detonation-based protections in Office 365 ATP protect customers in both campaigns.”
Additional tweets warned, "The Netflix campaign lures recipients into giving away credit card and SSN info using a 'Your account is on hold' email and a well-crafted payment form attached to the email."
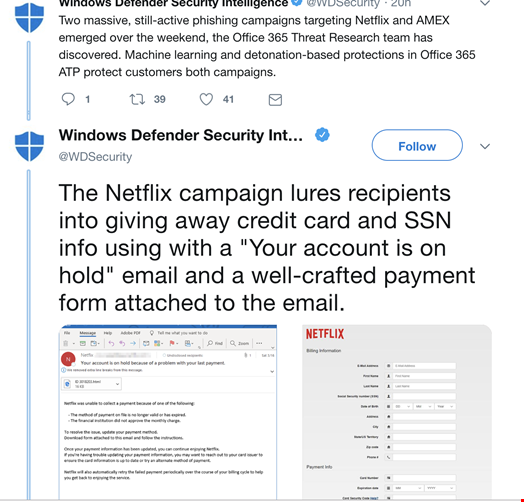
Phishing emails such as these are not only easy to craft but also easy to deploy. When aimed at unsuspecting users, they are highly successful. “They are designed to make us afraid that if we don’t click on that link or open that attachment something bad will happen,” said Colin Little, senior threat analyst, Centripetal Networks.
Cyber-criminals continue to employ the social engineering tactics of brevity and urgency, understanding that threatening user accounts or suggesting something may be amiss will evoke action.
In addition to the many places in the phishing kill chain that can keep these malicious emails away from users, Little said, “a security awareness program that trains users on how and why to identify phishing emails is both essential and fundamental. If our users are the broadest attack surface, their preparation for this attack is our best defense.”
When in doubt about whether an email is legitimate or not, an additional safety precaution is to address the potential issue in a separate dialogue. “Start a new email chain (such as to the Netflix help desk, in this example) using an address you obtain from the site,” Little said.
“Address the inquiry in a different media, such as calling their vendor support line. Or the recipient can open the applicable app (if one's available) on their smartphones and check their credit or account status.”
