Law enforcement organizations have been sharing decryptor keys with victims of the DoNex ransomware since March 2024, according to antivirus provider Avast.
In a blog post published on July 8, the Avast Threat Research Team said it had silently provided the decryptor to DoNex ransomware victims after discovering a flaw in the malware's and its predecessors’ cryptographic schema.
“The cryptographic weakness was made public at Recon 2024 and therefore we have no reason to keep this secret anymore,” the researchers wrote.
What is the DoNex Ransomware?
The first sample of what is now called DoNex appeared in April 2022 as Muse ransomware. It rebranded to LockBit 3.0 in November 2022, although it was not actually linked to the LockBit ransomware strain.
In May 2023, it rebranded again, this time under the name DarkRace, before the latest rebrand to DoNex in March 2024.
A March 2024 Broadcom-owned Symantec security advisory said the group behind DoNex had claimed companies, including US and European ones, as victims on its TOR website.
Avast says the group’s targets are primarily in the US, Italy and Belgium.
“Since April 2024, DoNex seems to have stopped its evolution, as we have not detected any new samples since. Additionally, the TOR site of the ransomware has been down since that point,” the researchers wrote.
Inside DoNex Ransomware Configuration
Samples of the DoNex ransomware and its previous versions are encrypted using an XOR cipher, a standard encryption algorithm.
During the ransomware execution, an encryption key is generated by the ‘CryptGenRandom()’ function and then used to initialize the ChaCha20 symmetric key and encrypt files. After a file is encrypted, the symmetric file key is encrypted by RSA-4096 and appended to the end of the file. The files are picked by their extension, and file extensions are listed in the ransomware XML config.
Small files (up to 1 MB) are entirely encrypted, while intermittent encryption is used for larger ones (over 1 MB). This means that the file is split into blocks, which are encrypted separately.
The ransomware also contains settings of whitelisted extensions and files, as well as requests to kill specific services.
To identify whether they have been attacked by DoNex operators, Avast advised observing the ransom note layout, as DoNex’s and associated brands’ notes look similar.
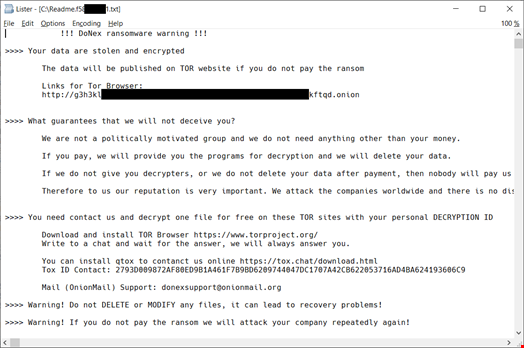
The antivirus provider provided a link to the decryptor and instructions on how to use it.
