RedJuliett, a likely Chinese state-sponsored group, conducted cyber espionage campaigns targeting Taiwan from November 2023 to April 2024, according to cybersecurity provider Recorded Future.
In a report published on June 24, Insikt Group, Recorded Future’s research team, shared its findings on the campaigns.
The hacking group compromised 24 organizations, including government agencies in Taiwan, Laos, Kenya and Rwanda.
The group also conducted network reconnaissance via vulnerability scanning or attempted exploitation against over 70 academic, government, think tank, and technology organizations in Taiwan, as well as multiple de facto embassies operating on the island.
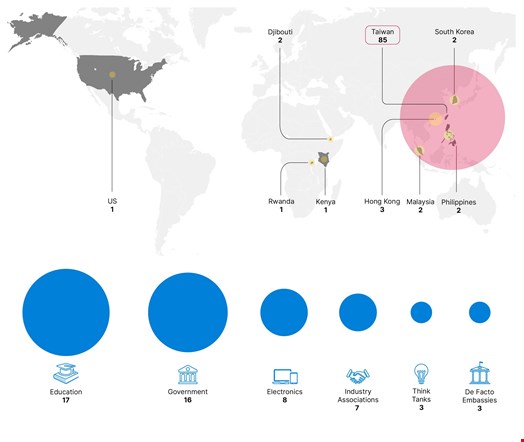
Approximately 60% of RedJuliett’s identified victim organizations were in Taiwan, with others in Hong Kong, South Korea, Laos, the United States, Rwanda, Kenya and Djibouti.
Exploiting Vulnerable Appliances and SQL Injections
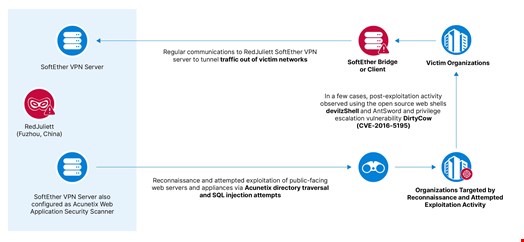
RedJuliett exploited known vulnerabilities in internet-facing appliances for initial access. These include network edge devices such as firewalls, virtual private networks (VPNs), and load balancers.
The group also attempted structured query language (SQL) injection and directory traversal exploits against web and SQL applications.
In some cases, Insikt Group researchers observed the group conducting post-exploitation activity using open-source webshells and exploiting a known elevation of privilege vulnerability in the Linux operating system (OS).
RedJuliett used the open-source VPN software SoftEther to administer operational infrastructure consisting of both threat actor-controlled servers leased from virtual private server (VPS) providers and compromised infrastructure belonging to three Taiwanese universities.
About RedJuliett
RedJuliett is a new cyber espionage group operating from Fuzhou, the capital of the Fujian province, in China.
The group’s malicious activity was first detected by Microsoft in August 2023. The tech giant said it observed a cyber espionage campaign targeting organizations in Taiwan and using living-off-the-land (LotL) techniques and SoftEther. Microsoft tracks the group under the name Flax Typhoon.
That same month, a CrowdStrike report on a group the threat intelligence provider tracks as Ethereal Panda showed very similar tactics, techniques and procedures TTPs) and the group’s use of the open-source webshell Godzilla.
“RedJuliett closely overlaps with public reporting under the aliases Flax Typhoon (Microsoft) and Ethereal Panda (CrowdStrike),” Insikt Group's report noted.
In the Recorded Future report, the Insikt Group researchers observed suspected administration activity from Chinanet IP addresses geolocating to Fuzhou, Fujian province, to multiple RedJuliett SoftEther servers.
“This traffic was consistent with established SoftEther VPN connections and interaction with an internet-exposed Acunetix login panel. While RedJuliett’s potential affiliation with either China’s Ministry of State Security MSS or People’s Liberation Army PLA is currently unknown, an operating location within Fuzhou is consistent with the group’s persistent focus on Taiwan,” reads the report.
The Insikt Group researchers referred to previous observations showing that Chinese intelligence operations based in Fuzhou fall within the PLA Eastern Theater Command, which heavily focuses on targeting Taiwan.
Based on this location and the group’s activity, Insikt Group assessed that RedJuliett is likely sponsored by the Chinese government.
“RedJuliett's activities align with Beijing's objectives to gather intelligence on Taiwan’s economic policy, trade, and diplomatic relations. The group also targeted multiple critical technology companies, highlighting the strategic importance of this sector for Chinese state-sponsored threat actors,” said the report.
Finally, Insikt threat intelligence researchers anticipate RedJuliett’s continued exploitation of vulnerable public-facing devices. This prediction is based on the group's past success with TTPs targeting these weaknesses.
