A backdoor in Executable and Linkable Format (ELF) files used by Chinese hackers has wrongly been identified as a variant of existing malware for years, Trend Micro claimed in a new report.
In Noodle RAT: Reviewing the New Backdoor Used by Chinese-Speaking Groups, a blog post based on a Botconf 2024 presentation, Trend Micro Research introduced Noodle RAT, a remote access Trojan used by Chinese-speaking groups engaged in either espionage or cybercrime.
A Longstanding Yet Misclassified Backdoor
Also known as ANGRYREBEL or Nood RAT, Noodle RAT has been active since at least 2018. However, it was always considered a variant of an existing malware strain like Gh0st RAT or Rekoobe.
“For instance, NCC Group released a report on a variant of Gh0st RAT used by Iron Tiger in 2018. Talos released a report on an ELF backdoor used by Rocke (aka Iron Cybercrime Group) in 2018. Sophos released a report on a Linux version of the Gh0st RAT variant used in the Cloud Snooper Campaign in 2018. Positive Technology Security released a report on Calypso RAT used by Calypso APT in 2019,” said Trend Micro.
Upon analysis, the cybersecurity provider’s threat intelligence team discovered that the ELF backdoor mentioned in these reports was actually a new malware strain that they named Noodle RAT.
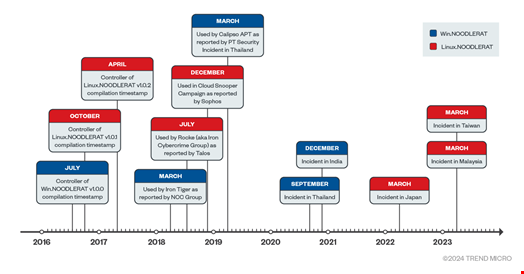
The researchers also claimed they found espionage campaigns using Noodle RAT targeting Thailand, India, Japan, Malaysia, and Taiwan since 2020.
Why Noodle RAT is a New Malware Strain
Noodle RAT is a relatively simple backdoor deployed in two versions: a Windows one called Win.NOODLERAT and a Linux one called Linux.NOODLERAT.
The Windows version of Noodle RAT has several links to Gh0st RAT, a malware strain initially developed by the C. Rufus Security Team in China, whose code leaked in 2008.
For instance, Win.NOODLERAT and Gh0st RAT use the same plugins, and the former implements a slightly similar packet encryption algorithm used by some variants of Gh0st RAT, such as Gh0stCringe, HiddenGh0st, and Gh0stTimes.
However, the rest of Win.NOODLERAT and Gh0st RAT's code does not appear similar, leading Trend Micro to conclude that the plugins were simply reused, but the backdoor itself is totally different.
Additionally, some of Linux.NOODLERAT’s code is the same as Rekoobe v2018, a backdoor based on Tiny SHell (aka tsh), whose source code is publicly available on GitHub.
Specifically, both include the same reverse shell and process name spoofing techniques.
“Still, since the rest of the code of Linux.NOODLERAT is totally different from any version of Rekoobe or Tiny SHell, we can conclude that Linux.NOODLERAT should be classified as another malware family,” Trend Micro said.
Current Use of Noodle RAT “Highly Probable”
In its blog post, the threat intelligence team provided a technical analysis of both Noodle RAT versions, Win.NOODLERAT and Linux.NOODLERAT, including how to initialize them, how they communicate with their command and control (C2) servers, how to control the backdoor once installed, and a description of the C2 server features.
“We have confirmed that some samples of Noodle RAT were uploaded in Virus Total in 2024, which means that it is highly probable that the malware is still in use.
Considering the increase of exploitation against public-facing applications in recent years, malware targeting Linux/Unix systems is becoming more essential for attackers. It might suggest that Noodle RAT could continue to be an attractive option for threat actors for attacks,” the researchers concluded.
