Organizations who pay a ransom to cyber-criminals following a cyber-attack are highly likely to suffer a subsequent attack. It is against this backdrop that one leading CISO has developed a new method to help business leaders decide whether to pay.
During the Gartner Security & Risk Management Summit, Lorraine Dryland, CISO at First Sentier Investors presented her quantitative decision-aid. The model has been developed by Dryland and her colleagues to enable executives to make informed choices during time-critical ransomware incident scenarios.
She said that CISOs simply telling executives they should not pay a ransom will not work. “To force an executive down that path can only end up in negative results and bad experiences because these are very wilful individuals – they don’t get to where they are because they shy away from things, they will want to make a decision,” Dryland explained.
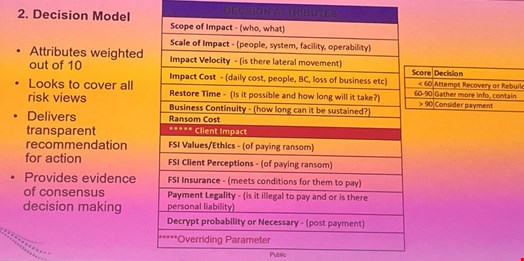
She emphasized that decision-aids must incorporate the business implications of ransomware attacks as well as technical impacts. The technical considerations include restore time and scale of impact without paying.
The business aspects in Dryland’s model include how paying a ransom will impact clients and how it ties in with the firm’s ethics and potential legal liabilities – both personal and company.
Working with the First Sentier risk scoring team, Dryland developed a scoring mechanism on such areas that allows executives to calculate the risks involved in whichever choice they make.
She added that the model has been agreed by the First Sentier executives and will be formally tested in an exercise in the next few months.
Dusty Miller, executive partner - security and risk management at Gartner, welcomed Dryland’s approach, noting that “to pay or not to pay is not a cybersecurity decision, it’s a business decision.”
He emphasized that paying a ransom should be a last resort, highlighting Gartner figures that showed 80% of payers suffered a subsequent attack.
“There’s no guarantee on data recovery, or that the encryption key will work,” added Miller.
What CISOs Should Consider When Developing Decision Aids
Speaking to Infosecurity, Dryland acknowledged that all businesses are unique, and therefore the risk scoring mechanisms will vary in different organizations.
“An extinction level event for one is not extinction level for another, so there’s definitely a uniqueness there for people to understand,” she outlined.
Dryland strongly advocated the ‘ALANP’ (Aim, Legality, Alternative, Necessity & Proportionality) legal framework as the basis for developing a decision-aid like this, ensuring it to stands up to scrutiny.
She also set out several principles that CISOs should follow if they decide to develop their own decision aids for executives in areas such as whether to pay or not to pay a ransomware demand:
- Simplicity is key: Dryland explained that earlier iterations of her decision aid model were too detailed and complicated. Instead, security leaders should be as clear and concise as possible in the options provided.
- Understand the business: Dryland said it is vital CISOs have a strong understanding of the businesses’ goals and turn them into risk factors. She noted that executives’ main priorities will be areas like loss of market share and loss of reputation, and these must be emphasized in a decision aid model.
- Honesty and transparency: She said it is vital that executives are presented with the full facts of any situation, even when mistakes have been made by the security leader.
- Build relationships: Dryland outlined the importance of CISOs building close relationships with business leaders in the organization to be able to develop criteria’s these types of protocols during cyber incidents; if possible, getting to know them on a personal level and “humanizing them.”
