Threat actors are ramping up the use of ‘ClickFix’ social engineering attacks, with this tactic likely proving highly effective for malware deployment.
A new analysis by Proofpoint highlighted numerous campaigns by multiple different threat actors utilizing this tactic since March 2024.
This included a suspected Russian espionage group using this technique to target Ukrainian organizations.
Various malware have been deployed using ClickFix, including AsyncRAT, Danabot, DarkGate, Lumma Stealer and NetSupport.
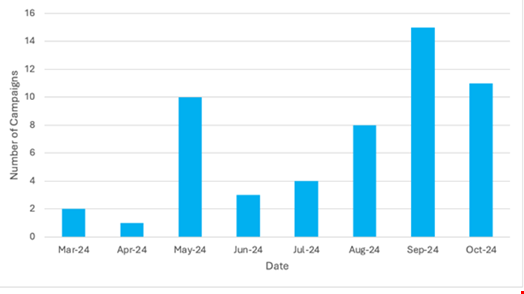
“The ClickFix technique is growing in popularity and is being used by many financially motivated threat actors, as well as reportedly by suspected espionage-focused groups. Given the widespread adoption, it is likely this technique is very effective,” the researchers wrote.
Read now: ClickFix Exploits Users with Fake Errors and Malicious Code
ClickFix Attacks Explained
ClickFix is a unique social engineering technique that uses dialogue boxes containing fake error messages to lure people into copying, pasting and running malicious content on their own computer.
It is effective at bypassing security protections as the user infects themselves.
This tactic preys on users’ desire to fix problems themselves rather than alerting their IT team or anyone else.
The dialogue boxes can originate from a range of sources, including compromised websites, documents, HTML attachments and malicious URLs.
Threat actors have been observed impersonating various software and services using the ClickFix technique, including common enterprise software such as Microsoft Word and Google Chrome.
The dialogue box contains instructions that purport to “fix” the problem, but will either lead to:
- The user automatically copying and pasting a malicious script into the PowerShell terminal or the Windows dialog box to eventually run a malicious script via PowerShell, or
- The user manually opening PowerShell and copying and pasting the provided command
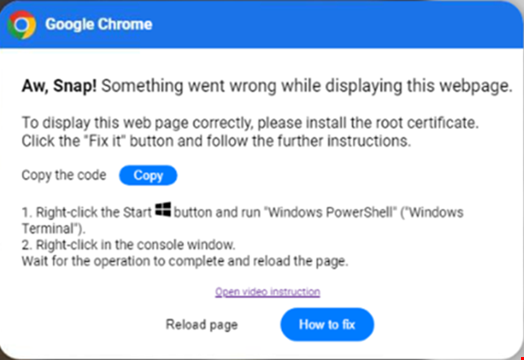
Proofpoint said the growing popularity of ClickFix is a direct result of improved security tooling and user awareness, reducing the success rate of traditional social engineering attacks.
Attackers Leveraging reCAPTCHA Phish Toolkit
The researchers highlighted the frequent use of a fake CAPTCHA themed technique that pretends to validate the user with a "Verify You Are Human" (CAPTCHA) check in recent ClickFix campaigns.
Much of this activity is based on an open source toolkit named reCAPTCHA Phish, which has been available on GitHub since September 2024 for “educational purposes.”
On September 18, Proofpoint identified a campaign which used GitHub notifications to deliver malware.
In this case, the threat actor either commented on or created an issue in a GitHub repository, leading to the repository owner, issue owner or other relevant collaborators receiving an email notification of this content.
The notification impersonated a security warning from GitHub and included a link to a fake GitHub website, which used the reCAPTCHA Phish and ClickFix social engineering technique to trick users into executing a PowerShell command on their computer.
The website landing page contained verification steps that would lead to PowerShell code being executed and the installation of Lumma Stealer.
This page contained a fake reCAPTCHA message at the end of the copied command so the target would not see the actual malicious command in the run-box when the malicious command was pasted.
This activity is believed to have impacted at least 300 organizations globally.
Suspected Russian Espionage Campaign
The researchers also observed a ClickFix campaign using the reCAPTCHA phishing technique being perpetrated by a suspected Russian espionage actor, tracked as UAC-0050, targeting Ukrainian organizations.
The Ukrainian language campaign, identified on October 31, 2024, purported to be emails sharing of documents or requested information with the recipient.
The messages contained suppressed HTML attachments which, if executed, presented a web page with a lure using the reCAPTCHA phish ClickFix technique.
If the user copied and pasted the PowerShell script as instructed, it executed a second PowerShell script which used Bits transfer to download and run a malicious payload, suspected to be Lucky Volunteer. Lucky Volunteer is an information stealing payload that Proofpoint said is “rarely observed.”
Notably, the reCAPTCHA phish ClickFix landing page was in English, despite the email content and attachment names being written in Ukrainian.
