A sophisticated ‘ClickFix’ phishing campaign is impersonating Booking.com to target hospitality firms with multiple infostealing malware, enabling financial fraud and theft.
The ongoing campaign, which began in December 2024, has been attributed by Microsoft Threat Intelligence to a threat cluster known as Storm-1865.
The attackers use a social engineering technique called ClickFix to specifically target individuals in hospitality organizations in North America, Oceania, South and Southeast Asia, and Europe, which are likely to work with Booking.com, an online travel agency.
ClickFix sees threat actors use fake error messages that instruct users to fix issues copying, pasting and launching commands that eventually result in the download of malware.
The technique can bypass conventional and automated security features as the user infects themselves.
The tactic preys on users’ desire to fix problems themselves rather than alerting their IT team or anyone else.
The new campaign deploys multiple families of malware that have capabilities to steal financial data and credentials for fraudulent use. The malware families include XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot and NetSupport RAT.
Some samples have downloaded PowerShell, JavaScript, and portable executable (PE) content.
Microsoft said the tactics bear the hallmarks of past Storm-1865 campaigns, including targeting hotel guests by impersonating Booking.com.
“The addition of ClickFix to this threat actor’s tactics, techniques and procedures (TTPs) shows how Storm-1865 is evolving its attack chains to try to slip through conventional security measures against phishing and malware,” the researchers wrote.
Read now: Booking.com's CSO on Strengthening Security as Cyber-Attacks Target Travel Sector
How the ClickFix Campaign Works
Storm-1865 begins by sending malicious email impersonating Booking.com to the targeted individual.
The content of the emails varies significantly, including references to negative guest reviews, requests from prospective guests, online promotion opportunities account verification.
The emails request the recipients to take action to address the purported issue or query. They contain a link, or a PDF attachment containing one, claiming to take recipients to Booking.com.
Clicking on the link instead takes the victims to a webpage that displays a fake CAPTCHA dialog box. This box is overlayed on a subtly visible background designed to mimic a legitimate Booking.com page, designed to give the targeted user a false sense of security.
Read now: Booking.com Customers Scammed in Novel Social Engineering Campaign
The fake CAPTCHA instructs the user to use a keyboard shortcut to open a Windows Run window, then paste and launch a command that the webpage adds to the clipboard.
If launched, the command downloads and launches malicious code through the mshta.exe file.
This leads to the user being infected with various malware for the purpose of stealing financial data and credentials. The specific code launched through mshta.exe varies for different victims.
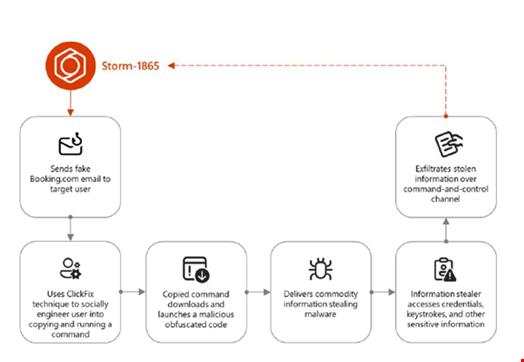
The stolen credentials and other sensitive information, including financial data, are then exfiltrated over a command and control (C2) channel.
This information can be used for follow-on attacks, including fraudulent financial transactions.
Booking.com Confirms Partners and Customers Impacted
In a statement shared with Infosecurity, Booking.com said that while its systems have not been breached from the phishing campaign, some of its accommodation partners and customers have been impacted by phishing attacks with the criminal intent of taking over their local computer systems with malware.
"The actual numbers of accommodations affected by this scam are a small fraction of those on our platform and we continue to make significant investments to limit the impact on our customers and partners. We are also committed to proactively helping our accommodation partners and customers to stay protected. A lot of this is via education, informing our partners of the types of scams we are seeing while arming our customers with practical advice that they can apply as they search for and manage their holiday bookings," the firm wrote.
Booking.com also urged customers to carefully check the payment policy details on their booking confirmation if they receive a payment message purporting to come from the travel booking site.
"It is important to note that we would never ask a customer to share payment information via email, chat messages, text messages or phone," the company added.
This article was updated at 15.50 GMT on March 14, 2025, to incorporate Booking.com's statement
