The MOVEit cyber-attack continues to grow, with more organizations falling victim every day. Brett Callow, a threat analyst at Emsisoft, counted 257 organizations and 17,750,524 individuals impacted by the attack on July 11, 2023.
Meanwhile, the Clop ransomware group, which is reportedly responsible for the attack, keeps adding names to the list of victims on its leak site, with newer ones including big financial companies (Deutsche Bank, ING Bank and Post Bank) and 25 US schools.
David Wallace, a senior threat intelligence analyst at Sophos, took a deep dive into Clop’s background and activity as well as its tactics, techniques and procedures (TTPs) in an article published on July 10.
Clop, Ransomware and Threat Actor
Clop, also spelled Cl0p, translates as ‘bedbug’ in Russian – “an adaptable, persistent pest,” Wallace insisted in his post. It is originally the name of a new variant of the CryptoMix ransomware family first identified in 2019 and tracked by MITRE as s S0611.
The threat group behind Clop is a financially-motivated organization believed to currently operate from Russian-speaking countries, “though it was known to operate in both Russia and Ukraine prior to 2022,” Wallace said.
The Clop ransomware gang has ties with various threat groups, including TA505 and FIN11. Wallace noted that a recent advisory from the FBI and the US Cybersecurity and Infrastructure Security Agency (CISA) stated that Clop and TA505 refer to the same group, but others suggest the three simply overlap or that FIN11 is a subset of TA505.
Clop has recently collaborated with other groups like DarkSide and FIN7, using its ransomware as a service (RaaS) toolkit for point-of-sale attacks or plain old-fashioned exploitation.
Clop Prefers High-Profile Victims
Clop’s preferred targets are larger companies (over $5m annual revenue) located in North and Latin America, Europe and Asia-Pacific – although some of its recent supply chain attacks have impacted smaller organizations in other markets, too. The group typically attacks its victims during holidays.
When first observed, the group relied mainly on phishing attempts, brute forcing and exploiting known vulnerabilities.
They were among the first threat groups to use a ‘double extortion’ strategy, in which an adversary threatens to publish critical data on a leak site – the ‘CL0P^_- LEAKS’ site, which is accessible via Tor hidden service – if the victim refuses to pay. This was initially used as an additional way of exerting pressure on the victims, along with decrypting the data previously encrypted, but Clop and other threat actors seem to have recently been moving away from decrypting data altogether.
According to Wallace, the group is also known for its innovative techniques: “It was, for instance, among the first to use the tactic of emailing customers and partners of a compromised site to demand that they, too, pressure the compromised target to pay – and aggressive, preferential targeting of large organizations. It’s part of infosec history as the source of the first known ransomware demand of over $20m, against Software AG in October 2020.”
Clop’s involvement in the exploitation of a critical zero-day vulnerability (CVE-2023-34362) in Progress Software’s MOVEit Transfer is the third such effort ascribed to Clop during the first half of 2023, after the GoAnywhere incident in February and the PaperCut incident in April.
“Some of those efforts appear opportunistic, either resulting from a sale of the group’s own ransomware tooling or from collaboration with other groups. Others, such as MOVEit itself, appear to be the culmination of a long-term tech effort and refinement process by the group. […] Of note is the group’s consistent and aggressive recent targeting of file-transfer services, which tend to handle data from a variety of systems and thus could be considered a vulnerable point in many supply chains.” reads Wallace’s blog post.
Clop is regularly connected to high-profile attacks such as the 2021 Accellion File Transfer Appliance (FTA) as well as GoAnywhere and the multi-vulnerability MOVEit, which impacted large companies like the BBC, British Airways, Sony, Siemens Energy, EY, PwC, along with the ones previously mentioned.
In the case of the MOVEit attack, Clop wants to directly engage with its victims to negotiate the ransom, although “as recently as July 3, Sophos is not aware of any victims actually paying the ransom,” Wallace added.
Many government agencies worldwide were also impacted by the MOVEit attack. However, in mid-June, Clop issued a statement telling entities affected by the attack, "If you are a government, city or police service do not worry, we erased all your data. You do not need to contact us. We have no interest to expose such information.”
The US government offers a bounty of up to $10m for information on the threat group.
Advisory from @CISAgov, @FBI: https://t.co/jenKUZRZwt
— Rewards for Justice (@RFJ_USA) June 16, 2023
Do you have info linking CL0P Ransomware Gang or any other malicious cyber actors targeting U.S. critical infrastructure to a foreign government?
Send us a tip. You could be eligible for a reward.#StopRansomware pic.twitter.com/fAAeBXgcWA
Deep Dive into Clop’s TTps
Like the pest after which it was named, Clop is “a loud, adaptable, persistent player,” Wallace said.
It employs several tactics during an attack to maximize impact and increase the likelihood of victims paying the ransom, which can change from case to case.
Here are the five typical steps of an attack deployed by the ransomware gang:
- Initial access: Clop usually targets its victims with social engineering techniques and gains initial access to their network through phishing emails, exploit kits, or exploitation of vulnerabilities in software and systems. “One Sophos MDR client’s logs recorded 3689 Clop-driven attempts against their Ubiquity UniFi server to gain initial access,” Wallace noted.
- Persistence: Clop maintains access to compromised systems in multiple ways. “In a case recently handled by the Sophos X-Ops Incident Response team, the threat actor chose to leverage Cobalt Strike Beacon to establish their persistence on the first compromised machine,” Wallace said.
- Lateral movement: Once access to the network has been achieved, Clop pivots laterally, searching for and infecting connected systems. This lateral movement allows the ransomware to deploy quickly throughout the network: infecting the infrastructure, encrypting many files and maximizing the operation’s impact. “In incidents Sophos observed, the threat actor initially leveraged server message block (SMB) connections before transitioning to interactive remote desktop protocol (RDP) sessions,” reads the blog post.
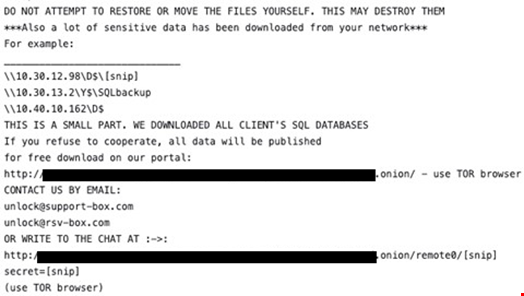
- Exfiltration: Clop often exfiltrates data that it considers valuable from compromised networks before deploying the ransomware – including employee human resources data, intellectual property, financial data and customer information. This gives the group the leverage it needs to strengthen the extortion portion of the plot, relying on the threat of leaks to pressure victims into paying hefty ransoms. “One of the tactics Clop and similar groups rely on most frequently for exfiltration is classified by MITRE as Exfiltration Over Web Service (T1567), which covers the use of a variety of third-party tools such as megasync, rclone, Filezilla or Windows Secure Copy. They also look at C2-based avenues of approach such as Remote Access Software (T1219) and Ingress Tool Transfer (T1105),” Wallace outlined. Meanwhile, the group leaves its mark all across the network, changing the extensions of the encrypted files to [.]Clop (or [.]CIIp or [.]C_L_O_P or similar).
- Victim notification: As is typical with ransomware operators, after encrypting (and possibly exfiltrating) the files, Clop leaves a README.TXT ransom note on the compromised systems. This is (usually) where the price to decrypt the files is made known to the target – a distinctive choice, since ransomware gangs often prefer to disclose the price to victims once a private chat is established — as well as the instructions for how to provide the payment demanded. Clop usually – but not always – provides a deadline for initial contact.
In rare cases, Clop has also been observed to engage in hacktivism campaigns, conducting distributed denial of service (DDoS) attacks.
“The benefit to Clop of participating in such campaigns (money, loyalty, or something else) is unknown, as is the actual impetus for the attack – hacktivism or merely ransomware with extra pressure points,” Wallace said.
