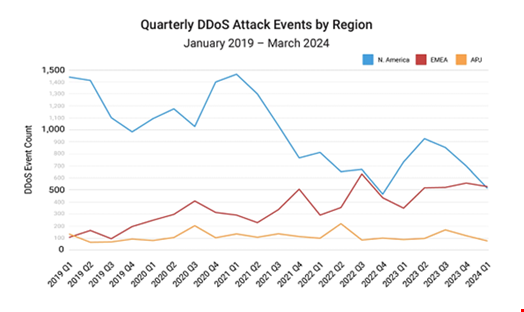
DDoS attacks have risen sharply in Europe, the Middle East and Africa (EMEA), surpassing North America as the most targeted region in Q1 2024, according to a new Akamai report launched at Infosecurity Europe 2024.
EMEA is the only region of the world where DDoS attacks have consistently risen since 2019. This has partly been driven by the ongoing Russia-Ukraine war and more recently the Israel-Hamas conflict, the researchers noted.
In contrast, in North America the DDoS attack volume has significantly fallen since 2023.
The total number of EMEA DDoS attack events reached almost 2500 throughout 2023, which is more than three-times as high as those experienced in the Asia Pacific and Japan (APJ) and Latin America (LATAM) combined.
UK the Biggest Target for DDoS Attackers
The researchers observed that the UK has faced over a quarter (26%) of all DDoS attacks targeting the EMEA region since 2019.
The next most targeted nation states are Saudi Arabia (22%) and Germany (9%).
The analysis also found that over half (53%) of all DDoS attacks in the financial services sector are aimed at targets based in EMEA. North America is the second most targeted region in the financial services vertical, at 43%.
The most prevalent DDoS attack type used by threat actors are those targeting the Domain Name System (DNS), likely due to the enormous impact flooding these systems can have on victims.
More than one-third of DDoS events use multiple attack vectors, sometimes as many as 12, to increase success rates. The most popular of these vectors are DNS flood, UDP fragment and NTP reflection.
Akamai noted that the emergence of services such as DDoS boosters, which can cost as little as £8.50 ($10.83), is further lowering the barrier to entry for attackers.
Global Conflicts Contribute to the DDoS Surge
The report also highlighted how the ongoing Russia-Ukraine and Israel-Hamas wars are contributing to the DDoS surge in EMEA.
Both conflicts have led to a wave of politically motivated hacktivists and nation-state sponsored actors on all sides conducting cyber-attacks. DDoS has been a particularly popular tactic due to its low cost and complexity.
Pro-Russian actors repeatedly took Ukrainian government and critical infrastructure websites offline through DDoS attacks in the build up to the Kremlin’s invasion of the region in February 2022. Such actors have also targeted Ukraine’s allies with this tactic, such as the websites of the European Parliament and British Royal Family.
Pro-Ukrainian hacktivists have been frequently observed targeting websites of Russian governments and institutions since the war began.
While cyber-attacks appear to have played a far less significant role in the Israel-Hamas conflict, various hacktivist groups have claimed to have launched DDoS attacks on Israeli targets in the wake of Hamas’ shock attack on Israel on October 7, 2023.
In February 2024, several top UK universities were disrupted by DDoS attacks, with the Anonymous Sudan hacktivist group claiming responsibility, citing the UK Government’s support for Israel’s military action in Gaza.
Richard Meeus, Director of Security Technology and Strategy, EMEA, Akamai, said that he expects EMEA targeted DDoS incidents to continue to rise over the coming months with a number of high-profile events set to take place.
“As the region approaches several high-profile events such as the UK and EU elections, and the summer of sports, cybercriminals will continue to turn up the heat. It is critical that organizations protect their digital assets and shield their DNS infrastructure to avoid being burnt,” he commented.
