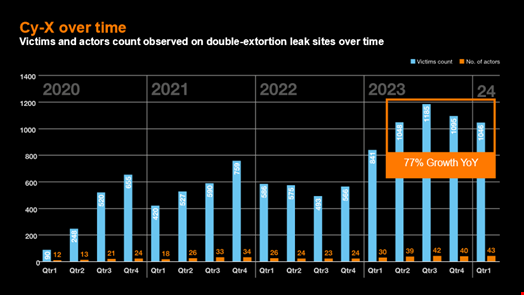
Cyber extortion continues to proliferate with an unprecedented number of threat actors and a 77% year-on-year growth in cyber extortion victims, according to Orange Cyberdefense (OCD).
In its Cy-Xplorer 2024 report, published on July 3 , OCD observed that 60 distinct ransomware groups were responsible for 4374 victims over the period of Q2 2023 to Q1 2024.
Companies employing less than 1000 people, classed as small and medium businesses (SMBs), suffered cyber extortion attacks 4.2 times more often than larger enterprises.
Diana Selck-Paulsson, the lead security researcher at OCD, said that the large number of SMBs in the overall number of cyber extortion victims could be explained by the fact that threat actors have turned away from ultra-targeted attacks – also called ‘big game hunting.’
“What we see, and what our victimology data confirmed, is that nowadays, threat actors compromise a network and only then scan for targets they could extort,” she explained during the report’s launch event in Antwerp, Belgium, on July 2.
Generally, the report data shows that threat actors employ opportunistic approaches, primarily targeting organizations with lower cyber preparedness levels in English-speaking, wealthy countries like the US, the UK and Canada.
However, overall, the OCD report shows that the cyber extortion problem is universal, with 75% of all countries in the world having had businesses directly impacted since 2020.
Healthcare Sees 160% increase in Cyber Extortion
Over the past 12 months, all 20 industries classified by the North American Industry Classification System (NAICS) have been victims of cyber extortion.
As in last year’s report, manufacturing is the most targeted sector, followed by organizations in professional, scientific, and technical services.
The healthcare and social assistance sector, which suffered a 160% increase in cyber extortion attacks between 2023 and 2024, joins the top three most impacted industries for the first time since OCD started tracking cyber extortion in 2020.
These findings come during a challenging period for the healthcare industry, which suffered several major cyber-attacks over the past few months.
Incidents include the series of extortion campaigns against Change Healthcare, a subsidiary of UnitedHealth Group, and a breach in pathology provider Synnovis’ IT systems that led to sensitive patient information in the UK being leaked.
Law Enforcement Shares Real Ransomware Victim Counts
The actual number of cyber extortion victims is likely more significant than the observed number of victims shown in Cy-Xplorer and other ransomware threat intelligence reports, explained Simen Van der Perre, a strategic advisor at OCD, at the event in Antwerp.
“Our analysis comes primarily from victims reported on ransomware groups’ data leak sites, with additional dark web research and interviews. Usually, victims appear on these data leak sites because they haven’t paid the ransom,” he said.
This means that threat intelligence researchers cannot count victims who have paid the ransom before being posted on data leak sites – a phenomenon Van der Perre called the ‘dark number.’
“Thankfully, the increased law enforcement operation activity over the past few months provided us with insightful extra information,” he added.
Following the takedowns of ransomware groups ALPHV/BlackCat and LockBit, law enforcement shared the actual number of those groups’ victims. They were respectively 1.61 and 1.52 times higher than the number of victims previously observed by OCD.
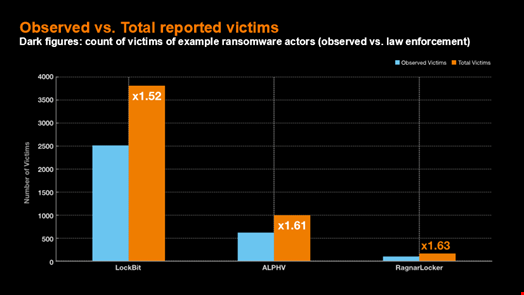
“With this data, we found that the overall number of cyber extortion victims in 2023 and 2024 is 50% to 60% bigger than what we observed,” Van der Perre said.
Revictimization, Ransomware Groups’ New Tactic
Finally, OCD observed a new trend of “revictimization.”
This phenomenon happens when a ransomware victim is targeted twice or more in different compromise campaigns, either by the same group or by other threat actors.
OCD observed over 200 occurrences of revictimization, with the majority happening in 2023.
Victims were posted up to three times on ransomware groups’ data leak sites, sometimes with a long delay between each occurrence, of up to 1301 days.
“We analyzed the relationships between first, second and third posters and concluded that revictimization could result from three possible scenarios: ransomware affiliate crossovers, ransomware groups sharing data and potential new compromises,” Selck-Paulsson explained.
