Swift detection of a malicious insider that used stolen credentials to gain unauthorized access to Australia’s Early Warning Network (EWN) allowed EWN staff to shut down systems and limit the number of messages the hacker was able to disperse, according to a 7 January 2019 update on the company’s website.
The anomalous activity of the hacker who had illegally accessed the EWN alert system was detected around 9:30 EDT on 5 January 2019. While news of companies being hacked becomes more commonplace, the ability to swiftly detect and respond to malicious insiders continues to be critical to an organization’s overall security strategy.
After gaining access to the alert system – which is designed to alert users to weather emergencies – the attacker was able to send what the company describes as “nuisance” messages by way of email, text messages and phone calls to landlines, then to part of EWN’s database.
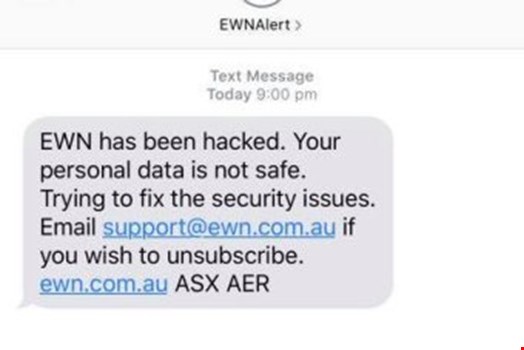
Included in the message was a link to opt out of future messages, and those who received the fraudulent alert are advised to not click on the links and delete the message.
“EWN staff at the time were able to quickly identify the attack and shut off the system limiting the number of messages sent out. Unfortunately, a small proportion of our database received this alert. Our systems are back up and running providing ongoing alerts for severe weather and natural hazard events. Investigations are continuing with police involvement,” the website said.
“The unauthorized alert sent on Saturday night was undertaken by an unauthorized person using illicitly gained credentials to log in and post a nuisance spam-notification to some of our customers. The links used in this alert were non-harmful and your personal information was not compromised in this event. Investigations are continuing with the police and Australian Cyber Security Centre involved.”
Infosecurity Magazine contacted EWN, but the company has not responded. According to the Australian Broadcasting Corporation (ABC), EWN's managing director, Kerry Plowright, said the breach was the result of compromised login details believed to have come from within Australia. No personal data has been compromised, as the system reportedly holds only "white pages" and no personal information.
