Ebury, one of the most advanced server-side malware campaigns, has been active for 15 years but its use by threat actors is still growing, according to cybersecurity firm ESET.
A new report published on May 14 by ESET Research showed that operators of the Ebury malware and botnet were more active than ever in 2023.
Over the years, Ebury has been deployed as a backdoor to compromise almost 400,000 Linux, FreeBSD and OpenBSD servers. More than 100,000 were still compromised as of late 2023.
Long known to deploy spam, web traffic redirections and credential stealing, the Ebury group recently added credit card compromise and cryptocurrency theft in its techniques, tactics and procedures (TTPs).
What is the Ebury Botnet?
Ebury is a malicious group that has been active since at least 2009. It has developed an OpenSSH backdoor and a credential stealer used to deploy multiple malware strains simultaneously by relying on a bot network (botnet).
The group’s primary targets are hosting providers.
The Ebury botnet is used to compromise Linux, FreeBSD and OpenBSD servers in order to deploy web traffic redirection modules, proxy traffic for spam or perform adversary-in-the-middle attacks (AitM).
In 2014, ESET published a white paper about Operation Windigo, a malicious campaign using multiple malware families working in combination with the Ebury malware family at its core.
Following the release of the Windigo paper, Russian national Maxim Senakh, one of the Ebury operators, was arrested at the Finland-Russia border in 2015, and later extradited to the US.
In 2017, he was sentenced to 46 months in prison in the US for his role in running the Ebury botnet. ESET assisted the FBI in the operation and testified during the trial.
In late 2021, the Dutch National High Tech Crime Unit (NHTCU), part of the Netherlands national police, contacted ESET after they had found Ebury on the server of a victim of cryptocurrency theft.
“Those suspicions turned out to be well-founded and with NHTCU's assistance, ESET Research has gained considerable visibility into operations run by the Ebury threat actors,” the new ESET report indicated.
Marc-Etienne M. Léveillé, the ESET researcher who investigated Ebury for more than a decade, commented: “We have documented cases […] where the Ebury actors were able to compromise thousands of servers at once. There is no geographical boundary to Ebury; there are servers compromised with Ebury in almost all countries in the world. Whenever a hosting provider was compromised, it led to a vast number of compromised servers in the same data centers.
“At the same time, no verticals appear more targeted than others. Victims include universities, small and large enterprises, internet service providers, cryptocurrency traders, Tor exit nodes, shared hosting providers and dedicated server providers, to name a few.”
Ebury’s New Favorite Targets: Bitcoin and Ethereum Nodes
Despite the arrest, the Ebury group has continued running malicious campaigns, at least until late 2023.
The ESET report describes new methods used to propagate Ebury to new servers that appeared after 2021.
From its access to its target’s infrastructure, usually a hosting provider, the Ebury group can deploy several types of attacks.
In one of the most recent ones, the group uses an AitM attack to intercept SSH traffic of attractive targets inside data centers and redirect it to a server used to capture credentials.
The malicious actors leverage existing Ebury-compromised servers in the same network segment as their target to perform Address Resolution Protocol (ARP) spoofing. Among the targets are Bitcoin and Ethereum nodes. Ebury automatically steals cryptocurrency wallets hosted on the targeted server once the victim types the password to log into it.
ESET has observed that this method was used to target over 200 targets across over 75 networks in 34 countries between February 2022 and May 2023.
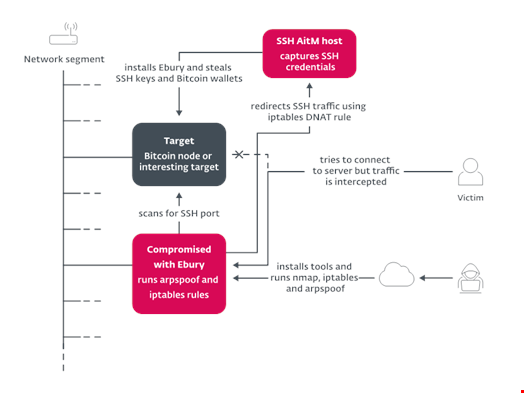
This example not only illustrates one of Ebury’s latest attack techniques, but also one of the group’s newest vectors of monetization: cryptocurrency theft.
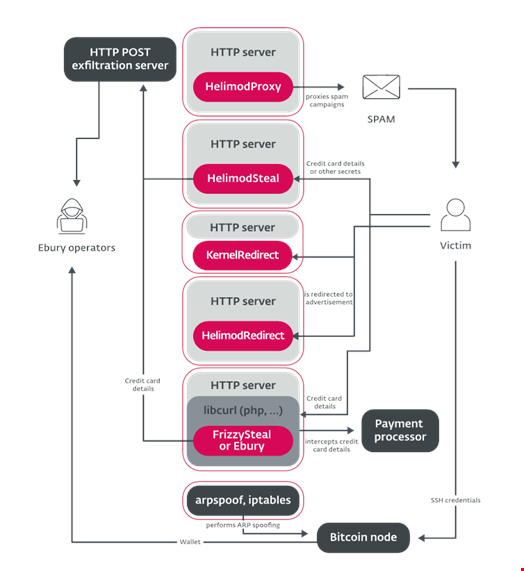
Additionally, the Ebury malware family itself has also been updated.
The new major version update, 1.8, first seen in late 2023, included new obfuscation techniques, a new domain generation algorithm (DGA) and improvements in the userland rootkit used by Ebury to hide itself from system administrators. When active, the process, the file, the socket and even the mapped memory are hidden.
2023, a Record-Breaking Year for Ebury
These shifts in the Ebury group’s infection and monetization methods seem to be bearing fruit, as the group’s activity significantly increased in 2023 compared to 2021.
“The perpetrators keep track of the systems they compromised, and we used that data to draw a timeline of the number of new servers added to the botnet each month,” the ESET researchers wrote.
August 2023 saw record-breaking activity from the group, with over 6000 compromised servers recorded that month.
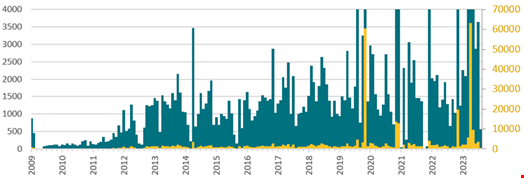
Combined, about 400,000 servers have been compromised by Ebury since 2009, and more than 100,000 were still compromised as of late 2023.
