The UK National Crime Agency (NCA) has sanctioned 16 members of Russian hacker group Evil Corp and has identified its links to prolific ransomware group, LockBit.
The sanctions were announced on October 1, 2024. Australia and the US have also imposed sanctions.
This latest update is the result of phase three of Operation Cronos, a global law enforcement operation which first that took down much of LockBit’s infrastructure in February.
Evil Corps in the Crosshairs of Law Enforcement
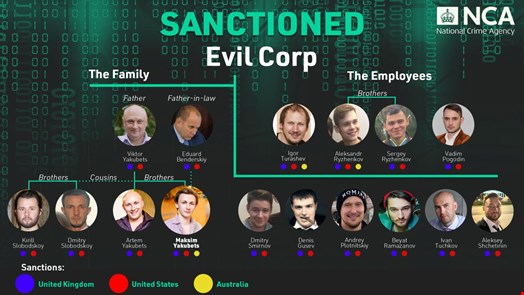
This latest round of sanctions is in addition various Russian nationals from the group having been indicted or charged by the US Department of Justice (DoJ) in 2019, including the head of Evil Corp, Maksim Yakubets, and one of the group’s administrators, Igor Turashev.
In the October 1, 2024 announcement, Yakubets, Turashev, and seven of those sanctioned by the US in 2019 have also been designated in the UK by the Foreign, Commonwealth and Development Office, along with an additional seven individuals, whose links and support for the group have not previously been exposed.
The NCA has been investigating Evil Corp for a number of years and said that the crime group has extorted at least $300m from global victims including those within healthcare, critical national infrastructure, and government, among other sectors.
Evil Corp is a well-known financially motivated Russian cybercriminal group which was formed in 2014 and was responsible for the development and distribution of BitPaymer and Dridex, which it used target banks and financial institutions in over 40 countries, stealing over $100m.
Some of the group’s members had close links to the Russian state.
Commenting on the latest sanctions, UK Foreign Secretary David Lammy said: “I am making it my personal mission to target the Kremlin with the full arsenal of sanctions at our disposal."
“Putin has built a corrupt mafia state with himself at its center. We must combat this at every turn, and today’s action is just the beginning.”
He added that the sanctions send a clear message to the Kremlin that we will not tolerate Russian cyber-attacks - whether from the state itself or from its cyber-criminal ecosystem.
Evil Corp’s Links to LockBit
The right-hand man of Yakubets, Aleksandr Ryzhenkov, is among those sanctioned and has been identified as a LockBit affiliate as part of Operation Cronos - the ongoing NCA-led international disruption of the group.
The NCA said that the 2019 sanctions of Evil Corps members caused considerable disruption to Evil Corp, damaging their brand and ability to operate, including making it harder for them to elicit ransom payments from victims.
They were forced to rebuild and change tactics, and some member moved away from using their own technical tools, like WastedLocker, Hades, PhoenixLocker, PayloadBIN and Macaw, to using other ransomware strains such as LockBit.
The leader of LockBit, or admin known as LockBitSupp, was identified as Russian national Dmitry Yuryevich Khoroshev in May 2024.
Despite the law enforcement operation, which took place in February, the LockBit ransomware has still been used in attacks and LockBit 3.0 returned to the fold in May.
According to an analysis by NCC Group, 176 ransomware attacks were launched in May alone using LockBit 3.0.
Four More Suspected LockBit Members Arrested
Alongside the Evil Corp sanctions, Europol has revealed that four suspected LockBit actors have been arrested by law enforcement, while servers critical for the group’s infrastructure have been seized.
A suspected developer of LockBit was arrested at the request of French authorities, while the British authorities arrested two individuals for supporting the activity of a LockBit affiliate.
In addition, Spanish police arrested an administrator of a Bulletproof hosting service used by the ransomware group, and seized nine servers used by the group.
This article was updated at 17.00 BST
