An Iranian state-backed threat actor is targeting individuals associated with the Harris and Trump Presidential campaigns, according to Google’s Threat Analysis Group (TAG).
The group, APT42, has been observed attempting to compromise email accounts of individuals associated with the respective US Presidential campaigns via spearphishing attacks.
TAG said APT42 targeted the personal email accounts of roughly a dozen affiliated with President Biden and with former President Trump, including current and former officials in the US government, in May and June.
These campaigns have led to multiple accounts being successfully breached, including the personal Gmail account of a high-profile political consultant.
“Today, TAG continues to observe unsuccessful attempts from APT42 to compromise the personal accounts of individuals affiliated with President Biden, Vice President Harris and former President Trump, including current and former government officials and individuals associated with the campaigns,” said the researchers.
The new analysis follows a Microsoft report on August 8 that detailed four distinct cyber-enabled influence operations by Iranian actors targeting the US Presidential Election cycle.
APT42 is known to targets military and political figures in support of Iran’s geopolitical goals.
Intensified Targeting of Israel
The Google TAG researchers also revealed an intensified targeting of users based in Israel since April 2024 by APT42. These phishing attacks have primarily targeted individuals with connections to the Israeli military and defense sector, as well as diplomats, academics and NGOs.
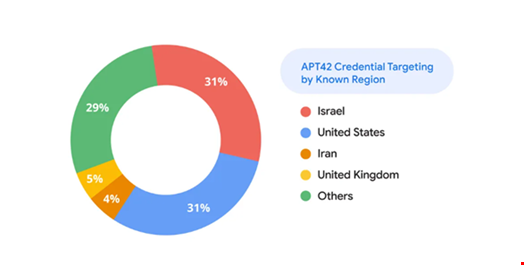
In the six months from February to July 2024, TAG found that the US and Israel has accounted for approximately 60% of APT’s known geographic targeting.
“These activities demonstrate the group’s aggressive, multi-pronged effort to quickly alter its operational focus in support of Iran’s political and military priorities,” the researchers wrote.
APT42’s Tailored Phishing Attacks
APT42’s spearphishing operations are sophisticated and use a variety of tactics, including hosting malware, phishing pages and malicious redirects.
“APT42 is a sophisticated, persistent threat actor and they show no signs of stopping their attempts to target users and deploy novel tactics,” warned the TAG researchers.
The group regularly creates accounts or domains that impersonate organizations that might be of interest to the targets, such as political think tanks.
It will also register typosquat domains very close to the legitimate domains of the organizations they impersonate to appear more legitimate.
Once a target is identified, APT42 often sends phishing links directly in the body of the email or as a link in an otherwise benign PDF attachment. In these cases, it engages their target with a social engineering lure to set-up a video meeting and then link to a landing page where the target was prompted to login and sent to a phishing page.
Another common APT42 approach is sending legitimate PDF attachments as part of a social engineering lure to build trust and encourage the target to engage on other platforms like Signal, Telegram or WhatsApp.
The attackers then use these platforms to send a phishing kit to harvest credentials. These phishing kits target a variety of sign-on pages including:
- GCollection/LCollection/YCollection: A tool capable of gathering credentials from Google, Hotmail and Yahoo users
- DWP: A browser-in-the-browser phishing kit often delivered via URL shortener
APT42 has developed a strong understanding of the email providers they target, often researching the security settings of accounts being targeted using failed login or recovery workflows to determine the configured second factor for authentication to better target their initial phishing attempts.
Additionally, APT42 undertakes significant reconnaissance on targets, using open-source marketing and social media research tools to identify personal email addresses that might not have default multi-factor authentication (MFA) or other protection measures in place.
