In 2022, Russia-backed cyber-attacks targeting Ukraine rose 250% compared to 2020 and those targeting NATO countries, 300%.
This staggering surge is one of the findings from Google Threat Analysis Group (TAG) in a February 16 report, Fog of War: How the Ukraine Conflict Transformed the Cyber Threat Landscape, published in collaboration with Google Trust & Safety and threat intelligence firm Mandiant, now part of Google Cloud.
In the report, Google found that Russia’s aggressive, multi-faceted strategy to “gain a decisive wartime advantage in cyberspace” could actually date back to 2019.
Five Phases of Cyber Operations
During the first phase highlighted by Google, which spanned between 2019 and early 2022, Russia ran cyber espionage campaigns against Ukraine and NATO member-states, as well as what the American tech giant calls “pre-positioning” operations.
From April 2021, one month after Russian troops started to mass on the Ukraine border, the Russian Advanced Persistent Threat (APT) group UNC2589 (aka Frozenvista), “a new, probable GRU actor,” started deploying phishing attacks against Ukrainian organizations, the report claims. The GRU is the common acronym given to the Russian Armed Forces’ Main Directorate of the General Staff, a military intelligence agency.
Several other Russian-sponsored followed suit throughout 2021, including Fancy Bear (APT28, aka Frozenlake).
In mid-January 2022, a wave of disruptive and destructive cyber-attacks started, with wiper attacks such as WhisperGate (aka PayWipe) and its affiliate, WhisperKill (aka ShadyLook).
These were a taste of what was to come in the second phase when Russian troops began their kinetic invasion of Ukraine. The land-advance in February was accompanied by many more disruptive and destructive wiper attacks. This phase lasted until April, with the emergence of several new malware families, including the PartyTicket ransomware, the wiper CaddyWiper and Industroyer 2, an updated version of Industroyer, a destructive malware targeting industrial control systems (ICS), which is considered to have been used in the cyber-attack on Ukraine’s power grid in December 2016.
In May, Russian-backed threat actors entered a third phase where they started to reuse the same malware, primarily CaddyWiper, to attack entities in Ukraine and NATO countries.
According to the report, this phase lasted until July, followed by a lull in activity during August and September. Cyber-attacks resumed in October, in a fifth phase that saw Russian threat actors use CaddyWiper along with other new malware.
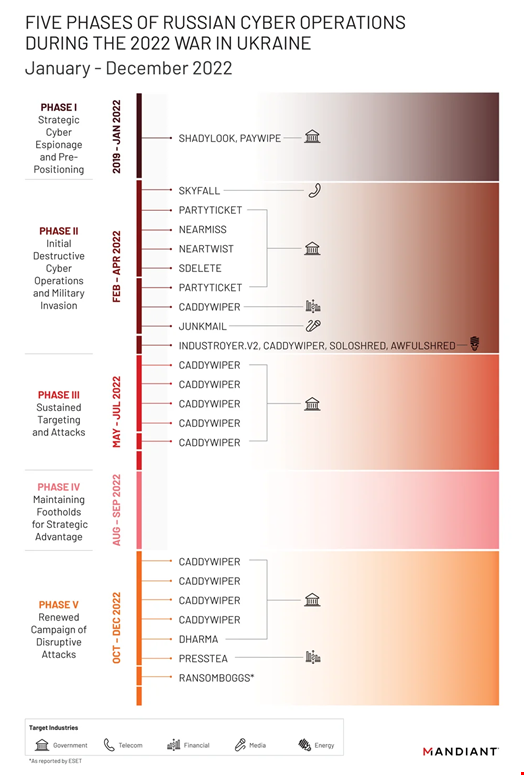
“From its incident response work, Mandiant observed more destructive cyberattacks in Ukraine during the first four months of 2022 than in the previous eight years, with attacks peaking around the start of the invasion. […] Many operations indicated an attempt by the GRU to balance competing priorities of access, collection, and disruption throughout each phase of activity,” the report reads.
A Multi-Faceted Strategy
In summary, Russia’s multi-pronged offensive approach in cyberspace included the following:
- A dramatic increase in the use of destructive attacks on the Ukrainian government, military and civilian infrastructure
- A spike in spear-phishing activity targeting NATO countries
- An uptick in cyber operations designed to further multiple Russian objectives, such as hack-and-leak attacks targeting sensitive information
The report showed that some actors focused on specific types of attacks, such as Frozenlake/Fancy Bear, Frozenvista and Belarusian actor Puschcha (UNC1151) with phishing campaigns against Ukraine and NATO countries, and Coldriver (aka Gossamer Bear) with hack-and-leak campaigns against Ukraine and the UK.
One group, however, Frozenbarents (aka Sandworm, Voodoo Bear), dubbed “the GRU’s most versatile operator” by Google, ran all kinds of cyber-attacks against Ukraine and NATO countries.
“While we see these attackers focus heavily on the Ukrainian government and military entities, the campaigns we disrupted also show a strong focus on critical infrastructure, utilities and public services, and the media and information space,” the report reads.
However, the report also noted that many of these operations led to “mixed results.”
A good example is the Industroyer 2 attempted attack on the Ukrainian energy sector, which seemed to have failed.
Overt and Covert Disinformation Campaigns
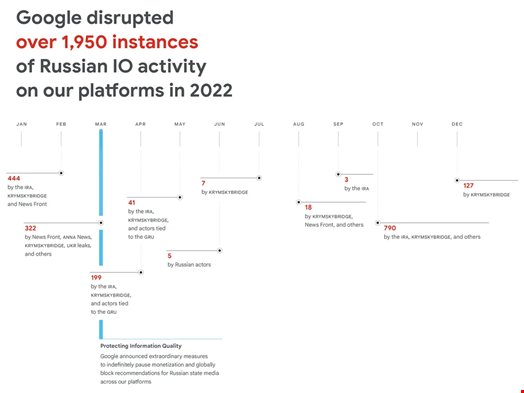
Along with these straightforward cyber-attacks, the report showed that Russia has been running all types of information operations (IO) campaigns, from the most overt state-sponsored disinformation campaigns run by the infamous St-Petersburg-based ‘troll farm,’ the Internet Research Agency (IRA), to more covert campaigns run by affiliates like the Russian consulting firm Krymskybridge or groups linked with Russian intelligence.
Google claimed it “disrupted over 1950 instances of Russian IO activity in 2022,” targeting both Russian and foreign audiences.
The report also showed that “the war has split the loyalties of financially motivated attackers, [which has increased] the overlap between [them] and government-backed threat actors.”
This phenomenon is best represented by the fate of the Conti gang, which counted both Russian and Ukrainian members and exploded after some of its alleged leaders publicly supported the invasion.
“This shift in the Eastern European cyber-criminal ecosystem will likely have long-term implications for coordination between criminal groups and the scale of cybercrime worldwide,” notes the report.
Looking ahead, Google believes “with high confidence that Russian government-backed attackers will continue to conduct cyber-attacks against Ukraine and NATO partners, increase disruptive and destructive attacks in response to developments on the battlefield [and] increasingly expand to include NATO partners.
The researchers also think “with moderate confidence, that Russia will continue to increase the pace and scope of IO, particularly as we approach key moments like international funding, military aid, domestic referendums, and more.
