Originally discovered in the first quarter of this year, Gumblar compromises infected PCs and steals their FTP credentials to compromise PHP-based websites. In October, Gumblar began using the compromised websites to host the malware directly, using server-side polymorphism to thwart signature-based detection.
These websites are being used as malware servers to deliver the malware via thousands of other websites that have been compromised and injected with HTML iFrame tags.
The significance is that whereas traditional drive-by downloads are delivered via a handful of malware servers, Gumblar is now serving malware from at least 2000 actual websites, explained Mary Landesman, senior security researcher at ScanSafe. "As a result, there is no single or few points at which to target efforts to shut down the source of malware", she warned.
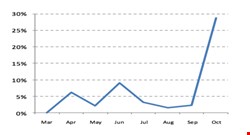
This has led to a drastic increase in the level of Gumblar infections. In September, the percentage of malware blocked by ScanSafe's systems rested at around 2%. It reached 29% in October, according to the ScanSafe Global Threat Report for Q4. This is in spite of errors in the malware that can cause an infected site to display incorrectly.
Ongoing analysis suggests that other groups of attackers are also using the backdoors left behind by Gumblar, ScanSafe said.
Gumblar specifically attacks PHP-based websites with its backdoor, and uses PDF, Flash, and office web components [OWC] to infect clients.