Attackers have been exploring new forms of phishing bait that will entice users to click and have reportedly had success exploiting Bangladesh's Cairo embassy website, according to researchers at Trustwave.
Research conducted at the end of October 2018 revealed that the Coinlmp web miner created a block for a government facility domain. Only two months later, the threat team detected a Microsoft Word document with an embedded malicious EPS script for the same domain. According to today’s blog post, the office document contains an EPS file and exploits a use-after-free vulnerability, CVE-2017-0261.
Detection rates for the malicious page were low,. However, when researchers tried to access most of the webpages on the site, they were prompted to save a file instead, indicating that malicious actors were controlling the embassy's website.
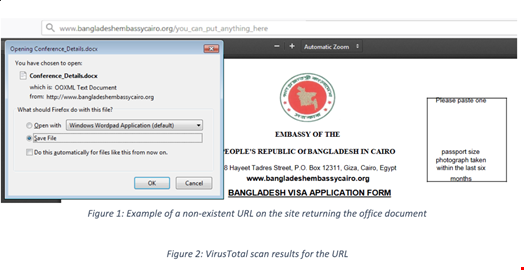
“We contacted the compromised domain in an attempt to alert them of the infection, unfortunately we received no response and at the time of publishing this blog the site remains infected,” researchers wrote.
Through their analysis, researchers noted that the file appeared to have been modified in October 2018, adding, “It’s possible that after running a wider infection campaign infecting sites with a web miner, the attacker looked through their victims to find more interesting targets to leverage further.”
The file then exploits the vulnerability CVE-2017-7255, which enables privilege escalation for the execution of the main payload, the Godzilla loader. Additional executables can be dropped by the attacker after establishing communication with the C2 server. In this case, the researchers identified an additional downloader using a cryptominer payload.
