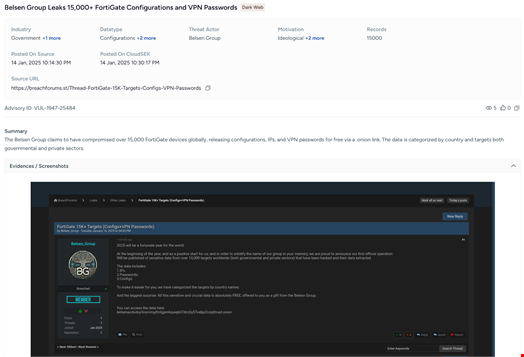
A new threat actor has leaked configuration files and virtual private network (VPN) information for 15,000 firewall devices provided by security vendor Fortinet.
On January 15, Kevin Beaumont, an independent security researcher, revealed on Mastodon that sensitive information from the FortiGate devices had been made available for free on the dark web.
Beaumont said a new hacking group dubbed ‘Belsen Group’ was responsible for the leak.
Security provider CloudSEK confirmed Beaumont’s findings in a new report published on January 16.
The firm said the data dump included FortiGate usernames, passwords (some in plain text), device management digital certificates and firewall rules.
Beaumont and CloudSEK researcher, Koushik Pal, said most exposed devices run Fortigate 7.0.x and 7.2.x versions.
Belsen Group, which first appeared on social media and cybercrime forums in January 2025, has leaked the data on a Tor website.
A CloudSEK spokesperson told Infosecurity that the threat group has likely been around for a couple of years and the exploitation campaign probably occurred in 2022.
“Belsen Group may seem new to the forums, but based on the data leaked by them, we can ascertain with high confidence that they’ve been around for at least three years now. They were likely part of a threat group that exploited a zero-day in 2022, although direct affiliations have not been established yet,” CloudSEK noted in its report.
Beaumont came to the same conclusions in a blog post he published on January 16.
“The data appears to have been assembled in October 2022, as a zero-day vulnerability. For some reason, the data dump of config has been released today, just over two years later,” Beaumont said.
Belsen Group’s Leaked Data Likely Legitimate
Elements in the data dump indicate that at least some of the data leaked by Belsen Group is legitimate, according to Beaumont.
For instance, the researcher said he was able to match up devices’ IP addresses and configurations and observed some exposed devices on the security search engine Shodan.
“I've confirmed one of the usernames and passwords with one of the victims a friend works at. Impacted organizations are going to need to change local SSL VPN passwords, admin passwords etc,” Beaumont added. “It looks like a very serious cyber incident is going to play out.”
A Fortinet Vulnerability Behind the Leak
CloudSEK and Beaumont said the threat group probably exploited a vulnerability disclosed by Fortinet in 2022, CVE-2022-40684.
This flaw is an authentication bypass using an alternate path or channel in Fortinet FortiOS version 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy version 7.2.0 and version 7.0.0 through 7.0.6 and FortiSwitchManager version 7.2.0 and 7.0.0.
When exploited it allows an unauthenticated attacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests.
The US National Vulnerability Database entry for this vulnerability was modified in November 2024 and is awaiting reanalysis by the NVD staff.
New Authentication Bypass Zero-Day in FortiGate
The dark web data leak comes days after Fortinet disclosed a new zero-day vulnerability, CVE-2024-55591.
This zero-day affects FortiGate firewall devices running FortiOS versions 7.0.0 through 7.0.16 and FortiProxy versions 7.0.0 through 7.0.19 and versions 7.2.0 through 7.2.12.
While the new vulnerability is unrelated to the one exploited by the Belsen Group, CloudSEK’s Pal told Infosecurity, the threat actors that exploited the zero-day in 2022 will likely plan on exploiting this vulnerability too, making them imperative to patch.
Pal explained this is because both the CVEs are authentication bypass vulnerabilities of the same kind and can be exploited using an alternate path or channel.
Separately, security provider Arctic Wolf recently revealed a massive exploitation campaign affecting FortiGate firewall devices with management interfaces exposed on the public internet since December 2024.
It is unclear if this campaign is linked to the Belsen Group data dump.
Fortinet and Arctic Wolf have been contacted by Infosecurity for comment but have not responded at the time of publication.
Photo credits: Lutsenko_Oleksandr/T. Schneider/Shutterstock
