Identity compromise is one of the top cyber threats to organizations, prompting cybersecurity professionals to encourage better identity management hygiene across industries.
According to the Identity Defined Security Alliance (IDSA), almost nine out of ten businesses (84%) have experienced an identity-related breach over the past year, and 78% have experienced direct business impacts from such incidents.
In 2021, IDSA established Identity Management Day alongside the National Cybersecurity Alliance (NCA) to raise awareness about this growing threat.
In 2024, IDSA chose to run its fourth Identity Management Day campaign on April 9 with the slogan #BeIdentitySmart.
“With 90% of organizations experiencing an identity-related breach in the last year, you must #BeIdentitySmart,” IDSA’s website states.
Identity-Based Incidents, a Growing Threat
The main reason identity-based incidents are growing is that identity compromise and identity theft are becoming threat actors’ preferred means to gain access to systems.
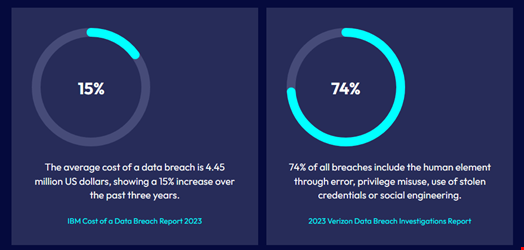
According to the Identity Theft Resource Center, identity compromise increased by 17% globally in 2023, while Sift’s Q3 2023 Digital Trust & Safety Index showed that account takeover attacks increased by 354% year-over-year that same year.
These numbers confirm previous CrowdStrike and IBM findings showing that identity compromise has risen to the top of malicious initial access methods in 2023 and 2024.
Speaking to Infosecurity during Black Hat USA 2023, Josh Lemos, GitLab’s CISO, explained the increased interest of threat actors for identity theft.
“As an industry, we’ve eventually gotten good at mitigating some of the threats, like ransomware – which still happens frequently but does not have the success it used to have. However, we’ve been lacking in identity and data security. These are where we should now focus our efforts,” he said.
According to Denis Dorval, vice president of International EMEA & APAC at JumpCloud, the momentum of identity theft can also be explained by the increasing complexity of today’s corporate IT networks.
“Modern IT environments are now incredibly diverse. As a result, security strategies have shifted from securing the physical network perimeter to defending a large, disparate attack surface, comprising devices, on-prem/cloud resources, operating systems, and networks. Although a distributed environment brings flexibility, it presents IT teams with an immense challenge and demands a completely different approach when it comes to identity management,” Dorval explained.
Identity Management Day 2024
In its awareness campaign in the run-up to Identity Management Day, IDSA insisted that “identity-related breaches are ubiquitous and preventable, whether you are an individual, a small business, a government agency or a Fortune 500 organization.”
To convey this message, the Association is running two different programs:
- The Identity Management Champion Program, for which individuals who have made identity management and security foundational to their mission can apply
- The Identity Management Awards, which rewards individuals and organizations that have made identity management and security an enabler to business operations while reducing risk over the past year
The Identity Management Awards winners will be announced on April 9 during IDSA’s Virtual Identity Management Day Conference.
JumpCloud’s Dorval commented: “Despite large-scale cyberattacks dominating the headlines and the growing emphasis on security in the boardroom, instilling good cyber hygiene into an organization's culture remains a challenge. Identity Management Day on April 9 aims to raise awareness about the dangers of casually or improperly managing and securing digital identities.“
James Dyer, a threat intelligence lead at Egress, added that advancements in cyber surveillance and the broader adoption of artificial intelligence (AI) tools have heightened the threat to digital identities.
“The art of cyber surveillance has advanced, with cybergangs employing open-source intelligence (OSINT) to create comprehensive profiles of their targets. This can be a deep dive into a target’s social media to understand their job role, social connections, and even personal interests, with the intention of creating hyper-personalized phishing emails that persuade recipients to reveal sensitive information or transfer funds,” Dyer said.
“The introduction of AI tools and chatbots has slashed the time it takes from data reconnaissance to full-blown attack. AI is enabling the automation and acceleration of data analysis, to quickly tailor phishing emails with convincing personalization,” he concluded.
Actionable Steps to #BeIdentitySmart
The IDSA also provides a list of actionable steps business professionals can take to improve their organization’s identity management posture.
These recommendations are divided into three groups: advice for security leaders, security practitioners and individual employees or consumers.
Recommendations to Security leaders include:
- Discuss the risk of failure to address identity security vulnerabilities with your board
- Prioritize identity as a top priority in your security program
- Think of identity as the first line of your cybersecurity defense.
- Make sure your identity foundation is solid by eliminating technical debt
- Create a ‘Beidentitysmart’ culture in your organization and speak often about best practices and their importance
Recommendations to security practitioners include:
- Prioritize identity management vulnerability assessments and closing security gaps
- Get to know what you have, what’s sensitive and protect it
- Apply the same identity concepts and processes across all types: employee, third party, customer/consumer and non-human
- Automate, automate, automate
- Focus on security outcomes and prioritize the gaps
Recommendations to individual employees and consumers include:
- Practice good identity hygiene, i.e. never share or reuse passwords and create strong passwords
- Recognize and report phishing
- Keep your software up to date
- Enable multi-factor authentication
- Use a password manager
