MuddyWater, an Iranian threat group, has recently started using a new, tailor-made backdoor to attack IT systems in the Middle East, according to threat intelligence firms Check Point and Sekoia.
In the past, MuddyWater primarily compromised systems using legitimate remote management tools such as Atera Agent, Screen Connect, Tactical RMM, or SimpleHelp.
The advanced persistent threat (APT) group’s typical kill chain started with a phishing campaign spread from compromised organizational email accounts, which led to the unauthorized deployment of these legitimate tools to control the victim’s devices.
Recently, MuddyWater shifted away from this approach and started deploying a custom backdoor, Check Point and Sekoia revealed on July 15, 2024.
Shift in MuddyWater’s Approach
MuddyWater is an APT group affiliated with Iran’s Ministry of Intelligence and Security (MOIS), which has been active since at least 2017.
It has engaged in widespread phishing campaigns targeting the Middle East, with a particular focus on Israel.
Since the Hamas attack on Israel in October 2023 and the beginning of the Hamas-Israel war, the group has significantly increased its activity.
On June 9, 2024, a report by cybersecurity company ClearSky on a new MuddyWater campaign led Sekoia to realize that the threat actor was using a new, undocumented tool.
Sekoia named this tool MuddyRot.
Check Point Research identified the same shift and dubbed the new tool BugSleep.
Decoding MuddyRot/BugSleep’s Functioning
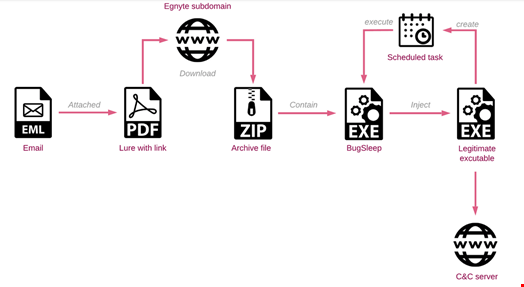
MuddyRot/BugSleep is an x64 implant developed in C that executes the threat actors’ commands and transfers files between the compromised machine and the command and control (C2) server.
It includes several capabilities such as reverse shell, persistence and the possibility for the operators to download and upload files from/to the compromised workstation.
The typical infection chain involves an Egnyte abuse. Egnyte is a secure file-sharing platform that allows employees and companies to share files via a web browser.
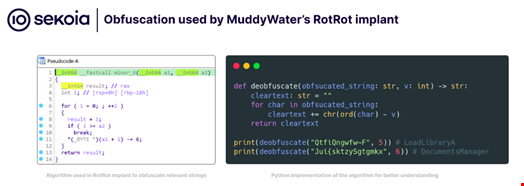
Upon execution, the malware performs standard tasks, such as deobfuscating strings, loading necessary functions from a dynamic application programmable interface (API), and creating a mutex.
All relevant strings, such as the malware configuration, file paths, and imported methods, are obfuscated using several standard obfuscating techniques, such as dynamic import loading.
Increased Scrutiny on Remote Monitoring Tools
The backdoor has primarily been used to infect the IT systems of Israeli organizations, although some campaigns targeted entities in Turkey, Saudi Arabia, India, and Portugal.
It is currently in development, with threat actors continuously improving its functionality and addressing bugs.
Sekoia threat researchers said this is not the first time MuddyWater has been observed using its own implant. The threat group crafted Powershell-coded first-stage backdoors before using legitimate remote monitoring tools.
The increased scrutiny of remote monitoring and management tools by security vendors following their increased use by malicious threat actors has influenced this change, Sekoia noted.
“Maybe one of its targets prevented Atera execution on its own network, so MuddyWater operators had to change for something more custom,” they added.
