Leicester City Council has confirmed that confidential data has been published online by a “known ransomware group” following a cyber incident that was identified on March 7.
The UK local authority said on April 3 that around 25 documents have been leaked, including rent statements, applications to purchase council housing and personal identification documents such as passport information.
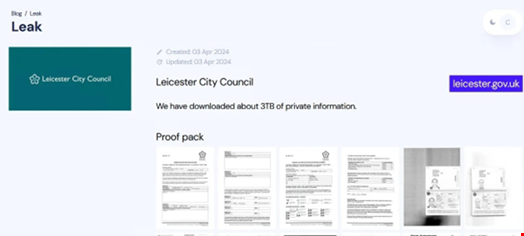
The attack was reportedly perpetrated by the Inc Ransom group, who claimed to have stolen 3TB of data from Leicester City Council.
The group also included a ‘proof pack’ in a post on its data leak site, which included various sensitive documents, including individuals’ passports and bank statements.
The data breach comes after Inc released patient clinical data it accessed from NHS Dumfries and March 27, 2024, following an attack on the Scottish NHS Trust earlier in the month. The ransomware group is known to have attacked a number of government, education and healthcare organizations
Leicester Council Cyber-Attack Incident Has Major Impact on Residents
In a statement, Richard Sword, Leicester City Council's strategic director of city developments and neighbourhoods, said the local authority is in the process of trying to contact all the individuals that have been affected by the breach.
He added that “it is very possible” that other documents have been extracted from the Council’s systems, although this is unconfirmed at this stage.
“We realize this will cause anxiety for those affected, and want to apologise for any distress caused,” stated Sword.
Leicester City Council is warning staff and the public to be on their guard for any attempt to access their systems or approaches from anyone claiming to be in possession of data relating to them. The Council has urged people to report any suspicious activity of this nature.
Stephen Robinson, Senior Threat Intelligence Analyst at WithSecure, believes Council employees and residents are exposed to sophisticated social engineering attacks.
“With the type of data stolen, a cyber attacker could craft extremely plausible, targeted phishing emails, texts and phone calls,” he explained.
The Council also confirmed it is working with Leicestershire Police and the National Cyber Security Centre (NCSC) as part of the ongoing investigation into the incident, and has notified the Information Commissioner’s Office of the breach.
Sword said, “As this is a live investigation we are not able to comment in further detail, but will continue to give updates when we have news to share.”
Council IT systems and phone lines were shut down in response to the incident on March 7, which severely disrupted citizens’ access to vital public services, including waste and recycling, school admissions, birth registration appointments and licensing.
On March 28, the city council confirmed that most of its main service portals and phone lines were operating as normal.
Inc Ransom a Prolific Ransomware Actor
Rebecca Moody, Head of Research and Data at Comparitech, noted that Inc is known for its double-extortion technique of encrypting systems and stealing data, providing it with two avenues to make money from incidents.
“If Inc is responsible for this attack, its recent posting suggests negotiations with Leicester City have so far failed so it's increasing the pressure to try and secure a payment. Failing that, it'll look to sell the data on the dark web,” she commented.
Oliver Spence, CEO of Cybaverse, said Inc would understand it is unlikely to extract ransom payments from public sector bodies, given the UK government’s opposition to making such payments. Therefore, it may have other motivations for targeting such organizations.
“This could suggest the gang is motivated by damage, rather than money, which means more public bodies could be on its target list,” he warned.
Inc has substantially increased its activities in 2024, claiming around 30 attacks so far this year.
WithSecure’s Robinson noted that 30% of their attacks have targeted the healthcare sector, which suggests they are primarily picking out vulnerable organizations that hold sensitive, private data.
“They use standard methods for the ransomware industry at this time, abusing legitimate tools and services for their attacks, and performing multi-point extortion, i.e. stealing data, as well as encrypting or wiping it on the local network,” explained Robinson.
Public Sector a Big Target for Ransomware Groups
Multiple local authorities in the UK, as well as regional government bodies in other countries such as the US, have been hit by ransomware attacks in recent years, causing significant disruption to vital public services.
Moody said there is no sign this activity is slowing, with 36 other attacks on government organizations around the world recorded so far in 2024.
“According to our data, the average ransom demand on government entities this year is $2.1m,” noted Moody.
In 2022, the UK government unveiled a new cybersecurity strategy designed to protect essential public sector services from being shut down by hostile threat actors.
Robinson said there are a range of methods local councils should use to enhance their cyber resilience, even amid financial pressures.
“Cost effective methods we advise all councils to implement include regular risk assessments, rigorous patching schedules, and fostering a strong cybersecurity culture supported by clear security policies,” he stated.
